Author(s): Sampath Talluri
Identity and Access Management (IAM) plays a pivotal role within Amazon Web Services (AWS) by governing the utilization of cloud resources and enhancing the overall security of the AWS ecosystem. IAM allows AWS users to effectively manage resource access while ensuring a robust security framework. This exploration delves into the fundamental concepts that underpin IAM, shedding light on authentication and authorization processes, best practices, practical implementation scenarios, and the convergence of IAM and security, and provides a forward-looking perspective into emerging trends in the field.
IAM's significance lies in its ability to control access for individual users and groups, roles, and policies, ensuring the principle of least privilege and minimizing security risks. Multi-factor authentication (MFA) is a key facet of IAM within AWS, offering an extra layer of security and identity verification. This enables organizations to fortify access control measures, safeguarding their AWS resources from potential threats.
In addition to these foundational concepts, this exploration delves into practical implementations, elucidating how IAM can be leveraged to meet realworld security and compliance requirements. IAM's robust features enable users to define and manage access permissions with precision, catering to the specific needs of their organizations.
Furthermore, this abstract introduces the IAM Query API, which provides a means to interact directly with AWS services. The IAM Query API supports GET and POST methods through APIs, offering developers and administrators a more streamlined approach to managing access to AWS resources.
IAM is a linchpin in AWS security, ensuring that access to cloud resources is fine-tuned, well-protected, and compliant with best practices. The continued evolution of IAM, including integrating emerging technologies and security measures, promises to further enhance the security posture of AWS users and the cloud computing ecosystem.
Identity and Access Management (IAM) is the bedrock of security within Amazon Web Services (AWS), furnishing organizations with a robust framework to govern and manage access to their cloud-based resources. An in-depth understanding of IAM is essential for unlocking the full potential of AWS services and ensuring that access to these resources is both secure and precisely tailored to organizational needs [1, 2].
In the AWS environment, users represent the individuals or entities seeking access to various AWS resources. Groups, on the other hand, function as a means to organize users based on shared permissions or access requirements. Additionally, roles are pivotal, enabling services and applications to access a diverse array of AWS services without the need for traditional user credentials. This structured approach facilitates efficient and controlled interactions between different elements of the AWS ecosystem, contributing to a more secure and manageable cloud environment.
Policies, as the final piece of the IAM puzzle, provide the means to fine-tune access rights, offering a highly granular approach to access control. IAM policies allow organizations to define and enforce specific permissions, ensuring that only authorized actions are executed within their AWS environments.
This paper endeavors to delve into the core principles and functionalities of IAM, illuminating the intricacies of its operation. By providing insights into best practices and practical implementations, this paper aims to empower AWS users with the knowledge required to optimize IAM within their cloud infrastructure. Moreover, this exploration will take a forwardlooking perspective, examining how IAM continues to evolve within the dynamic cloud landscape, adapting to emerging technologies and security requirements to maintain its critical role as a linchpin of AWS security.
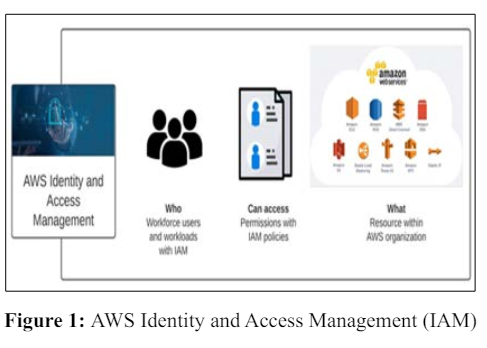
IAM users and groups are fundamental entities for managing access. This section explores their roles and interactions within the AWS.
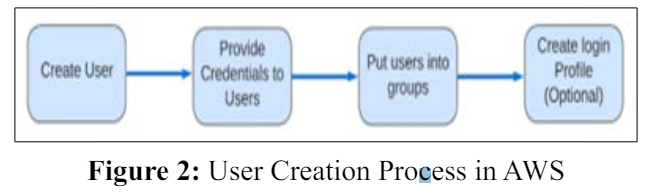
Users are defined as individuals with an account to access the AWS workspace. Users will only have one account to access the environment [3]. There is also a restriction on the user account creation based on the region and cost “IAM and AWS STS quotas” [4]. If you look at Figure 2, we are creating a user with all the necessary permissions and access and login credentials to the user.
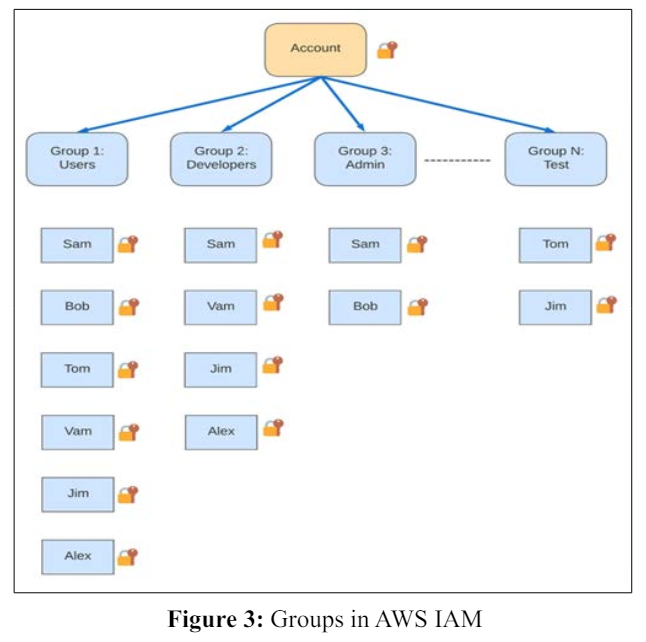
Groups are used to club multiple users in one place to swiftly assign the necessary access and permission to the users. This will also help us to manage access/permission. User groups can’t be nested, and users can be in multiple groups as needed [5]. The number and size of the group depend on the AWS account “IAM and AWS STS quotas” [4]. If you look at the Figure 3, You can see accounts are having multiple groups associated to them.
Roles define a set of permissions for making AWS service requests. IAM has multiple roles defined in AWS. We can switch roles using AWS CLI or API and set the time frame for the role assignments [6]. We can also use user roles to delegate access to users, applications, and services [7]. The roles will not have any long-term credentials or access keys associated with them. Still, when we assign a role, it will have temporary security credentials for the given session [7].
IAM roles having temporary credentials are used in the below situations [6]:
IAM roles with temporary credentials are often used in a federated identity scenario, allowing external users, such as employees from partner organizations or customers to access AWS resources.
These roles grant permissions to temporary IAM users. They were created for short-term projects, testing, or other temporary needs.
IAM roles with temporary credentials are essential for crossaccount access scenarios. For instance, if one AWS account needs to access resources in another, a role is created in the target AWS account, and the originating account can temporarily assume that role to gain access.
Roles with temporary credentials can enable cross-service access. For example, granting an Amazon S3 bucket or EC2 access to trigger an AWS Lambda function involves assuming a role temporarily, allowing the Lambda function to perform actions on the bucket.
In the context of AWS, a principal is often an AWS service or resource that requires access to other resources.
It is used for AWS services like Lambda, EC2, or Elastic Beanstalk to access other AWS resources. They typically provide permissions to resources created and managed by AWS services.
Service-linked roles are predefined IAM roles used by AWS services to grant permissions to perform actions on behalf of the service. These roles are often automatically created by the service and have specific permissions associated with the actions they perform.
Roles with temporary credentials are used for applications running on Amazon EC2 instances. These roles allow EC2 instances to securely access other AWS services without storing long-term credentials on the instances themselves. This enhances security and simplifies credential management.
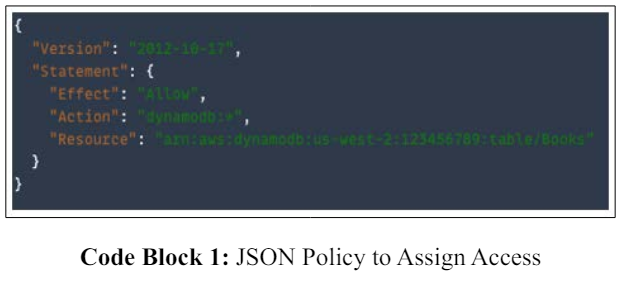
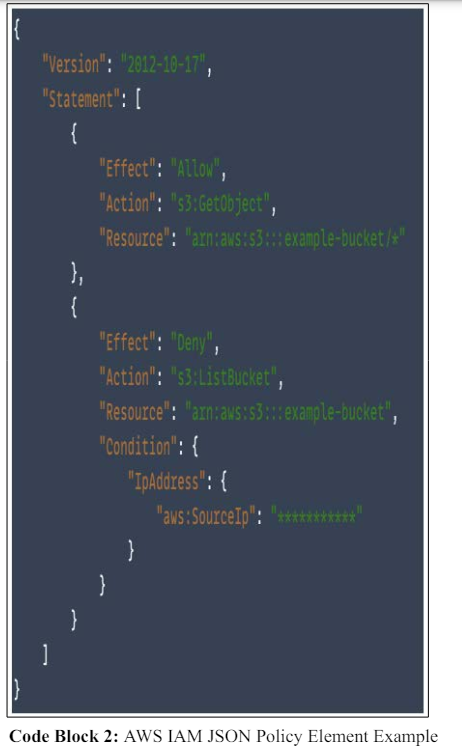
Policies are the building blocks of IAM permissions. An in-depth analysis of policies, their syntax, and how they shape access privileges are provided. AWS supports 6 types of policies [8]. If you look at Code Block 1, shows a JSON policy that allows theuser to perform all AWS DynamoDB actions (dynamodb:*) on the Books table in the 123456789 accounts within the us-west-2 region.
A JSON-based permissions policy controls the identity of users, groups, and roles [8]. They are categorized into two types: Managed policies and Inline policies. Managed policies are standalone and can be attached to multiple entities, making them easier to manage and update. Inline policies are directly embedded within a single user, group, or role, providing more granular control at the entity level [8].
These policies are used to grant access to AWS resources like S3 buckets or EC2 instances, allowing you to define who can perform actions on a specific resource. Resource-based policies are typically attached to the resource itself, and they determine access based on the characteristics of the resources, such as a public S3 bucket or an EC2 instance [8].
Permissions boundaries serve as a safeguard to limit the maximum permissions granted to an IAM entity. An entity can only act if it satisfies identity-based policies and permissions boundaries, which allows for a structured approach to managing access while preventing excessive permissions that identity policies could grant [8].
SCPs manage and control AWS accounts within an AWS Organization centrally. These policies define guardrails that restrict AWS accounts' actions, providing a governance layer to ensure compliance with organizational policies, security standards, and cost controls [8].
ACLs specify fine-grained control over which principals in another account can access and perform actions on existing resources. These are commonly associated with Amazon S3 buckets and provide an additional access control layer beyond IAM policies [8].
Session policies are used to create temporary access sessions for a role or federated users. These policies define the permissions that will be in effect during a temporary session, granting specific access for a limited timeframe. They are commonly used in scenarios where users assume roles temporarily for particular tasks or applications, and they offer a level of security and control over session-based access [8].
IAM's authentication mechanisms are pivotal components of its security framework, with various methods available to verify user identities. These methods include password-based authentication, multi-factor authentication (MFA), and AWS Identity Federation. MFA, in particular, adds an extra layer of security by requiring users to provide two or more authentication factors, bolstering the protection of sensitive AWS resources. To streamline the authentication process, it is highly recommended to utilize AWS Software Development Kits (SDKs) or the Command Line Interface (CLI) for authentication requests. This approach enhances efficiency and reduces the complexity of manually validating or calculating authentication information.
IAM's authorization processes are equally crucial, as they dictate which actions users or systems can perform within the AWS environment. These processes involve policy evaluation and enforcement to ensure users possess the appropriate permissions for their actions. IAM policies are employed to specify these permissions, either granting or denying specific access rights based on user identity, privileges, or assigned roles. This fine-grained control over access helps organizations adhere to the Principle of Least Privilege (PoLP), limiting potential security risks and minimizing the scope for unauthorized actions.
In summary, IAM's authentication and authorization mechanisms work in tandem to provide a robust security infrastructure within AWS. By verifying user identities and controlling access to AWS resources, IAM enables organizations to maintain a secure and compliant cloud environment. Leveraging MFA, AWS SDKs, and IAM policies, IAM empowers users to access AWS services while adhering to stringent security standards and best practices.
The Principle of Least Privilege (PoLP) is a fundamental security concept, especially crucial in the context of Amazon Web Services (AWS) Identity and Access Management (IAM). PoLP is based on the idea that individuals or systems should be granted the minimum level of access required to perform their tasks, thereby reducing the potential attack surface and minimizing security risks. In AWS, IAM plays a central role in enforcing the PoLP. AWS IAM allows organizations to define and manage user, group, and role access permissions. Organizations can significantly enhance their security posture by adhering to the PoLP within IAM.
This principle dictates that AWS IAM users and entities should only have permissions to perform actions necessary for their specific roles or tasks, and nothing more. By implementing least privilege, AWS customers can mitigate the risk of accidental or deliberate misuse of access rights, limiting the damage that a compromised account or a human error can cause. Furthermore, IAM provides fine-grained control through policies, which can be customized to specify who can access which AWS resources, under what conditions, and with what actions. Organizations can also leverage IAM's policy conditions to further restrict access based on factors like IP addresses and time of day.
By following the Principle of Least Privilege in AWS IAM, organizations can bolster their security, minimize the potential for security breaches, and ensure that their resources remain well-protected in the cloud.
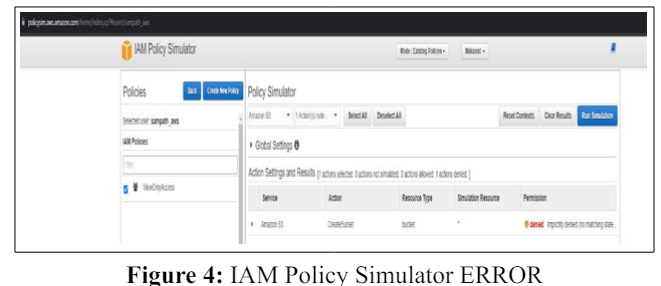
This section underscores the necessity of ongoing audits and reviews to identify and rectify potential security vulnerabilities and access anomalies. With respect to AWS, there is a special tool named IAM Policy Simulator. Without manual testing, the administrator can assess the privileges of other users or roles to determine if they have sufficient permissions to perform their required job duties. For example, in the figure below, we have a user named Sampath_aws with 'view only' access to the AWS account, but when attempting to perform a 'CreateBucket' (S3) operation, it is denied due to the lack of required privileges for the task.
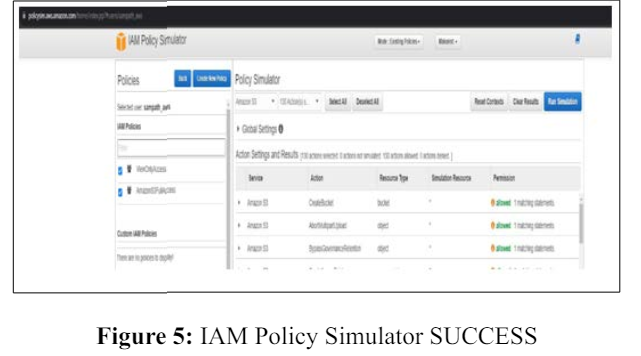
In the figure below, for the same user, we have added 'AmazonS3FullAccess' permissions alongside the 'view-only' permissions, granting access to S3 operations as depicted in the figure. Therefore, we can readily audit and confirm the assignment of specific permissions to particular roles or users using the IAM Policy Simulator.
Effective AWS secret key management is paramount for maintaining the security and integrity of cloud-based systems and applications. Properly securing and managing AWS secret keys ensures the confidentiality of sensitive data and protects against unauthorized access. AWS provides a comprehensive suite of tools and services for secret key management, including AWS Key Management Service (KMS) and AWS Secrets Manager. This allows users to create, rotate, and control access to secrets and encryption keys.
As scholars have highlighted (Smith et al., 2022), these services streamline the management process and enforce best practices, such as key rotation and fine-grained access controls. By adhering to these practices and leveraging AWS key management solutions, organizations can significantly reduce the risk of security breaches and data exposure, ensuring compliance with industry standards and regulations.
IAM security is critical in enforcing and managing user access within AWS. It allows control access to their resources with finegrained precision, ensuring users have the appropriate permissions in the organization. Multi-factor authentication (MFA) is a critical layer of security within IAM, offering an extra level of user verification beyond traditional passwords.
MFA is a secondary authentication method that adds a significant layer of protection to user identities. AWS supports three types of MFA:
FIDO (Fast Identity Online) security keys provide a hardwarebased MFA solution. They offer a high level of security by requiring users to physically possess the key and authenticate themselves by plugging it in or using NFC/Bluetooth connectivity.
Virtual authenticator apps, such as Google Authenticator or AWS MFA, generate time-based one-time passwords (TOTPs) that users must enter to complete the authentication process. These apps run on a user's smartphone or device.
Hardware Time-based One-Time Password (TOTP) tokens are physical devices that generate temporary codes. Users enter these codes during the authentication process. They are beneficial in environments with strict security requirements.
It's important to note that AWS GovCloud (US) Regions specifically offer hardware TOTP tokens for enhanced security. These tokens benefit government and highly regulated sectors where stringent security measures are required to protect sensitive data and resources. By incorporating MFA, mainly through these authentication methods, IAM security becomes more resilient to unauthorized access, safeguarding AWS resources and data and helping organizations maintain high security and compliance.
The paper speculates on the future of AWS IAM in the context of the rapidly evolving cloud landscape, considering emerging technologies and changing security paradigms.
As biometric technologies such as fingerprint, face, iris, voice, and palm recognition become more sophisticated and widely adopted, AWS IAM will likely integrate these methods for enhanced user authentication, providing an additional layer of security and a more seamless user experience.
The trend towards passwordless authentication methods, including email, SMS, and push notifications, is expected to continue in AWS. As these methods evolve, IAM in AWS will likely incorporate advanced features, making authentication more convenient and secure.
The adoption of the Zero Trust security model is on the rise, emphasizing the need to authenticate and authorize every user and device trying to connect to resources on a network. AWS IAM is expected to align more closely with Zero Trust principles, enhancing security and access control.
AWS IAM will likely leverage artificial intelligence (AI) and machine learning (ML) for predictive security analysis. AI can help identify patterns and anomalies in user behavior, allowing for proactive threat detection and automated responses to potential security risks.
IAM in AWS is expected to implement continuous access monitoring, allowing real-time assessment of user activities and access patterns. This trend will help identify and respond to security threats promptly.
Adopting decentralized identity technologies, such as blockchainbased identity solutions, may find their way into AWS IAM. These solutions could offer users more control over their identities while maintaining security.
IAM security in AWS may incorporate behavior-based authentication, where user actions, locations, and device data are analyzed to verify identity, adding an extra layer of protection and reducing reliance on static credentials.
In conclusion, our exploration of Identity and Access Management (IAM) within Amazon Web Services (AWS) has underscored its pivotal role as a foundational and robust security service.
IAM serves as a linchpin in safeguarding the security and integrity of AWS resources and environments, providing tools and mechanisms to fortify access control. IAM's user and group management flexibility ensures that organizations can tailor access permissions to their specific needs while adhering to the Principle of Least Privilege (PoLP). This, in conjunction with support for various authentication methods, bolsters the security posture of AWS environments. Furthermore, IAM's capability for finegrained control over resource access, made possible through the meticulous crafting of policies, enhances the overall security of cloud deployments. The best practices of regularly reviewing and updating IAM policies and groups are crucial for maintaining the integrity of an AWS environment.
As we look to the future, IAM is poised to continue evolving to meet the ever-changing landscape of cloud security. This field will likely see further integration with emerging technologies and more streamlined methods for managing access to AWS resources. AWS users must stay informed about these developments to adapt and optimize their IAM strategies, ensuring that their AWS environments remain secure and compliant with evolving security standards. IAM will continue to be an essential component of any comprehensive cloud security strategy, and its importance is set to grow in parallel with the dynamic nature of the cloud computing landscape.
