Adopting Zero Trust Architecture in Data Engineering: Implementing Secure, Trustless Systems for Modern Data Security
Author(s): Abhijit Joshi
Abstract
The ever-evolving landscape of data engineering necessitates robust security measures to protect sensitive information in distributed environments. Traditional security paradigms, which rely heavily on perimeter defenses, are increasingly inadequate against sophisticated cyber threats. Zero Trust Architecture (ZTA) emerges as a pivotal strategy, advocating the principle of "never trust, always verify." This paper delves into the implementation of ZTA within data engineering, outlining its core principles, significance in modern data security, and practical applications to safeguard data integrity and confidentiality. Through detailed methodologies, algorithms, and visual representations, we explore how ZTA can transform data security practices, ensuring resilient protection against a myriad of cyber threats.
Introduction
In recent years, the paradigm of data security has undergone a significant transformation. With the exponential growth of data and the increasing complexity of cyber threats, traditional perimeter- based security models have proven inadequate. The rise of cloud computing, mobile devices, and remote work environments has further exacerbated these challenges, necessitating a more robust and dynamic security approach. Zero Trust Architecture (ZTA) offers a revolutionary framework that fundamentally redefines security principles, emphasizing the need for strict identity verification, granular access control, and continuous monitoring of all network activities.
The Evolution of Security Paradigms
Historically, security models have operated on the assumption that threats originate outside the network perimeter. Consequently, robust defenses were erected at the network boundaries, with minimal security measures within the network. This approach, while effective against external threats, fails to address insider threats and sophisticated attacks that penetrate the perimeter. As organizations increasingly adopt cloud services, mobile applications, and decentralized workflows, the traditional perimeter becomes nebulous and indefensible.
Introducing Zero Trust Architecture
Zero Trust Architecture (ZTA) challenges the conventional security paradigm by asserting that threats can exist both outside and inside the network. It operates on the principle that no entity, whether inside or outside the network, should be inherently trusted. Instead, every access request must be authenticated, authorized, and continuously validated based on predefined policies. This approach significantly mitigates the risk of unauthorized access and data breaches.
Relevance to Data Engineering
Data engineering plays a critical role in managing, processing, and securing vast amounts of data across various platforms and environments. As data becomes a strategic asset, ensuring its security and integrity is paramount. Implementing ZTA within data engineering frameworks provides a robust mechanism to protect sensitive data, maintain compliance with regulatory requirements, and build resilient data architectures. This paper explores the intricacies of ZTA in the context of data engineering, offering practical insights and technical methodologies for effective implementation.
Problem Statement
The traditional security models, which rely heavily on securing the network perimeter, are no longer sufficient in the face of modern cybersecurity threats. In a typical data engineering environment, data flows through various stages, including ingestion, storage, processing, and dissemination. Each stage presents unique vulnerabilities that can be exploited by malicious actors. The increasing adoption of cloud services, IoT devices, and remote work further complicates the security landscape, making it difficult to establish a clear perimeter.
Key Challenges in Traditional Security Models
- Insider Threats: Employees or contractors with legitimate access can intentionally or unintentionally compromise data Traditional models often lack the granularity to detect and prevent such threats effectively.
- Perimeter Breach: Once an attacker breaches the perimeter, they can move laterally within the network with minimal resistance, accessing sensitive data and critical
- Lack of Continuous Monitoring: Traditional security models rely on periodic checks and static defenses, which are inadequate against dynamic and sophisticated cyber
- Complexity of Distributed Environments: Modern data environments are highly distributed, spanning on-premises data centers, cloud platforms, and edge devices. Securing such a fragmented landscape with a perimeter-based approach is inherently flawed.
- Compliance and Regulatory Requirements: Data privacy regulations such as GDPR and CCPA impose stringent requirements on data Traditional security models struggle to meet these evolving standards, risking compliance violations and hefty penalties.
Specific Issues in Data Engineering
- Data Access Control: Ensuring that only authorized individuals and systems have access to specific data sets is Traditional models often grant excessive permissions, increasing the risk of data breaches.
- Data Integrity: Protecting data from unauthorized modification is essential for maintaining its accuracy and Traditional models may not provide the necessary mechanisms to verify data integrity at each stage of the data lifecycle.
- Data Confidentiality: Sensitive data must be protected from unauthorized Traditional models often rely on encryption at rest and in transit but may lack the comprehensive approach required for end-to-end data confidentiality.
- Scalability: As data volumes grow and environments become more complex, traditional security models struggle to scale effectively without compromising performance or
- Operational Overhead: Managing and maintaining perimeter-based defenses in a distributed environment can be resource-intensive and prone to misconfigurations, leading to potential security
The Imperative for Zero Trust Architecture
Zero Trust Architecture addresses these challenges by fundamentally rethinking security principles. By assuming that threats can exist both inside and outside the network, ZTA requires strict verification of every access request. This approach significantly enhances security by:
- Enforcing granular access controls based on the principle of least privilege, ensuring that users and systems have only the permissions they need.
- Implementing continuous monitoring and real-time analytics to detect and respond to threats swiftly.
- Utilizing multi-factor authentication (MFA) and strong identity verification mechanisms to ensure that access requests are legitimate.
- Applying micro-segmentation to limit lateral movement within the network, containing potential breaches.
- Ensuring end-to-end encryption and data integrity checks at each stage of the data lifecycle.
The adoption of ZTA in data engineering can significantly bolster security, ensuring that data remains protected in an increasingly complex and hostile cyber environment. This paper aims to provide a comprehensive guide for implementing ZTA within data engineering frameworks, offering detailed methodologies, practical solutions, and real-world examples.
Solution
Implementing Zero Trust Architecture (ZTA) within data engineering frameworks involves a multi-faceted approach that encompasses identity and access management, network security, data protection, and continuous monitoring. The solution requires a combination of advanced technologies, stringent policies, and best practices to create a robust security posture.
Core Components of Zero Trust Architecture Identity and Access Management (IAM)
- Strong Authentication: Implement multi-factor authentication (MFA) to ensure that users are who they claim to be. This includes biometric verification, one-time passwords (OTPs), and hardware tokens.
- Granular Access Controls: Employ the principle of least privilege, granting users and systems only the permissions necessary for their Role-based access control (RBAC) and attribute-based access control (ABAC) are critical mechanisms.
- Identity Federation: Utilize federated identity management to streamline authentication across multiple domains and platforms.
Network Security
- Micro-Segmentation: Divide the network into smaller, isolated segments to limit lateral movement by potential Each segment is protected with its own access controls and security policies.
- Software-Defined Perimeter (SDP): Use SDP to create dynamically provisioned, encrypted tunnels between users and resources, effectively concealing the network infrastructure from unauthorized access.
- Zero Trust Network Access (ZTNA): Implement ZTNA solutions to enforce continuous verification of user and device trustworthiness before granting access to applications and data.
Data Protection
- Encryption: Ensure that data is encrypted both at rest and in transit using strong cryptographic Implement end-to-end encryption to protect data throughout its lifecycle.
- Data Integrity: Utilize cryptographic hash functions and digital signatures to verify data Implement version control and immutability for critical data sets.
- Data Masking and Tokenization: Apply data masking and tokenization techniques to protect sensitive data elements, ensuring that unauthorized users cannot access or infer the actual data.
Continuous Monitoring and Analytics
- Security Information and Event Management (SIEM): Deploy SIEM systems to collect, analyze, and correlate security events from various sources in real-time.
- Behavioral Analytics: Use machine learning algorithms to establish baselines of normal behavior and detect anomalies indicative of potential threats.
- Automated Incident Response: Implement automated response mechanisms to swiftly contain and mitigate threats. This includes automated quarantine of compromised devices and revocation of suspicious user sessions.
Detailed Methodologies and Algorithms
Identity and Access Management (IAM)
Algorithm: Multi-Factor Authentication (MFA)
Pseudocode:
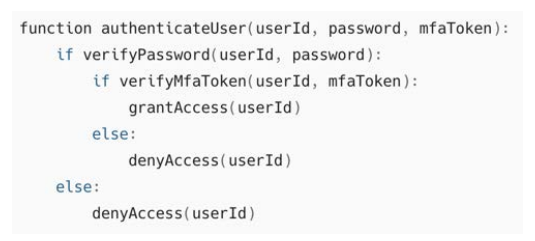
Explanation: The MFA algorithm verifies the user's password and an additional authentication factor (e.g., an OTP or biometric token) before granting access. This ensures that even if the password is compromised, unauthorized access is prevented.
Network Security Algorithm:
Micro-Segmentation
Pseudocode:
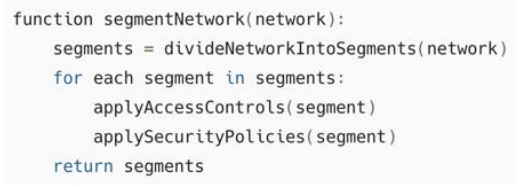
Explanation: The micro-segmentation algorithm divides the network into smaller segments and applies specific access controls and security policies to each segment. This limits the potential damage of a breach by containing the attack within a segment.
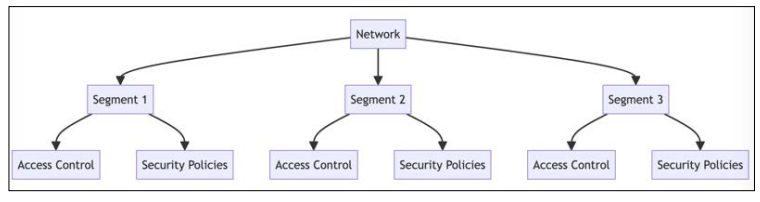
Network Segmentation Diagram
Explanation: The diagram illustrates how the network is divided into smaller segments, each protected with its own access controls and security policies. This approach limits lateral movement and contains potential breaches.
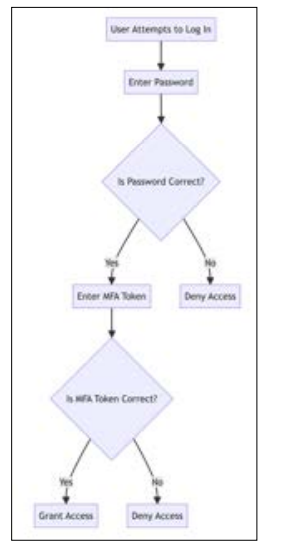
MFA Workflow
Explanation: The workflow chart depicts the multi-factor authentication process, highlighting the steps involved in verifying the user's identity through multiple factors before granting access.
Uses
Implementing Zero Trust Architecture (ZTA) in data engineering offers numerous practical applications across various stages of the data lifecycle. These use cases demonstrate the versatility and effectiveness of ZTA in enhancing data security, integrity, and compliance in distributed environments.
Data Ingestion
During data ingestion, ZTA ensures that only authenticated and authorized entities can introduce data into the system. This is particularly important in scenarios where data is sourced from multiple locations, including IoT devices, cloud services, and external partners.
- Access Control: Apply role-based access control (RBAC) and attribute-based access control (ABAC) to restrict data ingestion to authorized users and systems. This prevents unauthorized data sources from injecting malicious or unverified data into the pipeline.
- Encryption: Use encryption protocols such as TLS to secure data in transit during ingestion. This protects data from interception and tampering.
Data Storage
ZTA enhances the security of data storage by ensuring that only authorized users and systems can access stored data. This is crucial for maintaining data confidentiality and integrity in cloud and on-premises storage solutions.
- Encrypted Storage: Store data in encrypted formats using strong cryptographic algorithms such as AES-256. This ensures that even if storage systems are compromised, the data remains unreadable without the decryption keys.
- AccessControls: Implement fine-grained access controls to ensure that users and systems have the minimum necessary permissions to perform their tasks. This reduces the risk of unauthorized data access.
Data Processing
Data processing stages involve transforming, analyzing, and managing data. ZTA ensures that processing tasks are performed securely by authenticated and authorized entities, maintaining data integrity and preventing unauthorized modifications.
- Authenticated Processing Nodes: Require processing nodes to authenticate themselves before accessing data. This prevents unauthorized nodes from participating in data processing worlflows.
- Micro-Segmentation: Use micro-segmentation to isolate processing tasks into secure segments. This limits the potential impact of a compromised node, preventing it from affecting other parts of the network.
Data Dissemination
Data dissemination involves distributing processed data to various consumers, including applications, users, and external systems. ZTA ensures that only authorized recipients can access the disseminated data, maintaining data confidentiality and compliance with regulatory requirements.
- End-to-End Encryption: Implement end-to-end encryption to protect data during dissemination. This ensures that data remains secure from the point of origin to the final recipient.
- Continuous Monitoring: Monitor data dissemination activities in real-time to detect and respond to anomalies. This includes tracking access patterns and flagging suspicious behavior for further investigation.
Compliance and Regulatory Requirements
ZTA helps organizations comply with stringent data protection regulations such as GDPR, CCPA, and HIPAA by enforcing robust access controls, continuous monitoring, and comprehensive data protection measures.
- Audit Trails: Maintain detailed audit trails of all access and activity within the data engineering environment. This supports regulatory compliance by providing verifiable records of data handling practices.
- Policy Enforcement: Use policy-based access controls to ensure that data access and processing activities comply with regulatory requirements. This includes implementing data masking, anonymization, and other privacy-enhancing techniques.
Real-World Example: Financial Services
In the financial services sector, implementing ZTA can significantly enhance the security of sensitive financial data. By enforcing strict access controls and continuous monitoring, financial institutions can protect customer data from unauthorized access and ensure compliance with regulatory standards.
- Secure Data Transfers: Ensure that financial transactions and sensitive data transfers are encrypted and authenticated, preventing interception and fraud.
- Fraud Detection: Use behavioral analytics to detect anomalies in transaction patterns, flagging potential fraud attempts for further investigation.
Real-World Example: Healthcare
In healthcare, ZTA can protect patient data from unauthorized access and ensure compliance with HIPAA regulations. By securing data at every stage, from patient intake to electronic health record (EHR) storage, ZTA helps maintain patient privacy and data integrity.
Patient Data Access: Implement strict access controls to ensure that only authorized healthcare providers can access patient records. Use multi-factor authentication to verify identities.
TelemedicineSecurity: Secure telemedicine sessions using end-to-end encryption and authenticated access, ensuring that patient consultations remain confidential.
Graph: Data Flow with Zero Trust Architecture
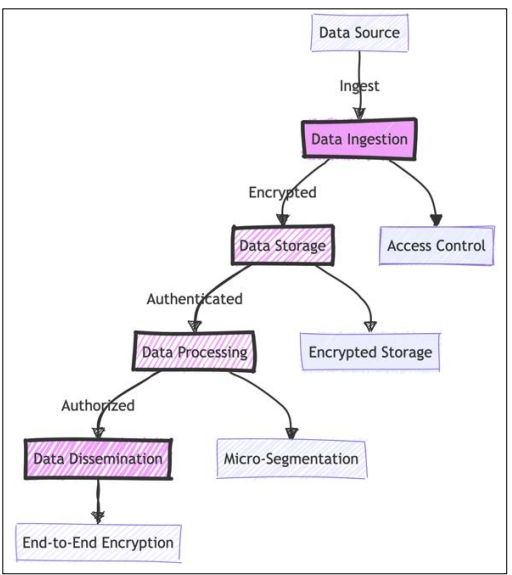
Explanation: The diagram illustrates the flow of data through various stages of the data lifecycle, highlighting the application of Zero Trust principles such as access control, encryption, and micro-segmentation. Each stage is secured to ensure that data remains protected from unauthorized access and tampering.
Impact
Adopting Zero Trust Architecture (ZTA) within data engineering has a profound impact on the overall security posture of organizations. This section explores the benefits and implications of implementing ZTA, highlighting its effectiveness in mitigating risks, enhancing compliance, and fostering a culture of continuous security improvement.
Enhanced Security Posture
- Reduction in Attack Surface: By enforcing the principle of least privilege and micro-segmentation, ZTA significantly reduces the attack surface. Each user, device, and application only has access to the resources necessary for their function, minimizing potential entry points for attackers.
- Improved Threat Detection and Response: Continuous monitoring and real-time analytics enable early detection of anomalies and potential threats. Automated incident response mechanisms ensure swift action to contain and mitigate security incidents, reducing the potential impact of breaches.
- Protection Against Insider Threats: ZTA's stringent access controls and continuous verification mechanisms are effective in mitigating insider threats. By ensuring that every access request is authenticated and authorized, the risk of malicious or negligent actions by insiders is minimized.
Compliance and Regulatory Benefits
- Meeting Regulatory Requirements: ZTA helps organizations comply with data protection regulations such as GDPR, CCPA, and HIPAA by enforcing robust access controls, maintaining detailed audit trails, and implementing comprehensive data protection measures. This reduces the risk of non-compliance and associated penalties.
- Enhanced Data Privacy: By implementing data masking, encryption, and anonymization techniques, ZTA ensures that sensitive data is protected throughout its lifecycle. This is crucial for maintaining data privacy and meeting regulatory standards for data protection.
- Audit and Accountability: Detailed logging and audit trails provide verifiable records of data access and handling This supports regulatory compliance and enables organizations to demonstrate their commitment to data security during audits.
Operational Efficiency
- StreamlinedAccessManagement: By centralizing identity and access management (IAM) and leveraging identity federation, ZTA simplifies the process of managing user identities and access permissions across multiple platforms and environments. This reduces administrative overhead and the risk of misconfigurations.
- Scalable Security: ZTA's principles are adaptable to a wide range of environments, from small organizations to large enterprises with complex, distributed infrastructures. This scalability ensures that security measures can grow with the organization without compromising effectiveness.
- Reduced Operational Risk: By continuously monitoring and verifying access requests, ZTA reduces the risk of security incidents caused by human error or This leads to more stable and secure operational environments.
Business Continuity and Resilience
- ResilientDataArchitectures: ZTA enhances the resilience of data architectures by ensuring that security measures are integrated at every stage of the data lifecycle. This reduces the risk of data breaches and ensures that data remains protected even in the event of a security incident.
- Minimized Downtime: Automated incident response and containment mechanisms help minimize the downtime associated with security incidents. This ensures that critical business operations can continue with minimal disruption, preserving business continuity.
- Increased Customer Trust: By demonstrating a commitment to robust data security practices, organizations can enhance customer trust and This is particularly important in ndustries where data privacy and security are paramount, such as finance and healthcare.
Real-World Example: Technology Sector
In the technology sector, adopting ZTA can significantly enhance the security of software development and deployment processes. By ensuring that only authenticated and authorized developers have access to code repositories and deployment pipelines, organizations can reduce the risk of code tampering and unauthorized changes.
Secure Development Environments: Implementing ZTA in development environments ensures that only verified developers can access sensitive codebases. This protects intellectual property and reduces the risk of introducing vulnerabilities through unauthorized changes.
Continuous Security Integration: By integrating continuous monitoring and threat detection into the development pipeline, organizations can identify and address security issues early in the development lifecycle. This leads to more secure software releases and reduced risk of post-deployment vulnerabilities.
Scope
The scope of adopting Zero Trust Architecture (ZTA) in data engineering is extensive, covering a wide range of applications, industries, and technological environments. This section provides a brief overview of the scope, highlighting key areas where ZTA can be implemented to enhance data security and operational efficiency.
Broad Applicability
- Industries: ZTA is applicable across various industries, including finance, healthcare, technology, government, and Each industry benefits from ZTA's robust security measures tailored to protect sensitive data and ensure compliance with industry-specific regulations.
- Technological Environments: ZTA can be implemented in cloud, on-premises, and hybrid environments. It is particularly effective in securing distributed systems, Internet of Things (IoT) devices, and mobile applications.
- Organizational Sizes: ZTA is scalable and can be adapted to suit organizations of all sizes, from small businesses to large enterprises with complex infrastructures.
Key Areas of Implementation
- Data Lifecycle Stages: ZTA can be integrated at various stages of the data lifecycle, including data ingestion, storage, processing, and This ensures comprehensive protection of data from the point of creation to its final use.
- Access Management: By centralizing identity and access management (IAM), ZTA streamlines the management of user identities and access permissions across multiple platforms, enhancing security and operational efficiency.
- Compliance and Auditing: ZTA supports compliance with data protection regulations by enforcing robust access controls, maintaining detailed audit trails, and implementing comprehensive data protection measures.
Challenges and Considerations
- Implementation Complexity: Adopting ZTA requires careful planning and execution. Organizations must assess their existing infrastructure, identify potential gaps, and develop a comprehensive implementation strategy.
- Cultural Shift: Transitioning to a Zero Trust model involves a cultural shift within the Employees and stakeholders must be educated about the importance of continuous verification and strict access controls.
- Technological Integration: Integrating ZTA with existing systems and workflows may require significant technological Organizations must ensure compatibility and interoperability with current technologies.
Conclusion
Zero Trust Architecture (ZTA) represents a paradigm shift in data security, moving away from traditional perimeter-based defenses to a model of continuous verification and strict access control. By implementing ZTA within data engineering frameworks, organizations can significantly enhance their security posture, reduce the risk of data breaches, and ensure compliance with regulatory requirements.
ZTA's principles of "never trust, always verify" and "assume breach" are critical in today's complex and distributed technological environments. By enforcing granular access controls, continuous monitoring, and end-to-end encryption, ZTA provides a robust framework for protecting sensitive data throughout its lifecycle.
The practical applications and real-world examples discussed in this paper demonstrate the versatility and effectiveness of ZTA in various industries and technological environments. As cyber threats continue to evolve, adopting Zero Trust Architecture will be essential for organizations aiming to secure their data and maintain operational resilience [1-11].
Future Research Area
The field of Zero Trust Architecture is continually evolving, with ongoing research and development focused on enhancing its principles and methodologies. Future research areas include:
- Artificial Intelligence and Machine Learning: Integrating AI and ML algorithms to enhance threat detection, automate incident response, and continuously refine access controls based on evolving security
- Quantum-Resistant Encryption: Developing and implementing encryption algorithms resistant to quantum computing attacks, ensuring long-term data security in the face of emerging technological threats.
- IoT Security: Extending ZTA principles to secure IoT devices and networks, addressing the unique challenges of managing and protecting vast numbers of connected devices.
- Policy-Based Access Control (PBAC): Advancing PBAC frameworks to provide more dynamic and context-aware access control mechanisms, enhancing the flexibility and effectiveness of ZTA.
- Interoperability Standards: Establishing interoperability standards for ZTA solutions, ensuring seamless integration across diverse platforms and environments.
By exploring these future research areas, the security community can continue to refine and expand the capabilities of Zero Trust Architecture, ensuring its relevance and effectiveness in the face of evolving cyber threats.
References
- Rose SW, Borchert O, Mitchell S, Connelly S (2020) Zero Trust Architecture. NIST Special Publication https://nvlpubs.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf.
- Bertino E (2021) Zero Trust Architecture: Does It Help? IEEE Security & Privacy 19: 95-96.
- Kindervag J (2012) Build Security into Your Network’s DNA: The Zero Trust Network Architecture. Forrester Research https://forrester.com/report/Build-Security-Into-Your-Networks-DNA-The-Zero-Trust-Network-Architecture/ RES57047 .
- Schneier B (2015) Secrets and Lies: Digital Security in a Networked World. Wiley https://onlinelibrary.wiley.com/doi/book/10.1002/9781119183631.
- Smith S, Marchesini (2008) The Craft of System Security. Addison-Wesley Professional https://www.amazon.in/Craft-System-Security-Sean-Smith-ebook/dp/B004X1D2SY .
- Saltzer J, Schroeder MD (1975) The Protection of Information in Computer Systems. Proceedings of the IEEE 63: 1278-
- Rescorla E (2000) SSL and TLS: Designing and Building Secure Systems. Addison-Wesley https://www.amazon.in/ SSL-TLS-Designing-Building-Systems/dp/0201615983.
- Kaufman C, Perlman R, Speciner M (2002) Network Security: Private Communication in a Public World. Prentice Hall https://amazon.in/Network-Security-Communication-Networking-Distributed/dp/0130460192 .
- Ristenpart T, Shacham H, Savage S (2009) Hey, You, Get Off of My Cloud: Exploring Information Leakage in Third-Party Compute Proceedings of the 16th ACM Conference on Computer and Communications Security 199-212.
- Somorovsky J (2016) Systematic Fuzzing and Testing of TLS ACM Transactions on Information and System Security https://wcventure.github.io/FuzzingPaper/Paper/CCS16_SystematicFuzzing.pdf.
- McDaniel P, McLaughlin S (2009) Security and Privacy Challenges in the Smart Grid. IEEE Security & Privacy 7: 75-77.
View PDF





