Author(s): Anvesh Gunuganti
This paper discusses identity-centric security as a crucial approach for protecting cloud workloads in the contemporary world of integrated networks. It seeks to fulfill this need by explaining the importance of securing cloud workloads as cloud computing has become central to organizational functionalities. The review focuses on the importance of identity-centric security and the change from perimeter protection approaches, which are no longer effective, to more sophisticated identity assurance and ubiquitous authentication. It outlines difficulties related to cloud workloads and provides prospective solutions stressing identity management systems integration. The study thus points to the need to preserve identity-centric strategies for improving cloud security, managing risks, and being compliant with the existing regulations. Some advice for practice consists of implementing reliable identity solutions, monitoring, cloud supplier cooperation, end-user education, and security audits. According to the existing studies, future research directions should focus on creating new identity-based security paradigms that are appropriate to modern cloud infrastructures and carry out longitudinal studies to see how effective the created models of identity-based security are in getting through the real test of time. In summary, incorporating identity-centric security remains critical for protecting innovative cloud-based workloads and guarding a firm's valuable resources from future cyber threats.
The need for identity-centered security in today’s globally connected context is now important to establishing security in IT systems. This approach consolidates user and device identification and control as the primary framework for the security agenda. Considering the rampant importance of cloud computing in modern organizations, cloud workload protection protects an organization’s workloads in the cloud, encompassing any application, service, or data in the cloud environment. This review, therefore, seeks to elaborate on identifying requirements for identity-centric security for cloud workloads, the challenges surrounding them, and the common approaches to embedding Identity Management solutions for a stronger Cloud Security.
Centric security has emerged as one of the popular security models practiced in the current evolutionary IT environment [1]. It shifts the prime focus of security measures to the users and the devices involved and depart from perceptions of perimeter control. In particular, in the process of identity verification, the process contributes to excluding non-identified subjects and the action on a system rather selectively, granting the privilege to work on it only to certified individuals and entities. This change must occur, as the IT infrastructures are becoming more complex and distributed physically and geographically, where the user is transferring from one place to another.
This change aligns with the overarching shift towards relying on identity as a key security point, given tendencies associated with new dynamic and distributed IT environments. The traditional security models focused on accustoming the network boundary are no longer efficient for today's flexible employees, moving cloud computing, various smart devices, and other trending concepts. Identity- centric security does this to overcome these challenges by enabling continuous authentication, access control on a need-to- use basis, and strong identity management systems [2]. This makes it easier to ensure that high-security levels are aligned with the current technological changes in IT environments. As displayed in the figure 1 it is important to acknowledge that cloud services are secured in a certain manner which comprise of; Data protection, Threat detection, Access controls and compliance measures that are vital in ensuring integrity and confidentiality of the cloud services. Figure 1 shows cloud service security measures including data encryption, access control, threat detection, and compliance. All these elements together guarantee the data security in cloud, particularly ensuring confidentiality, integrity and availability of such data, which are main concerns of different organizations as well as users employing the cloud services.
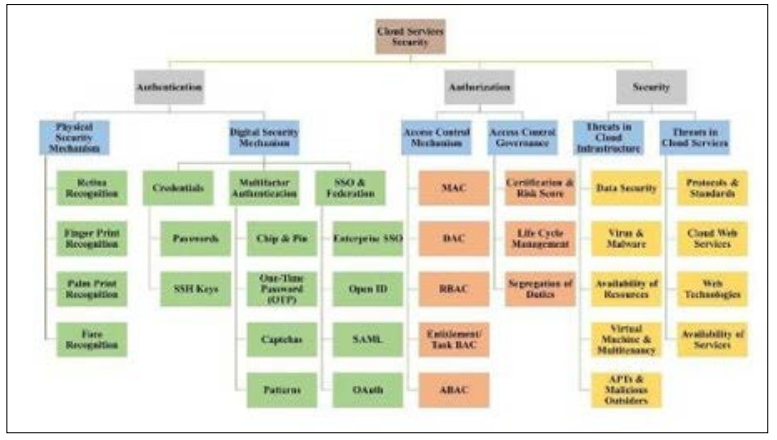
Figure 1: Cloud Service Security [3]
As adopting cloud computing gains momentum for supporting organizational operations, it provides the advantages of easy implementation, scalability, usage flexibility, and relatively low cost [4]. However, such changes also create new risks and problems in the security field. A cloud workload can be defined as the workloads that include applications, services, and data that execute in the context of the cloud, and they are way more exposed to various dangers than workloads residing in on-premises environments. Regarding the security of these workloads, it remains crucial that organizational IT security agendas align with the objectives of guarding such critical information, meeting all set legal requirements, and maintaining organizational image.
Cloud operations are frequently changing gradually, which is why they are of great concern to attackers, and protection against cyber threats is paramount [5]. Therefore, an organization has to implement security measures to efficiently address the workload type associated with the cloud. This requires protecting data just as when it is being moved from one location to the other when it is inactive, and how one manages access control with a strict, constant, and deliberate approach that involves constant monitoring and threat detection without interruption. In essence, by adequately implementing security measures to safeguard cloud workloads, organizations can use cloud computing to enhance their operations while simultaneously handling associated risks. Figure 2 presents a cloud access control model with other models of the same kind. The figure depicts how specific methods like the Role-Based Access Control, Attribute-Based Access Control, and the Multi- Factor Authentication compare with each other in terms of security, scalability, and the overall simplicity in managing the cloud resources needed for their execution.
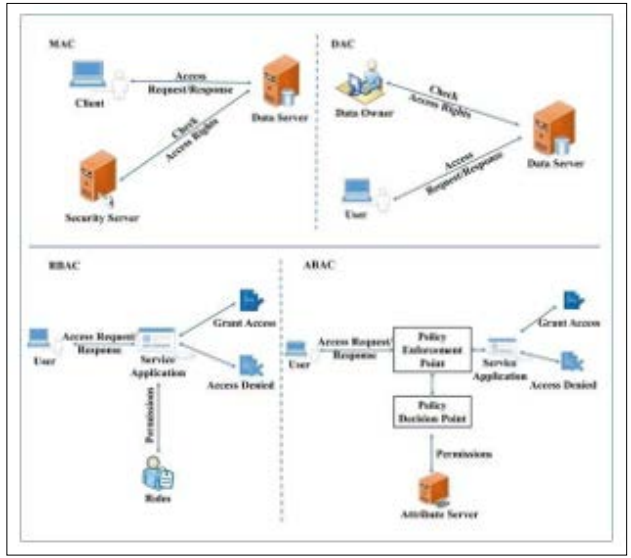
Figure 2: Access Control Mechanisms in a Cloud Environment [3]
This review will focus on analyzing the concept of identity-centric security in the context of cloud workloads. The paper will analyze identity-centered security and explore how the paradigm has transitioned from the conventional security assurance model to new models that aim to constantly determine a user's identity and subsequent authentication processes. This study, therefore, recounts the various steps that have transformed identity-centric security into an optimal solution for the new generation of IT systems by eradicating the defects of the earlier models.
Moreover, the concerns and measures that concern cloud workloads will also be described in the context of the review. It will focus on how ID management systems can help improve cloud safety and also how these systems can be effectively implemented. Hence, through this elaborate explanation, the review aims to foster a better understanding of how identification-focused methods can enhance the protection of cloud infrastructures to meet their distinct security challenges.
How does the implementation of identity-centric security frameworks impact the effectiveness of securing cloud workloads against unauthorized access and data breaches?
Identity-centric security has undergone drastic transformations over the years, moving from the conventional approach of perimeter defense to a concept that centers on validating identity and continually authenticating it [6]. This section further explains the identity-centric security concept, which focuses on identity, identifies the security issues related to cloud workloads and explains the integration of identity management into information security. Thus, after analyzing these aspects, it will be possible to outline the key advantages of identity- focused approaches, which can serve as the basis for creating effective mechanisms for securing cloud environments.
Definition and Evolution of Identity-Centric Security Traditionally, identity-centric security was designed in a completely different paradigm, but the overall change in the information technology space caused this. Previously, security measures focused mainly on protective barriers like firewalls and IDS for network resources [7]. However, the traditional approach of applied security solutions for business networks became insufficient when cloud computing, mobile employees, and complex connections between enterprises emerged. Identity-savvy security surfaced as a response to such challenges by focusing on entrusting individuals and gadgets as the building block of security.
This shift aligns with widely accepted zero-trust principles, prioritizing the continuous non-trust model of networks. By identifying individuals and enforcing the minimum level of data access permissions, companies can reinforce their defenses and mitigate the risks associated with actual possible changes in IT environments.
This cross-sectional view of security has stemmed due to flaws that come with traditional approaches to security. These models frequently proved inadequate since IT environments have become more complex and dynamic, and the traditional WAN/ LAN boundary can no longer be defined by clearly distinguished network resources accessed from multiple locations and equipped gadgets. Identity- aware solutions utilize continuous authentication, two-factor authentication security, and role-based security access, where resources can only be accessed and used by persons authorized for use. This approach enhances security by focusing on the most critical aspect of any security strategy: concerns about defining users and their devices in the networks implementing the system. In this case, this paper explains the advancement of identity-centric security as a way of assisting individuals to embrace the necessity of such a technique in the contemporary world of IT security.
Figure 3 gives a clear depiction of the working of Security Frameworks in Mobile Cloud Computing (MCC) in terms of encryption, authentication, secure communication and proactive application of security to secure the data and for having a strong hold on security in Mobile Cloud Computing environment.
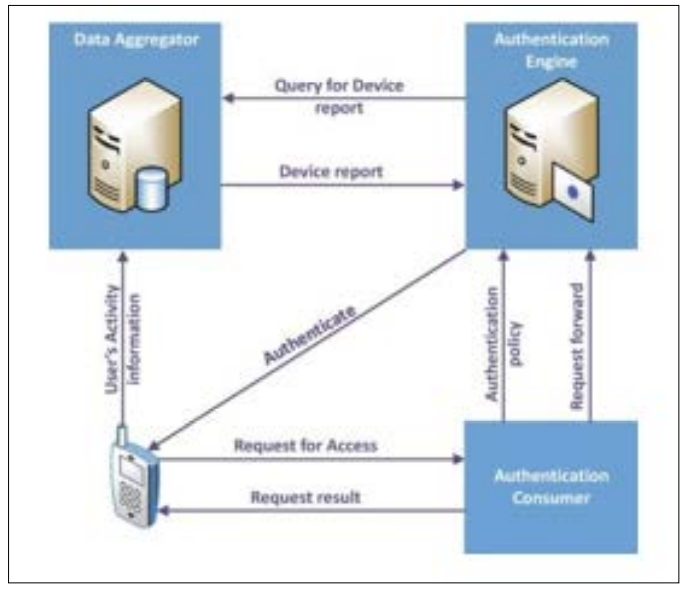
Figure 3: Security Framework in Mobile Cloud Computing [8].
Security Challenges and Solutions in Cloud Workloads Cloud computing workloads are quite an emerging area with numerous security challenges due to their dynamism and decentralization [9]. Of them, data theft is an acute problem because the data stored in the cloud is attractive to hackers. Preventing this risk would require encryption of data in transit and stored data samples. Moreover, the access control in the cloud network that may be tackled by virtualization may also be a source of potential vulnerabilities; thus, identity and access management may be complex. Using two-factor authentication for their accounts and setting user roles and permissions can reduce the likelihood of the problem occurring.
Some of the issues that concern businesses with cloud workloads include compliance and ad hoc governance. Business applications have to meet certain compliance requirements regarding cloud workloads, requiring strong auditing and reporting features. Responsibility in Cloud computing is also divided between the customer and the Cloud service provider, making security a bit more blurred. Incorporating identity and access management, information encryption, and constant audits are effective ways of filling this gap and reducing the risks associated with cloud computing. Figure 4 shows the security challenges in Cloud Computing.
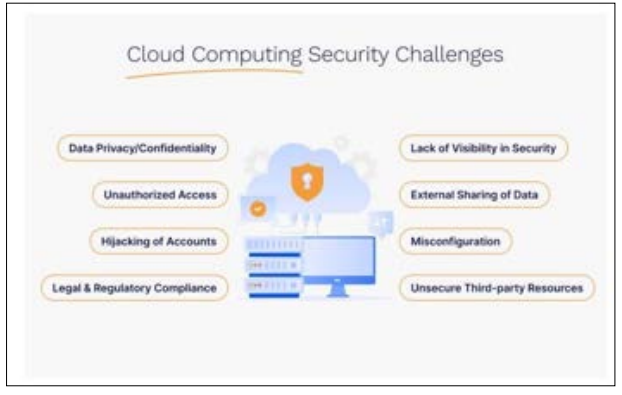
Figure 4: Security Challenges in Cloud Computing [10].
Integration of Identity Management in Cloud Security Incorporation of identity management into cloud security should be critical due to the importance of security in cloud environments. Identity management systems are beneficial for joining the customer's identification of the resources and devices they wish to access or are accessing clouds to increase the security of the cloud by removing the outright chances of getting compromised [3]. One crucial area to consider is a single sign-on solution: signing in once, using one set of credentials or identity, for multiple cloud applications and services. Single sign-on solutions facilitate access management and strengthen security structures by centralizing organizational authentication.
Moreover, the Multi-Factor Authentication (MFA) is an added layer to the security measures by allowing users to provide other means of identification besides passwords [11]. MFA works by integrating other authentication variables like biometric data or SMS codes/hardware tokens, thus minimizing vulnerability in a system occasioned by hacking user logins. Similarly, another significant element of identity management in cloud security is role-based access control (RBAC). Rich, flexible, and scalable, RBAC is an efficient system that controls user rights depending on their position within the organization. It grants access only to the utility to use necessary tools and features. Organizations can incorporate RBAC policies to form a principle of least privilege that would further reduce the organization's vulnerability to an attacker in the case of a security breach and the case of the presence of an insider threat. Incorporating an Identity Management System into cloud security strengthens security and access controls, optimizes user interface, and helps organizations control users' access to cloud resources.
The Identity Management System regulates people and their associated attributes in cloud infrastructures [6]. These are commonly used details in Internet sites or systems, such as usernames, passwords, email addresses, and user roles. SSO allows users to sign on once for various cloud services, and the federation capabilities employed through the use of SAML and OpenID Connect facilitate the identification of cloud services.
The access control mechanisms regulate how users interface with cloud resources and information. Open authorization (OAuth) users’ authentication and Security Assertion Markup Language (SAML) systems are some of the ways through which users are authenticated securely [3]. RBAC allocates privileges based on the position, while ABAC may decide based on the user's location and other factors. Policies on access help to regulate this through rules that must be followed in order to gain access as well as to fulfill the need for security. As illustrated in the figure 5 below, the main authentication mechanisms in a cloud environment. This comprises of strategies such as Single Sign-On (SSO), Multi Factor Authentication (MFA) and biometric security measures. Both methods are important in the cloud environment and work towards enabling advantageous access to the cloud resources and authenticating the users to reduce the potential access by an unauthorized person.
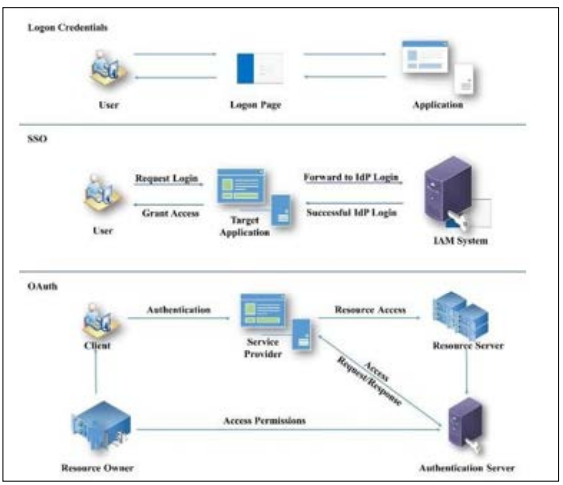
Figure 5: Authentication Mechanisms in Cloud Environment [3].
Identity management and access control within the cloud environment means configuring the identity endpoints and provider. In the case of RBAC, the roles and access policies are created using native identity and access management (IAM) of cloud services. ABAC necessarily requires the integration of attribute sources such as lightweight directory access protocol (LDAP) directories. It is gained through the evaluation engines that make access policies in force so that easy access to the cloud resources is granted without leaking out to outsiders [11].
Security policies and frameworks help to provide security while migrating workloads to the cloud and protecting data from malicious attacks, data breaches, etc. Here, we will review key security policies and frameworks commonly used in cloud environments, along with their technical implementation and effectiveness:
IAM policies specify identity and access rights to cloud resources and services. These policies support the least privilege principle, which requires users to have only those permissions they require to do their work [2].
Technical Implementation: IAM policies are written in JSON (JavaScript Object Notation) format and can be assigned to IAM users, groups, and roles. Policies are statements that define the manner, means, and circumstances under which an organization will control the use of specific resources.
Effectiveness: IAM policies have proven to be very efficient for cloud resource access control since, with their help, organizations can manage permissions and secure resources with the least privilege method.
Zero Trust Architecture is a security concept as far as the acronym goes; otherwise, it stands for Never Trust, Always Validate. It is the presupposition that threats may stem from inside as well as outside the network perimeter. Hence, access, privileges, and usage should be continuously validated [9].
Zero Trust is built around a principle where security is focused on identity and includes features such as MFA, identity verification, monitoring, and segmentation.
Zero-trust architecture improves the organization’s security by reducing the attack surface and limiting the attacker’s ability to move further inside the network. Thus, security threats can be identified in real-time by verifying user identities and the level of trust for a given device.
Cloud security frameworks are a set of guidelines and recommendations for planning, developing, and operating secure cloud applications. These guidelines are based on different categories of cloud security, such as identity and access management, data security, network security, and compliance.
Technical Implementation: Organizations attain cloud security frameworks by adhering to best practices issued by cloud service providers. This incorporates setting up security parameters, turning on security options, and implementing third-party security applications as required [5].
Effectiveness: Cloud security frameworks act as tools to assist an organization in enhancing the security of any workloads within cloud computing environments for efficient implementation of security measures on risk management. According to the current trends in IT security, organizations can improve security, compliance, and security threat management [7].
Hence, security policies and frameworks, including IAM policies, Zero Trust Architecture, and cloud security frameworks, are essential in cloud workload protection. The technical processes that envelope their execution include establishing restrictions on access, ways of identifying users, and security measures against intrusion and cybercrime. When properly conducted, these policies and frameworks help increase security and decrease the level of risk while simultaneously meeting the legal requirements of cloud computing.
Assessing the security of cloud workloads involves various metrics and comparisons between tools and frameworks:
Implementing identity-centric security in cloud environments presents several technical challenges that organizations must address. Here, we will identify these challenges and review proposed solutions and advancements in the field:
Identity Sprawl: Multiple user identities and devices require proper management in and across multiple cloud environments causing difficulties and security threats. Centralized identity management, like Identity-as-a- Service (IDaaS) platforms, can manage access and policies efficiently, hence improving access management [1].
Access Management Complexity: With multiple clouds and hybrid cloud models, the access control policy becomes problematic. RBAC and ABAC clarify the concept, and automated provisioning provides timely access changes to lighten the admin load and increase security.
Today, modern organizations are turning to cloud computing providers to meet the flexibility and availability requirements for IT as they adopt digital and App-Based businesses. Such a shift frequently entails blending intricate multi-cloud infrastructures consisting of public cloud IaaS from vendors, including Amazon Web Services [6]. While it still has its advantages, some need for clarification about the shared responsibility model still exists, which can lead to various severe cybersecurity issues.
The notion of security is evolving from using an IP address for protection to focusing on an identity-based and zero-trust model for protection. This approach involves regular risk checking and automation and ensuring limited access to risk controllers. The research also agrees that organizations must understand and apply such strategies to enhance security and protect organizational assets when using cloud services [1].
This identity-centric ‘zero-trust’ approach meant using proper identity and access management solutions underpinned by two and three-factor multi-authentication, strict most minor privilege policies, and micro-segmentation leveraged through practical monitoring tools for real-time detection [5]. The questions include how these solutions can work together in a multi-vendor IT environment to achieve security while being user-friendly, compliant with regulations and standards, easily scalable, and fast- performing. Nevertheless, the organization was able to record numerous successes within its cybersecurity framework, such as reinforcing the security measures, minimizing the threats of cyberattacks, increasing the levels of compliance with regulatory requirements, optimizing the activities, and implementing flexible solutions that can be easily adapted to the changing needs of the business.
The essentials of identity-centric security for cloud workloads are explained below. Thus, prioritized identity verification and access controls strengthen an organization's security and limit the potential for breaches by unauthorized access. Topics like multi-factor authentication and the principle of least privilege improve cybersecurity. Likewise, identity-centric frameworks guarantee compliance with regulations [9]. In addition, flexible access control methods and integrated security solutions enhance internal efficiency and relevance to the constantly changing needs of businesses within the cloud.
The idea of applying identity-centric security in the cloud environment has its drawbacks. The problem of having numerous user identities and critical controls in various cloud environments is challenging. Nonetheless, it is attributed to the fact that issues like centralized identity management platforms and automated provisioning alleviate these challenges. Finally, the adoption of RBAC and ABAC makes the access management of hybrid cloud environments more accessible to manage and deploy, thereby significantly minimizing the administrative overhead and standardizing the level of security to be provided.
As a result, organizations need to stick to the best practices on cloud workload security and learn from practices implemented throughout cloud projects. These involve the use of identity management systems to provide consolidated identity and access management, the use of continuous monitoring tools to identify the threats as well as provide real-time countermeasures, engaging the CSPs to enable proper integration of security solutions, promoting security measures, and counter-checking the efficiency of existing security solutions through regular audits, respectively.
In conclusion, the strategy mainly focusing on identity is a significant approach to adapting security measures in cloud workloads in the contemporary world. Security trends unveil the progression of security approaches, making constant, reliable re- authentications and access control measures necessary to deal with cyber threats and remain compliant [7]. The best practices are to use effective identity management to ensure protected access, use continuous monitoring solutions, cooperate with cloud providers, increase users' awareness, and regularly audit.
Cloud workloads are most securely managed, with priority being given to identity-centric security, as shown by this research. It outlines the changes in the security paradigm from traditional concepts based on perimeter security to identity security, focusing on constant monitoring and management of security access. Currently, cloud workloads are inevitable in organizations' operations; hence, there is a need to establish adequate security measures to address inherent threats and means to meet compliance regulations. The connection of identity management systems helps to increase protection levels and organizational performance in clouds.
Recommendations are as follows: Utilize robust identity solutions and authentication and access control to provide central management and visibility, continuously monitor networks for threat detection and response, Work with the cloud service providers to facilitate integration of cloud security, Train the users on more security measures, and finally perform security assessment and testing regularly to measure the organization's progress. If following the latter, the mentioned recommendations will help organizations to improve the protection of their cloud workloads and related risks.
For subsequent studies, it is recommended that new identity- centered security models be developed that address the contemporary state of cloud environments. This comprises new approaches to authentication, increasing standardization of identity management systems, creating effective threat intelligence solutions, and combating new problems of identity and access management. Also, longitudinal studies can evaluate the effectiveness and applicability of identity-centric security solutions to address the emergent threats in the cloud environment in the long term. As a result, organizations can continue researching and innovating to protect their cloud workloads from cyber threats.
