Author(s): Ravindar Reddy Gopireddy* and Akilnath Bodipudi
The effect of human behaviour in cyber security effort is gigantic. In this paper I am going to delve into the subject of human-centric cybersecurity, under two aspects: primarily inspecting the role one plays within cyber defense and ethical issues in cybersecurity. It emphasises the connection between cyber threats and human actions, education (or lack of it) as well as ethical concerns like privacy, surveillance and data protection. This holistic approach addresses the human element and ethical considerations to enhance cybersecurity strategies full stop.
Constant progress in technology has changed the world and cybersecurity is no exception to it. The focus on technology-based solutions in the traditional approaches often overlooks or gives very little importance to human behavior and ethical aspects. This paper proposes a human-centered security strategy against cyber attacks, taking into account that avatars are the easiest to destroy and most effective shield in terms of cybersecurity. We can better understand hacking by looking at humans and how they behave, their training, the ethics of cyber operations: all contributing profiles that make up more effective cybersecurity processes.
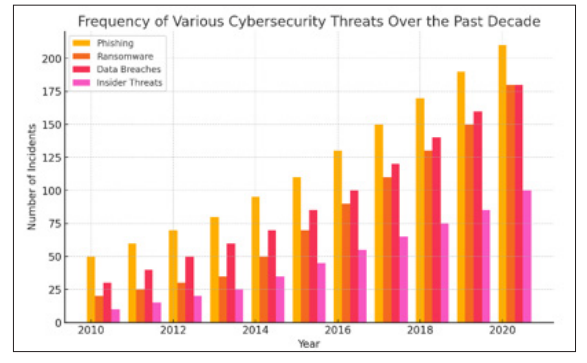
Figure 1: Frequency of Various Cybersecurity Threats Over the Past Decade
The bar chart displayed in Section 1 illustrates the frequency of various cybersecurity threats over the past decade, from 2010 to 2020. The chart categorizes threats into four main types: phishing attacks, ransomware attacks, data breaches, and insider threats.
Each category is represented by a distinct color, making it easy to differentiate between the types of threats.
Modern cybersecurity threats are too complex to address with only one discipline. However, human action creates vulnerabilities that technology alone cannot resolve. In this paper, we will discuss how human-centric cybersecurity may help to fill the void of specific technologies and frameworks by applying knowledge from psychology, sociology and ethics into security practices. It will also expose the importance that a trade-off has to be made between security measures and ethics so as not to undermine people's privacy under pretences of cybersecurity.
This is due to the fact that whether or not cybersecurity measures are implemented effectively has everything to do with human behavior - for we have seen time and again that people are truly the first line of defense when it comes to combating cyber threats. Human action and decision is still the number one driver of an organization security posture despite all advances in technology. For example, the human element in cyber defense is quite capable of determining that cognitive biases; emotional responses and levels of awareness can effectively dictate as well drive future cybersecurity outcomes. Tacking these human factors can enable organizations to build more resilient defenses alongside the technological solutions they have in place, and improve on their overall cybersecurity strategy.
Human behavior is inherently unpredictable and is often the most significant risk to cybersecurity. Regardless of the best intentions, malicious parties can use social engineering to exploit human psychology and enter the protected systems. As such, mitigating factors dependent on it might require a significant understanding of those behaviors, ranging from cognitive biases to emotional responses. Therefore, it is necessary to design the architectural defenses with those behaviors taken into account. It is essential to study how human biases factor into the decision-making process. Optimism bias is among the factors presented in H&S. Awareness programs should account for these biases since perception is the first step in the decision-making process. For instance, confirmation bias is the factor that cybersecurity training needs to utilize the most. Training programs should include affordable scenarios to make the participants decide to check interpretations actively. Recording this as a habit change can kill this bridge.

Figure 2: Flow Diagram - Relationship Between Human Behavior, Cybersecurity Threats, and Defense Mechanisms
Emotional Responses to Threats Emotional responses to work can range from feelings of fear and inadequacy to those of overconfidence. As such, the role of emotions as relevant responses to cybersecurity threats should not be overlooked. An awareness of the most frequent emotional triggers involved during cybersecurity attacks can assist developers in designing training aimed at ensuring the desired emotional response. Emotional intelligence is a crucial component of both information security and high productivity. Thus, safety training that focuses on promoting emotional intelligence can help employees gain emotional expertise and not succumb to panic during an incident. Simultaneously, organizations with supportive cultures can decrease the likelihood of anxiety experienced by staff, resulting in fewer emotionally triggered irrational decisions during cybersecurity discussions.
The importance of having sophisticated techniques is for cybersecurity to be efficient, and since there are millions of users who must have regular access to these devices or databases, it would make sense that employees receive proper training not only themselves but also the company as a whole. Cybersecurity centric human focuses on educating individuals to be able to understand and respond proactively when they face cyber threats. An informed and alert workforce requires routine, holistic training. That education should include - at a minimum - identifying phishing, safe browsing habits and sound password management to turn failure points into strong layers of defense.
Training programs continued on a regular basis to provide the knowledge and skills that individuals would need to recognize cyber threats. This includes recognizing phishing attempts, safe browsing habits and strong password management.
Phishing - is a classic example of the methods used by attackers to trick ordinary users into providing personal information. For example, training programs may also need to include simulated phishing attacks to improve the ability of employees in recognizing malicious emails and report them.
Realistic and diversified phishing simulation for differing styles of attacks (phishing, spear-phishing or whaling) These simulations, which are updated on a regular basis, help staff against the latest phishing attacks. Additionally, feedback and analysis following each simulation can allow employees to see where they went wrong in detecting these indicators as well what should have been discovered.
Cyber threats can easily be prevented with simple practices like safe browsing which includes staying away from dodgy websites and using secure connections. Training Guidelines: Train that these are the characteristics of how their device experience must behave; not just a point solution but to ensure they understand and practice safe online activity.
Training regarding the usage of these browser security features, i.e., employing HTTPS and possible dangers associated with downloading files from untrusted sources. In addition, make it clear to your employees that they should use the high-quality antivirus and ad-blocker. These safe internet habits can be honed by means of practical demonstrations and hands-on exercises.

Figure 3: Infographic - Safe Browsing Practices
The main source of all cybersecurity incidents today is human error, which includes misconfiguration, weak passwords and phishing simulations. Organizations can look at what has occurred in the past to determine general human errors and implement means of reducing these risks. This entails providing multi-factor authentication and creating an alert user base.
By looking back at previous cyber security incidents we can get a sense of what types of errors are by and large due to carelessness. This assessment can be used to direct the implementation of tailored training programmes and preventative actions.
The analysis of incidents should then delve deep into the root causes and contributing factors. Organizations can better develop prevention strategies when they understand the context and circumstances surrounding the human errors. It could mean changing policies, improving communication and strengthening technical controls to help people.
Using multi-factor authentication(MFA) is again another best practice where it adds an extra layer of security reducing the risk for breaches as even if passwords are compromised, unauthorized access protection remains. Promote the use of MFA (Multi Factor authentication) for all key systems to help reduce human-errors.
By enabling MFA, you improve security with two or more forms of authentication. This might be something they know (like a password), something they have (TAN/TOTP/hardware-token), or even what the user is, for example biometrical checks. Enterprises should instruct their employees on the value of MFA and how to best implement it in their lives.
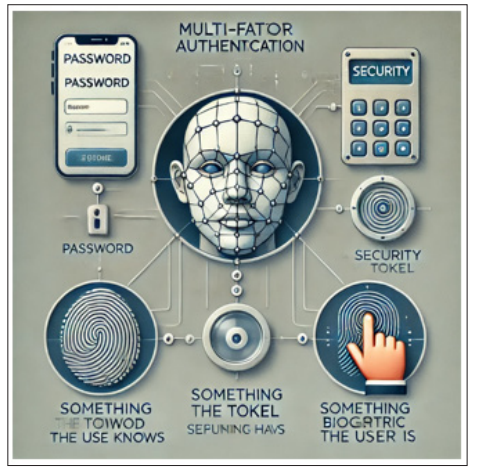
Figure 4: Diagram - Steps in Multi-Factor Authentication (MFA)
With the fact that cybersecurity has advanced being a sophisticated regulation, theres also an increasing border concerning honourable concerns and just how closely we need to abide by them in enacting these types of safeguards. Cyber security is not only protecting systems and data from actors but also that the actions taken should be within limit and they do trespass the boundaries of individuals. Adhering to cybersecurity ethics is key not only because it allows for the building of trust, but also helps in keeping everything above board with compliance and impacting a moral aspect on our digital interactions.
The challenge for cybersecurity professionals arises from the complexity of ethical dilemmas, where security must be achieved at minimum cost to privacy and personal freedoms. This series talks about a number of ethical components inside cybersecurity, which includes privacy and data protection as well as surveillance & monitoring but I would primarily focus on these two in addition to the significance of responsible disclosure through legitimate methods like creating your own notes. Adding an ethical dimension to cybersecurity strategies can only help ingrain a culture of ethics and accountability, leaving the digital world safer and more fair.
Privacy is a human right: this means cybersecurity must deliver security while at the same time regard personal data as something in special need of protection. This includes securing comprehensive data protection, embodying transparency in gathering and employing data as well respecting individuals' privacy rights.
Organizations need effective data protection strategies, including encryption and access controls to protect personal information. These controls are thereafter assessed at regular intervals to be changed in order combat against new threats.
When data is in transit, encryption helps to protect the privacy and confidentiality of that information so it can't be accessed by unauthorized third parties. Access controls restrict who can see the data, making it less likely that unauthorized individuals may access practice information. Carrying out audits and performing vulnerability assessments will help you determine data weaknesses, which can be addressed to fill in those gaps with more efficient protection.
In order to ensure trust, transparency regards both collecting and using the data. Organizations need to be transparent about what data they are collecting, how it is used and get consent from individuals.
Users must be notified about the clear and unambiguous privacy policies, ie informational which outlines what data it captures when A certain amount of information including third party affiliation is shared with these details. The process will include giving users a way to opt-in or out of data practices and also clearly explaining in what their choice consists.
Although surveillance and monitoring are crucial for cybersecurity, they also raise ethical concerns because of the extent to which they monitor people’s behavior. To diminish ethical concerns, it is important for organizations to develop policies and guidelines regarding surveillance that would be ethical and respect the privacy of individuals.
Purpose: Surveillance has to be conducted in a lawful manner. Usage of protection mechanisms such as VPNs reviews guidelines. Garage: It depends on the type of recorded data the orientation of the recording mechanisms. It can use an individual or in a common storage on surf shark.org review.
Data Access and Usage: Due to one of the principles of data protection, it is only used for the purposes for which data were collected.
It is more effective surveillance has to be built around the concept of privacy. It also uses privacy technology, such as procedures and technology services,cpn, to get into contact with regards to privacy. Organizations should also regularly inquire into its personal and privacy.
Ethical hacking and integrity, a commitment to work with stakeholder, Coordinate to organizations. Ethical hacking refers to the process of identifying and rectifying any issues that may allow malicious users to exploit the infrastructure.
This proves that ethical hacking is necessary, as the things those appear extremely brutal hackers can also be done by a person with secret malefic who will hack into your life and destroy you whether it an individual or government. Only difference between unethical hacker and someone powered whom he recognize itself without fear of punishment which legal system provide for fairness; aka clear guideline about how to lawful impairment his/ her targetependency. These recommendations would hopefully underscore the need to obtain appropriate permission while ensuring NO intercourse has occurred in any manner.
Ethical hacking needs to be elicited in a way that it creates the least possible danger or disruption for any company being deployed. They need to properly document their finding and give us how items that will require compensation. It is important to maintain good communication with the target organisation during all steps of testing process, failure in which will not only result into absence transparency but loss trust.
Responsible disclosure means you report the vulnerability in a timely and confidential manner to the vendor of whatever has been identified as vulnerable. This is to ensure that the security holes are rectified before it can be exploited by hackers.
There should be a written process for receiving and reacting to vulnerability reports. This includes receipt of the report, frequent status updates to the reporter as we collaborate on remediation. Another way to motivate ethical hackers is to give them some sort of reward, again a bounty program similar - PRIVACY or bug bounties.
These following Case studies show how theoretical principles and strategies play out in real-world scenarios - much to the confusion of many who are learning cybersecurity for the first time. Exploring individual incidents not only provides insight into the successes and failures of others but also reveals a more nuanced perspective on cybersecurity outcomes when dissected through its human-factor roots. Together, these case studies underscore the power of human error, capability effect improvement and strong data security protocols with real take-aways to make our own cyber hygiene that little bit stronger.
Social Engineering Attack on a Financial Institution Case Study 1 This is a case study about how the use of social engineering leaded to fraud with big losses for bank. They played on the humanness of people, pretending (among other things) to be familiar senders that were able coerce employees into sharing too much information. This example underscores that without proper training and the presence of mind social engineering scams are very difficult to prevent.
The attackers performed extensive reconnaissance to learn about the organization and its personnel. They leveraged this information to create inaccurate phishing messages and persuaded victims they came from trustworthy sources. The victims said the compromised employees were trained to administer their respective HR and payroll roles -- including transferring funds within ZDIAS's system of accounts, then fooled by the crooks into providing their usernames and passwords.
The bank replied by launching a detailed set of social engineering detection training. Additionally, they have hardened their email handling such as adding advanced filtering and warning banners on external emails. This use case further exemplifies the importance of ongoing education and technical controls against social engineering tactics.
A healthcare institution suffered a data breach exposing thousands of patient details. The breach also brought questions of data security and privacy into the discussion. This case underlines the importance of being completely sure followed by strong data protection concepts which come all together with ethical norms as to treatment sensitive information.
A vulnerability in the organization's electronic health record (EHR) system made it possible for unauthorized access to patient information. Information such as names, addresses, medical history and social security was exposed. This violation equated into severe brand and legal ramifications to the healthcare organization.
To address that criticism, the association put in place more rigorous encryption procedures and running ongoing security audits, appointed a DPO dedicated to ensuring compliance with privacy laws. A patient awareness campaign was also undertaken to promote citizen education on safeguarding their identity. Proactive Data Protection and Ethical Stewardship of Sensitive Data: A Case Study
Employers have to develop a culture of cybersecurity that shows employees the significance of it and get them involved in protecting their organizations. This includes ongoing training, written documentation of protocols and giving employees the opportunity to identify suspicious behavior.
Continuously train employees about the most common cyber security threats and effective strategies for protection It must interact and follow sales scenarios.
There must be various training sessions, which are exemplary for introducing subjects like phishing; safe browsing password management incident reporting. The use of interactive elements, such as quizzes and hands-on exercises may help engagement to improve the recall by. Regular refresher training helps staff stay sharp and educated about new threats.
When employees are clearly aware about their role in the cyber security policies, they also come to know what needs to be done if a breach occurs. Presumably it would only be accessed for larger design policy type stuff and even then you should have reachable/ commonly reviewed policies.
All the cybersecurity policies and guidelines should be maintained centrally by organizations, which are accessible to all employees. Frequent communication that this is company policy and not just something one manager thought up, are all part of the reinforcement. Creating an open discourse also allows your employees to ask questions and demand clarification on cyber- security related materials.
Security measures should be designed with human behavior in mind. This includes user-friendly interfaces, clear instructions, and minimizing the complexity of security procedures. By considering human factors, organizations can improve compliance and reduce the risk of human errors.
User-friendly interfaces reduce the likelihood of errors and improve compliance with security protocols. Interfaces should be intuitive and provide clear instructions to users.
Designing user-friendly interfaces involves conducting usability testing to identify potential barriers and pain points. Feedback from employees can inform improvements, ensuring that security measures are both effective and easy to use. Consistent design elements and straightforward navigation contribute to a positive user experience.
Simplifying security procedures makes it easier for employees to comply with security policies. This includes reducing the number of steps required to perform security-related tasks and providing clear guidance on complex procedures.
Streamlining security procedures can involve automating repetitive tasks and integrating security features into existing workflows. Clear, step-by-step instructions and visual aids, such as infographics, can guide employees through complex processes. Regular feedback sessions can help identify areas for further simplification.
Having ethical. guidelines and regulations in place matters more than anything when it comes to cybersecurityethical standards as well. Businesses should audit on a regular basis, create an ethical training and regularly reward employees for demonstrating ethics.
These audits serve to ensure that cybersecurity practices remain within the bounds of principles and legislation. Audits must test the security controls for their effectiveness and stimulate suggestions for enhancement.
A robust audit will check technical controls, policy adherence and employee behaviour. Third-party audits give you an impartial assessment that can expose blind spots. The results need to be recorded, and they should contribute towards any continuous improvement strategies.
Cybersecurity training should include programs that teach ethics. These programs need to provide some component educating staff on the appropriate ethical framing in cyberspace and reinforce a high standard of ethics.
Cybersecurity has to be human-centric So we come back to the critical point that cybersecurity needs not only keep pace with technological advancement but also start addressing how and why our behavior is a key component of what happens before technology hits us. Improving cybersecurity posture, preventing the human factor from affecting cyber incidents can be done by understanding and addressing human elements, increasing awareness for organizational staff in terms of information security behaviors and ethical standards. Human-Focused - This holistic process of considering humans alongside the technology that powers them, helps to maintain resilient and ethical cybersecurity practices.
Incorporation of human-centric strategies in cybersecurity mitigates the introduced vulnerabilities through a more prepared and prudent human behaviour whilst promoting security attitude alongside ethical responsibility within culture. By building a cybersecurity framework centered around human considerations and ethical dimensions, organizations can build a resilient, adaptive security ecosystem that addresses growing cyber-risks while nurturing trust relations. And the result: a more secure and ethical digital environment for all organizations, individuals [1-12].
