Author(s): Siva Karthik Devineni*, Brownmagnus Olivers and Mahidhar Mullapudi
Today, businesses are advancing their IT strategies to leverage cloud environments providing greater scalability and efficiency in the changing digital environment. This indicates that it will be the modernization of data and apps that will lead the way as enterprises try to adapt themselves to the change brought about by the cloud. Even though they are not intentionally constructing a new entry medium that may be readily stolen, information providers in both the public and commercial sectors are also facing critical challenges regarding data security. At the same time as it satisfies the requirements of commercial customers as well as those of public sector organizations, this article provides the many methods that may be used to build cloud computing systems that protect the data of customers, guaranteeing that it is kept private. Also included in this are the methods for safely transferring client information from servers housed in your office building to the cloud, as well as the best practices that are prevalent within a certain industry and particulars that are applicable exclusively to a particular sort of company activity.
The cloud is the driving force behind the seismic transformation happening in digital space. Businesses across all industries are moving their data and applications to the cloud because of the ubiquity, scalability, and cost savings offered by this technology. Many companies, both public and private, are worried about how to use the cloud's benefits while keeping sensitive information safe. Data modernization and the adoption of secure cloud practices are the subjects of this article's investigation. Services in both the public and private sectors may benefit from the secure cloud solutions discussed in this article.
Because of cloud computing, businesses that want to be more efficient, scalable, and agile must upgrade their data and applications. The mobile platform for these transformations, cloud computing lets organizations better their application designs and data management infrastructures using cutting-edge technologies. To ensure modernization success, security issues must be properly assessed. Organizations and governments adopting cloud services must protect sensitive data. Protecting sensitive government data requires following all encryption techniques and regulations.
Companies are rushing to modernize their data and applications for the cloud age. Cutting-edge technologies like AI and machine learning unleash scalability, agility, and power, not just new tools. This revolution revolves around data, the foundation of modern business. Legacy data systems may slow progress due to isolation and inactivity. Data modernization includes cloud-based, adaptive data platforms, pipeline consolidation, and robust data governance. Businesses may manage data in real time, get insights, and make informed choices [1,2].
Data-engagement applications are also changing. New methods like micro services and containerization are helping firms move away from monolithic systems. This technique allows component growth, shorter development cycles, and faster deployments [3,4]. Data and application modernization, however, is not an easy road to travel. Security must always take precedence during migration, which may be difficult in situations involving outdated systems. Nevertheless, the benefits are apparent. Updated applications may increase operational efficiency by 20-30% and save development and maintenance costs by 30-50%, according to studies.
One needs a plan to succeed. First, examine current infrastructure, set modernization goals, and choose a cloud platform. Containerization and micro services architecture may improve transitions. Modernizing cloud data and applications means leveraging information to alter companies, not simply upgrading technology. This digital symphony may help organizations become agile, creative, and sustainable. HIPAA, GDPR, and CMMCcomplicate business for commercial and governmental entities. The data governance, access controls and even the infrastructure choices are dependent on fully understanding these compliance requirements. For instance, healthcare organizations moving EHRs to the cloud should comply with HIPAA’s strict requirements for information protection and privacy [5].
Robust security protocols are the foundation of every successful cloud-based solution. Encrypting, both in transit and at rest protects data throughout its life cycle, with access controls and intrusion detection systems curbing the number of unauthorized accesses and sophisticated acts [6]. What is more, selecting a cloud provider featuring its deep security record as well as the model of shared responsibility makes it possible to secure entire cloud environment in collaboration with the chosen safe vendor on a joint basis [5].
Protecting data, applications, and infrastructure hosted in the cloud is the goal of cloud security, which is sometimes called cloud computing security. Data privacy, access control, and user and device authentication are all safeguarded by these safeguards. Regulatory data compliance is another area they help with. Protecting a company's data on the cloud against threats like viruses, hackers, and distributed denial of service (DDoS) assaults is the job of cloud security [7].
When it comes to private and government service delivery, cloud security measures are critical. Private clouds allow businesses to set up security measures that are specifically aligned with individual regulatory requirements, offering a highly specialized and dedicated cloud computing ecosystem for an organization with high security demands. This entails implementation of the best practices and controls to safeguard data against breaches and cyber threats while maintaining the highest standards in terms of data privacy and confidentiality. 8 This involves physical security, network segmentation and encryption for ensuring data availability and business continuity in private clouds [8].
Due to the widespread use of cloud computing, cloud security has become an essential concern for most enterprises. In light of this rapid uptake, Gartner has forecasted a 23.1% increase in the global market for public cloud services in 2021.
Cloud storage raises security, governance, and compliance concerns, which prevent IT departments from rushing to move more apps and data there. They are concerned that ever-evolving cyber threats or unintentional disclosures might compromise their company's intellectual property and extremely sensitive information.
Data and business information, including client orders, confidential design drawings, and financial records, must be safeguarded in the cloud. If you value your clients' confidence and want to keep the assets that give you an edge over your competitors, you must take every precaution to prevent data breaches and theft. Any business making the move to the cloud must prioritize cloud security due to its capacity to protect data and assets [7].
Although major cloud providers like AWS, Azure, and GCP provide numerous built-in security features and services, additional solutions from third parties are necessary to achieve enterprisegrade protection for cloud workloads against data breaches, targeted attacks, and other security issues [9].
Authentication: Organizational identity management (IAM) definitions may be easily updated with the help of groups and roles. The only assets and APIs that a group or role requires to perform properly should be allowed. Authentication is improved upon by extended privileges. IAM hygiene, which includes stringent password rules and permission time-outs, should not be forgotten.
Networks and Micro-Segments: Virtual Private Clouds (VPCs) on Amazon Web Services and Google Cloud Platform, as well as virtual networks (vNETs) on Microsoft Azure, may be used to separate mission-critical resources and applications from the rest of the cloud network provided by the provider. Apply fine-grained security controls at the gateways of subnets to micro-segment workloads. In hybrid designs, employ dedicated wide area network (WAN) connections to configure virtual networks, virtual devices, and public IP addresses with static user-defined routing.
and Software Updates: Where virtual servers are provisioned, manufacturers of cloud security solutions implement governance and compliance standards and templates uniformly. These vendors also inspect for configuration violations and automate remediation where feasible.
Located near micro services hosting workloads, this will optimize web application server traffic inspection and control, automatically adjust WAF rules to changing traffic behaviour, and more.
Securer Data Storage: Improved data security via multi-layer encryption, encrypted file sharing and communications, ongoing monitoring of compliance risks, and appropriate hygiene practices for data storage resources, including the elimination of orphan resources and the detection of incorrectly configured buckets.
Real-time Threat Analytics Detecting and Remediating known and Undiscovered Threats: To contextualize the vast and varied streams of cloud-native logs, cloud security vendors intelligently cross-reference aggregated log data with internal and external sources like configuration and asset management systems, vulnerability scanners, and geolocation databases. Tools for visualizing and querying the threat environment are also provided, which helps with incident reaction times. In order to identify unknown dangers, forensics analysis is performed on the data gathered using AI-based anomaly detection algorithms. The risk profile of these threats is then determined. Reduced response times and, in certain cases, the activation of auto-remediation procedures are outcomes of real-time warnings on intrusions and policy breaches.
Regarding encryption protocols and standards, cloud security controls are a necessity to protect cloud environments from vulnerabilities and reduce the impact of malicious attacks [10]. Cloud security primarily involves encryption and compliance with encrypted protocols or standards is of vital importance if the business plans to store any sensitive data in the cloud. It is crucial to put in place strong encryption algorithms so that although someone with malicious intent gains access to the intercepted data, they would not be able to understand its content. To prevent risks of data breaches in cloud environments, it is standard practice to use Transport Layer Security (TLS) for the data in transit and encryption at rest protocol.
One security method that helps maintain privacy and authenticity is access control. Its primary function is to control the dissemination of data and other resources. What we mean by "access control" is the ability to specify which operations a certain user may execute on specific data. In order to ensure security, access control rules specify which users have authority. An access control model is used to establish these regulations. It safeguards data and resources from being shared without authorization. Furthermore, it protects information against cyber-terrorists, as well as internal assaults and exposure [11].
Cryptography or Encryption is a way to make a communication unintelligible to everyone save the intended recipient by encoding clever plain text into a scrambled message. You need an algorithm and a key to encrypt a message. Symmetric, or private key encryption, uses the same key for both sender and receiver, whereas asymmetric, or public key encryption uses separate keys. It safeguards sensitive data against authorized and unauthorized access [11].
For the most part the term "access control" refers to the process of authenticating a user before granting them permission to access data in order to complete a certain task. In the same way that you authorize someone to access a network using their username and password, you also authorize them to utilize resources after verifying that they have the proper authorization to do so. The question then becomes how to authorize a certain user to carry out their action. Here, we use access control [3]. As a formal concept, "access control matrix" originally referred to subjects, objects, and the process of controlling their access.
If we talk about governmental details, security requirements get even laughable. most governments have a low-risk tolerance in terms of the cloud security and information protection within their network infrastructure. It is argued that government standards should be adjustable to address new cyber threats, and large commercial cloud providers may not follow stringent regulations on data security [12]. A simple example is the Cloud Computing Security Requirements Guide (CCSRG) provided by U.S. Department of Defense DoD that gives security authorization protocols and demands for cloud services used both by agencies affiliated with DoD as well as those not related to this department. This guide describes the Security Model that DoD utilizes in reference to cloud computing and applies to cloud services provided by both the DoD and those from commercial Cloud Service Providers [13].
Protecting sensitive and classified information is often a function of government agencies, which must comply with compliance frameworks. An example of this would be the (FedRAMP) Federal Risk and Authorization Management Programme in the United States, which establishes a standardized procedure for the testing of cloud products' security, authorization, and continuous monitoring [14]. It is fundamentally essential for the government data security in cloud to understanding and alignment with such requirements of compliance.
Finally, cloud security for private and government services requires strong security measures, encryption protocols and compliance requirements to be in place to ensure that sensitive data is protected in the cloud. Private clouds provide customized security settings, while government bodies have a certain process of security authorization and requirements to be followed as stated in the Cloud Computing Security Requirements Guide released by the United States Department of If protection.
When implementing secure cloud-based solutions, there are several critical aspects that need to be addressed including privacy issues regarding data, the part played by IAM and secure development methods for any cloud applications.
As a result of the fact that several laws and compliance frameworks require the protection of personal and sensitive information, the protection of data privacy is an essential priority in this scenario. Cloud solutions are forced to include privacy-centric design principles [15]. This is the case as legislation like (GDPR) General Data Protection Regulation in Europe and (HIPAA) Health Insurance Portability and Accountability Act in US enforce strict requirements on how entities collect, process, or store personal information. These laws are meant to safeguard people’s privacy
IAM is an essential collection of rules, procedures, and technologies is referred to as [16]. This collection establishes the control mechanisms for which users have access to what resources in a cloud computing environment, and how those resources are used [17]. It ranges from the establishment and assignment of roles to a person or persons, just as dynamically adding, removing, or modifying responsibilities that individuals have inside some certain system. Identity and access management IAM comes into importance at resolving data privacy issues as well as specific requirements particular to the General Data Protection Regulation GDPR using an identity through access protection, governance authorization and authentication [18]. They also evolved to adapt within regulation-intensive environments, providing broad coverage of protection, threat visibility and risk mitigation [19].

Figure 1: Key Cloud Security Measure (IAM) Categorized by Their Focus
In addition, IAM provides a robust security layer while developing secure cloud applications by controlling access to the cloud-based resources it manages and restricts its activities besides monitoring what users have been doing to ensure they observed any laws in place pertaining industry operating procedures [16]. So, securing cloud-based solutions involves a careful selection and deployment of IAM to address data confidentiality concerns, meet statutory requirements and practices for secure applications development in the cloud.
Secure development practices for cloud applications are a necessary component in developing resilient and robust systems. Implementing such methods as DevSecOps makes security practices ingrained in every point of the development lifecycle so that security is not seen as something that can be tackled on later. It encompasses periodic security checks, code reviews and penetration testing for discovery and mitigation of vulnerabilities prior to deployment minimizing the occurrence of security events in cloud applications [20].
Moving sensitive information to the cloud has its own complications. Data classification and risk assessment should be used as key points, focusing on the data’s sensitivity and potential consequences of a leak based on the information [21]. DLP (Data Loss Prevention) provides protection from unauthorized data extraction, while extensive testing and validation guarantee the integrity and functionality of data after migration [22].
Cloud migration is also a set of challenges that needs very careful planning. The detailing will include data migration strategies, latency and performance concerns as well as ensuring business continuity throughout the process. Evaluating data migration strategies is an integral part of moving to the cloud. Organisations can make any of the multiple approaches, including “lift and shift”, re-platforming or re-architecting depending on such considerations as how complex are their applications already and what kind of cloud native integration they want to achieve [23].
The seemingly straightforward process of data transfer is anything but for companies that gather massive amounts of data on their customers, internal processes, company performance, etc. on a regular basis. The allocation of resources and tools, as well as the organization of the work process, are crucial steps in a migration strategy. To get the most out of your data transfer, it's important to plan ahead so you know exactly how to use your time, money, people, and tools [24].
Risk mitigation reduces project and business continuity risks. Risk reduction methods are part of a project plan. Risk minimization prevents dangers [25].
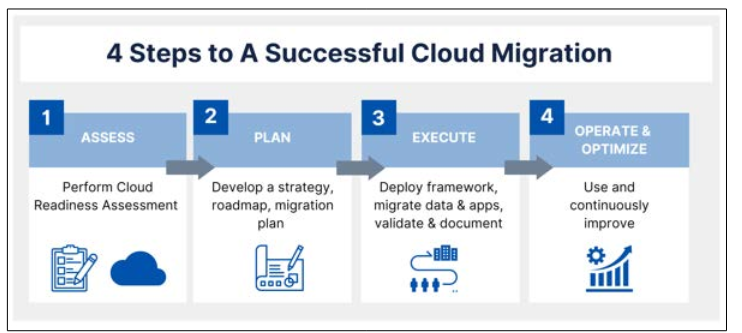
Figure 2: Steps to successful cloud migration [26].
Focus on risk management. In this quickly changing era, when we have numerous opportunities to design new items, features, and services, new hazards occur constantly, many of which are linked to or caused by digital technology. We need to know how to handle risks and be ready to face the consequences. Going back to the prior chapter, we discussed the ethics of new technologies. Envision a world where "risk assessment and management" are fundamental components of moral technology [27].
The greatest way to be ready for unanticipated occurrences that might slow down or even stop development is to practice risk management. An effective risk management program will first pinpoint the threat and then look at how it relates to other risks and the likelihood of their domino impact. Stakeholders may use a risk management method to find hazards, determine how bad they might be, and figure out how to fix them. Also, the most pressing risks are addressed with the utmost vigor via progressive risk management [28].
There are many upsides to anticipating and monitoring potential hazards in a business. Though it may seem like a setback at first, predicting possible hazards before they ever exist is really quite helpful for the future stakeholders. This is especially true when working on a project and discovering them. The engineers and builders of the system may better prepare for both possibilities and challenges if they can foresee potential hazards. The expenses of "fixes" discovered after the system is live may be significantly reduced if hazards are identified prior to deployment.
Carrying out a risk analysis entails calculating the probability of an adverse event. Discovering the probability is a crucial aspect of risk management. With the use of risk analysis, you may head off potential problems by dealing with unknowns and problems before they become liabilities. To assess potential dangers, most businesses use either quantitative or qualitative methods.
As its name suggests, quantitative risk analysis focuses on calculating an objective knowledge of the risks by making use of verifiable and evaluated data [29]. Expert opinion on the seriousness of a risk is the focus of qualitative risk analysis.
In qualitative risk analysis, casting doubt on the seriousness of potential outcomes is the main aim. That objective is graphically shown in the Risk Assessment Matrix that follows Figure. 3.
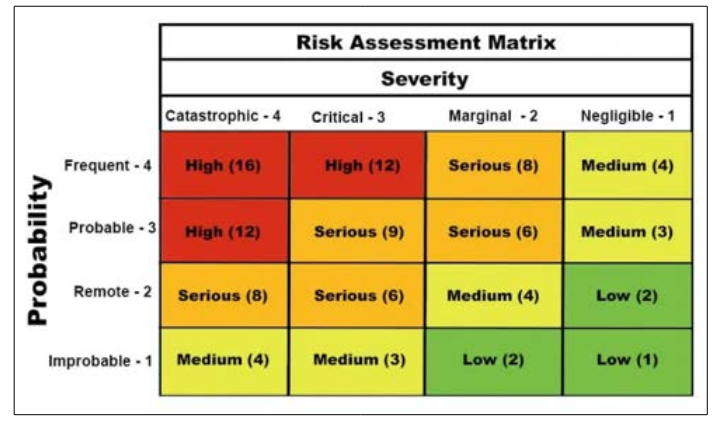
Figure 3: Risk assessment matrix illustrates qualitative risk analysis [29].
These problems, such as latency and performance concerns, may arise during cloud migration and have an impact on users’ experience and system functionality. So, organizations should evaluate and optimize network topologies, deploying content delivery networks (CDNs), as well as using edge computing when relevant to eliminate latency issues. On top of that, choosing cloud service providers with the global infrastructure can also help to enhance performance and lessen latency for users [30].
Continuation during migration is critical in order not to disrupt the business operations. This entails designing a comprehensive migration plan, performing rigorous testing to ensure that the moved objects behave as expected, and deploying fallback procedures in case of any unforeseen problems. Therefore, a phased migration approach should be identified, whereby certain components or services can be migrated gradually to manage risks and keep the business running without significant disruptions [31].
The healthcare industry is an example of the fact that secure cloud modernization is necessary. Hospitals are moving their EHRs to the cloud for better access and analytics but maintaining HIPAA compliance is still of utmost importance. Secure cloud solutions, coupled with strong data governance practices and access controls, help hospitals maximize the benefits of using the cloud without putting patient privacy at risk [32].
The financial sector also gains from cloud-based fraud detection platforms. These platforms analyse large-scale data sets in realtime to detect and prevent fraudulent transactions. However, one must be very careful about the customer’s data privacy. 25 Financial institutions can combat fraud effectively, while maintaining customer trust, by having secure cloud architecture coupled with data anonymization and granular access controls [33].
Observing cases of different industry sectors of the IT sector helps to understand the realities of data and application modernization in the cloud. Models of successful cloud migrations provide guidance for organizations pursuing similar paths. For instance, the story of Netflix explains how cloud migration can result in scalability and survivability as it can handle large workloads efficiently [26]. In the same way, migrating Capital One’s significant applications to the cloud demonstrates its potential for increased security and innovation [34].
Case Study: Mayo Clinic Migrating more than 10 petabytes of patient data to the cloud, Mayo Clinic enhanced accessibility for researchers and clinicians all while maintaining HIPAA compliance [35].
Lessons learned: protecting sensitive healthcare data is essential, and this requires rigorous data classification as well as granular access controls.
Case Study: Capital One: Engaging with a cloud-based approach at Capital One resulted in genuine real-time fraud identification, stopping more than $one billion worth of losses each year [36].
The lessons that were gained include that cloud-based analytics and machine learning are the driving forces behind proactive fraud prevention, but that solid security measures are absolutely necessary.
Case Study: The transfer to the cloud at Macy's made inventory management easier and resulted in improved consumer experiences [37].
Important life lessons: Although cloud-based technologies have the potential to improve supply chain visibility and improve the level of personalization of interactions with customers, concerns about data protection must be addressed.
Additionally, it is essential to gain knowledge from security breaches, which brings to light the fact that strong security policies are essential throughout the implementation of cloud computing. In 2017 year, the data breach that occurred at Equifax serves as a lesson, highlighting the need of implementing stringent security measures such as vulnerability assessments and timely patching to provide protection against unauthorized accesses to sensitive information stored in the cloud square [38].
The issues and solutions that are specific to industry are a further example of the complexity that is associated with cloud adoption. For instance, firms operating within the healthcare sector would have to deal with specific issues like following compliance standards such as HIPAA and reliably handling large amounts of sensitive patient information. There are available cloud solutions for healthcare such as Microsoft Azure that attempts to feel all these issues with a compliant and secure platform [39].
There are varied regulatory requirements for the protection of personal information in different sectors and the need to comply with regulations. Moreover, organizations should make sure that their cloud migration plan addresses these concerns and remains in compliance with the legally applicable requirements. This may involve the use of tools and procedures for monitoring compliance in terms of rules that is specific to sector [40].
Moving to a cloud infrastructure may be great in scalability and cost-efficiency; however, for an organization to enjoy these benefits, it must first build its cloud system thoughtfully. This may include selecting the correct cloud provider and delivery type (SaaS, PaaS, IaaS etc.) based on what the company requires as well as its budget [41].
All in all, a well-deployed plan of migrating to the cloud demands security attention and best practices to offer that smooth but secure transition period. An organization may be able to carry out effective migration of the cloud by learning from case studies and finding solutions for problems which are unique in their industry. This will enable the organization to benefit from enhanced efficiency, scalability, and cost savings.
The article concludes that cloud computing transforms data and application modernization and that security and technical innovation are interwoven. The lively digital world has led enterprises to cloud-based solutions for agility, scalability, and efficiency. However, business and government agencies must realize the benefits of cloud computing while safeguarding data security and confidentiality. The discussion focuses on encryption, data access locks, and compliance requirements that are associated with secure cloud computing in organizational settings that are both commercial and government based. Private clouds adhere to certain security requirements, while government systems are required to comply with stringent demands, such as the Cloud Computing Security Requirements Guide published by the United States Department of Defence. Due to ageing systems and security issues, data and application transformation is tough. Updated apps save money and boost efficiency. This strategic approach evaluates infrastructure, sets modernization targets, and chooses cloud platforms and methods [43].
Due to data privacy concerns, IAM frameworks and secure cloud apps are crucial. IAM helps comply with GDPR and HIPAA by delivering robust security features and a secure development environment. This report fully analyses cloud migration obstacles and best strategies. It emphasizes the necessity for data classification, risk assessment, and continuing testing following data transmission to ensure system integrity and prevent corruption. Case studies of cloud migration successes may provide blueprints and insights. Healthcare, banking, and retail case studies exist. The rise of cloud computing requires understanding of security issues, industry concerns, and solutions. This will help organizations embrace the cloud safely and easily, enabling them to reap its efficiency, scalability, and cost-effectiveness. Addressing industry-specific challenges and recognizing real scenarios would help businesses embrace the cloud.
