Performing Security API Testing using Postman AI
Author(s): Maheswara Reddy Basireddy
Abstract
Application Programming Interfaces (APIs) are becoming more and more popular, thus it is imperative to make sure they are secure. Because APIs make an application’s data and functionality visible to outside parties, attackers may find them appealing. Automated and effective solutions are required since human error and time consumption are major drawbacks of traditional manual security testing techniques. This article investigates the application of Postman, a well-liked tool for developing and testing APIs, and its AI-powered functionalities for automated API security testing. It discusses typical security flaws in APIs, how to check for them with Postman, and the benefits and drawbacks of this method. The goal of the article is to give developers, testers, and security experts a thorough manual on how to use Postman AI for quick and easy API security testing.
Introduction
The way businesses handle application deployment and computing resources has been completely transformed by cloud computing. Businesses may obtain on-demand computing power, storage, and services via the internet by utilizing the cloud, eliminating the need for substantial upfront expenditures in hardware and infrastructure. Organizations can now expand their resources dynamically, cut operating expenses, and adapt more quickly to shifting business demands thanks to this paradigm change.
The explosion of big data and the Internet of Things (IoT), the need for affordable and scalable solutions, and the growing need for digital transformation have all contributed to the acceptance of cloud computing. The need for efficient methods and best practices to handle data storage, launch apps, set up continuous integration and deployment (CI/CD) pipelines, and guarantee reliable testing and maintenance procedures is increasing as more companies move their workloads and applications to the cloud.
This article explores the idea of Postman AI-based API security testing. It starts out by giving a summary of Postman’s AI- powered capabilities. It then goes over typical security flaws in APIs and how to check for them with Postman AI. Along with providing advice and best practices for efficient API security testing, the article also examines the benefits and drawbacks of this methodology.
Postman: An Overview and AI-Powered Features

Postman is a versatile API development and testing tool that simplifies the process of building, testing, and documenting APIs. It provides a user-friendly interface for sending HTTP requests, inspecting responses, and organizing collections of API endpoints [1]. Postman supports a wide range of features, including environment variables, automated testing with scripts, and collaboration capabilities.
In recent years, Postman has introduced AI-powered features to enhance its functionality and streamline the API development and testing process. These features leverage machine learning and natural language processing (NLP) to automate various tasks and provide intelligent insights.
Postman AI-Powered Features
- Test cases may be automatically generated by Postman AI using the API specification or previously submitted API It lessens the work needed for manual test generation by analyzing the data types, anticipated answers, and API structure to build thorough test suites.
- Intelligent Code Generation: For interacting with the API, Postman AI can provide code snippets in a variety of programming languages, including JavaScript, Python, and You may use these code snippets to create automated tests or to construct applications.
- Natural Language Inquiries: To communicate with Postman AI and facilitate various activities within the tool, developers and testers may utilize natural language inquiries. As an illustration, users may instruct Postman AI to “create a test for the login endpoint” or “generate code for the user registration ”
- API Documentation Generation: Using the API specification or previously submitted API queries as a guide, Postman AI may automatically produce API documentation. The documentation facilitates developers’ understanding and utilization of the API by providing examples, request and response formats, and endpoint definitions.
- Intelligent Code Completion: During API development and testing, Postman AI increases efficiency and lowers mistakes by offering intelligent code completion recommendations based on the structure and data types of the these AI-powered capabilities create new opportunities for security testing task automation while also streamlining the API development and testing process.
Common API Security Vulnerabilities
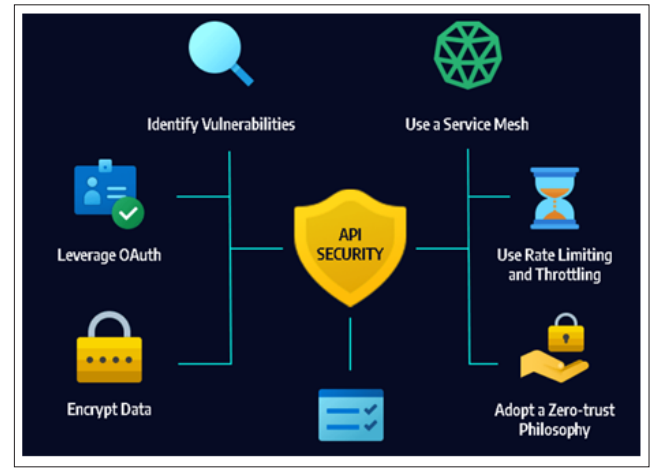
It’s important to comprehend the typical issues that impact APIs before learning how to use Postman AI to test for API security problems. The following are a few of the most common security flaws in APIs:
- Broken Authentication: Unauthorized access to APIs and the data they manage might result from inadequate authentication measures or incorrect implementation of authentication
- Broken Access Control: Unlawful users or systems may be able to access sensitive resources or carry out unlawful operations through the API due to inadequate or incorrectly configured access control measures.
- Injection Vulnerabilities: Injection attacks, such SQL injection, NoSQL injection, and command injection, can target APIs that do not adequately sanitize and check user This might result in data breaches or unauthorized access.
- Unsecured Cryptography: The confidentiality and integrity of data transferred over APIs may be jeopardized by antiquated or weak cryptographic techniques, poor key management, or unsecured transmission of sensitive
- Security Misconfiguration: Older software versions, unsafe default configurations, and activated services or features are examples of misconfigured security settings that can lead to vulnerabilities in
- Inadequate Monitoring and Logging: Inadequate monitoring and logging systems might make it more difficult to identify and look into security events or unusual API
- Excessive Data Exposure: APIs that disclose internal implementation details or deliver large amounts of sensitive data in response may unintentionally cause data breaches or give attackers useful information for additional
- Absence of Rate Limiting: APIs that do not have appropriate rate limiting measures in place are vulnerable to resource depletion assaults, denial-of-service (DoS) attacks, and brute- force attacks.
- API Abuse or Misuse: Developers may not have meant for APIs to be exploited for purposes such as data scraping, getting around intended restrictions, or carrying out illicit
- Insecure API Composition: If an API is not adequately protected or vetted, it may inherit or contribute vulnerabilities from other APIs that it integrates or composes.
- Developers and security experts may more effectively use Postman AI to prioritize and focus their security testing efforts by being aware of these prevalent API security flaws.
API Security Testing with Postman AI
A variety of features and functionalities provided by Postman AI may be utilized to improve and automate API security testing. The usage of Postman AI to check for several API security flaws is covered in this section.
Testing for Broken Authentication
Broken authentication is a critical vulnerability that can lead to unauthorized access to APIs and the data they handle. Postman AI can be used to automate testing for broken authentication by generating test cases and scripts that simulate various authentication scenarios.
- Create Authentication Test Cases: Using the API specification or already-existing queries as a guide, Postman AI may create test cases for authentication endpoints. Various circumstances, including valid and incorrect credentials, expired tokens, and missing or faulty authentication headers, can be covered by these test cases.
- Script Authentication Creation: Postman AI has the ability to produce scripts (in Python and JavaScript, for example) that automate the authentication process and mimic various attack These scripts can be used for different testing needs or incorporated into Postman collections.
- Examine Authentication Answers: Using Postman AI, you can examine authentication endpoint answers to find possible security flaws including poorly generated tokens, unsafe password storage, or improper session
- TestingforBrute-ForceAttacks: Postman AI may be used to create and run scripts for brute-force attacks, which are intended to assess how resilient authentication systems are against assaults that include guessing passwords or stuffing
Testing for Broken Access Control
Vulnerabilities in access control can let unwanted individuals or systems access private information or use the API to carry out illegal operations. By creating test cases and scripts that mimic different access control circumstances, Postman AI may help with testing for failed access control.
- Create Access Control Test Cases: Postman AI is able to create test cases for endpoints that need certain permissions or rules for access control. These test cases can include things like trying to access resources that are not permitted, checking for unsecured direct object references, and accessing resources with inadequate permissions.
- Write Access Control Scripts: Postman AI can write scripts that mimic various access control scenarios, like trying to access resources with varying user roles or permissions, checking for privilege escalation both vertically and horizontally, and trying to get around access control
- AnalyzeAccessControlReplies: Postman AI is capable of analyzing access control endpoint replies to identify possible security flaws such unsecured direct object references, inconsistent access control enforcement, and information
- Automated Privilege Escalation Testing: To evaluate the strength of the access control controls, Postman AI may be used to create and run scripts that try to escalate privileges or carry out unwanted actions.
Testing for Injection Vulnerabilities
Injection vulnerabilities can result in data breaches or unauthorized access to systems. Examples of these vulnerabilities are SQL injection, NoSQL injection, and command injection. By creating test cases and scripts that mimic different injection attack situations, Postman AI may help with injection vulnerability testing.
- Create Injection Test Cases: Postman AI has the ability to create test cases for endpoints—like search fields, login forms, and query parameters-that take user input. Payloads and code snippets intended to test for various kinds of injection vulnerabilities may be included in these test cases.
- Write Injection Scripts: Postman AI has the ability to write scripts that will deliver different injection payloads to the API endpoints automatically. These scripts are adaptable to test for several types of injection vulnerabilities, including command injection, NoSQL injection, and SQL
- Examine Injection Replies: Postman AI has the ability to examine API endpoint replies in order to identify any possible injection vulnerabilities. Analyzing error messages, response codes, and response content for indications of successful injection attacks is one way to do this.
- Automated Payload Generation: In order to lessen the need on predefined payload lists, Postman AI may be used to create bespoke payloads and injection attack routes based on the API structure, data types, and expected answers.
- Integration with Vulnerability Scanners: By integrating Postman AI with already available security tools and vulnerability scanners, a holistic testing strategy that integrates automated injection testing with other security testing methods is made possible.
Testing for Insecure Cryptography
Data transferred using APIs may be compromised in terms of integrity and confidentiality if insecure encryption is used. Using simulations of different attack scenarios and analysis of cryptographic implementations, Postman AI may be used to test for insecure encryption.
- Examine Cryptography Algorithms: Postman AI is capable of examining the cryptographic techniques that the API use to encrypt and decode data. When weak or antiquated algorithms are being used, it may detect them and suggest stronger, more secure
- Test KeyManagement: To test the API’s key management procedures, including key generation, key rotation, and key storage methods, Postman AI may produce test cases and
- To assess the resilience of the cryptographic implementations in the API, Postman AI may provide scripts that mimic a variety of cryptographic attacks, including side-channel, brute-force, and padding oracle attacks.
- Examine Data Transmission Security: Using weak or antiquated SSL/TLS protocols, unencrypted communication routes, and other possible vulnerabilities can be found by Postman AI. It can also examine the security of data transmission between the client and the
- Integration with Cryptographic Libraries: Postman AI is compatible with a variety of cryptographic tools and libraries, allowing for automated testing of cryptographic implementations and the provision of information about any setup errors or vulnerabilities.
Testing for Security Misconfiguration

Vulnerabilities in APIs can be caused by security misconfigurations, such as obsolete software versions, unsafe default setups, and the activation of needless services or features. By examining API setups and producing pertinent test cases, Postman AI may help find and validate security misconfigurations.
- Examine API Configurations: Using Postman AI, you may examine the server configurations, headers, and response metadata of an API to find any possible security misconfigurations, such unsecured HTTP headers, out-of- date software versions, or activated features that aren’t really
- Create Configuration Test Cases: Postman AI has the ability to create test cases with the express purpose of looking for security configuration errors. These test cases can mimic a number of scenarios, such checking for out-of-date software versions, testing for unsafe default configurations, or trying to reach pointless or exposed endpoints.
- Combine with Configuration Management Systems: Postman AI may be used with infrastructure-as-code platforms and configuration management systems to facilitate automated testing and validation of API setups throughout the deployment and maintenance stages.
- Automated Configuration Hardening: Postman AI is capable of making suggestions for secure default settings and hardening API setups by utilizing industry best practices and security guidelines.
- Integration with Vulnerability Scanners: Postman AI may be used with security tools and vulnerability scanners to do thorough security testing by integrating configuration analysis with other testing methods like penetration testing and vulnerability scanning.
Testing for Insufficient Logging and Monitoring
Inadequate logging and monitoring systems may make it more difficult to identify and look into security problems or unusual API behavior. By examining API answers and creating test cases to verify logging and monitoring capabilities, Postman AI may help with testing for inadequate logging and monitoring.
- Examine API answers for Logging: Using Postman AI, you may examine API answers to find possible problems with logging, such insufficient or missing log entries, exposed sensitive material in logs, or insufficient recording of important events.
- Create Logging Test Cases: Using Postman AI, it is possible to create test cases that are intended to verify the logging and monitoring features of the API. These test cases can mimic a number of circumstances, such making illegal requests, initiating error conditions, or sending faulty requests, and they can then examine the associated log entries.
- Integrate with Log Management solutions: By integrating Postman AI with SIEM (Security Information and Event Management) systems and log management solutions, you can automate the testing and validation of API logging and monitoring features inside your home logging
- Automated Anomaly Detection: Using scripts created by Postman AI, one may evaluate the capacity of the API’s monitoring systems to identify and notify users of unusual activity or possible attack scenarios.
- Integration with Security Monitoring Tools: Postman AI may be used with intrusion detection systems and security monitoring tools to provide thorough testing of the logging and monitoring capabilities of the API in addition to other security monitoring measures.
These are just a few instances of how API security testing may be facilitated by Postman AI. Additional methodologies and integrations can be investigated to improve the security testing process, contingent upon the particular needs and vulnerabilities being addressed.
Advantages and Limitations of Using Postman AI for API Security Testing
While Postman AI has several advantages for improving and automating API security testing, it is important to weigh these benefits against its drawbacks in order to assure dependable and efficient testing.
Advantages
- Efficiency & Automation: Postman AI reduces the time and effort needed for manual testing by automating a number of API security testing processes. Better security coverage is produced by the more frequent and thorough testing made possible by this enhanced
- Postman AI’s intelligent test generation feature reduces the likelihood of missing important test situations by generating test cases and scripts based on the API specification or previously sent This approach allows for more comprehensive and focused testing.
- Integration with Current Tools: Postman AI enables a thorough and efficient security testing strategy by integrating with vulnerability scanners, monitoring systems, and other security testing tools.
- Continuous Integration and Continuous Deployment (CI/ CD) Pipelines may use Postman AI to facilitate continuous security testing and monitoring at every stage of the software development lifecycle.
- Natural Language Interaction: Postman AI’s ability to query in natural language makes it easier for non-technical people to use and facilitates communication between security experts, testers, and developers.
- Learning and Improvement: Postman AI may learn from data and comments it gets and enhance its skills as it is used more widely. This might eventually result in more precise and efficient security

Limitations
- Accuracy & False Positives: Although Postman AI strives to offer pertinent and accurate security testing insights, it is possible for missing vulnerabilities or false positives to occur, particularly in intricate or dynamic API
- Dependency on API Specifications: Postman AI’s efficacy may be constrained by the completeness and quality of the API specifications or by requests that are already in existence and are utilized to generate scripts and test cases. Testing may be insufficient or ineffective as a result of inaccurate or incomplete
- Integration Challenges: Compatibility problems or complexity may arise when integrating Postman AI with current security solutions, monitoring systems, and CI/CD This will likely need extra work and configuration.
- Data Privacy and Security: It is essential to make sure that appropriate data privacy and security safeguards are in place to safeguard sensitive information when Postman AI processes API data and
- Maintenance and Updates: Regular maintenance and updates may be necessary to keep Postman AI abreast on the most recent security flaws, attack vectors, and best practices. This may result in an ongoing operating overhead.
- Limited Customization: Although Postman AI has many features, there can be restrictions on how they can be altered or expanded to satisfy particular or sophisticated security testing needs.
It is advised to take the following actions to lessen these restrictions and guarantee efficient API security testing with Postman AI:
- Develop a thorough security testing plan that include manual checks, Postman AI, and more testing
- To guarantee accurate and comprehensive test case generation, periodically evaluate and update API requirements and open
- When handling sensitive API specifications and data using Postman AI, make sure appropriate data privacy and security protections are in place.
- Keep an eye on Postman AI and keep it updated with the newest security flaws, attack methods, and best
- To strengthen Postman AI’s powers and make up for its shortcomings, think about combining it with additional security testing instruments and vulnerability
- Give developers, testers, and security experts the necessary guidance and assistance so they can use Postman AI for API security testing
- Organizations may decide whether to use Postman AI for API security testing and guarantee its successful integration into their entire security testing strategy by being aware of these benefits and drawbacks and taking appropriate
Best Practices for Effective API Security Testing with Postman AI
It is crucial to adhere to best practices and integrate Postman AI into an all-encompassing security testing plan in order to optimize the advantages of utilizing Postman AI for API security testing and minimize any potential drawbacks. The following are some suggested best practices:
- For Postman AI to provide precise and useful test cases and scripts, clear and detailed API requirements are essential. To reflect modifications to the API’s structure, data types, and anticipated replies, specifications should be updated and maintained on a regular basis.
- Postman AI can automate a number of API security testing tasks, but for a more thorough testing strategy, it should be combined with vulnerability scanners and other security testing This connection can offer further security insights and assist in locating problems that Postman AI might overlook.
- Throughout the software development lifecycle, continuous security testing and monitoring may be made possible by integrating Postman AI into CI/CD pipelines. This method lowers the possibility of vulnerabilities entering production systems by ensuring that API security flaws are found and fixed
- Secure coding techniques and secure software development lifecycle (SSDLC) procedures should be used in addition to security testing, even if the latter is To lessen the possibility of creating vulnerabilities in the first place, developers should undergo training on safe coding techniques, input validation, and secure API architecture.
- As new security vulnerabilities and attack vectors emerge, it is crucial to keep Postman AI up to date with the latest security information and best practices. This may involve updating Postman AI with new test cases, scripts, or integrations with security tools and vulnerability databases.
- When using Postman AI for API security testing, it is essential to implement proper data privacy and security measures to protect sensitive API data and This may include encryption, access controls, and secure storage mechanisms.
- Developers, testers, and security experts must work together and share expertise in order to conduct effective API security Encouraging open communication, information sharing, and cross-functional cooperation can result in improved API security overall and more effective security testing techniques.
- Given how APIs and their security needs change over time, testing for API security should be a continuous effort. To find and fix fresh flaws or modifications to the security environment, it is necessary to conduct ongoing monitoring and auditing of API security.
- Organizations may successfully utilize the capabilities of Postman AI while reducing its limits and guaranteeing strong API security by adhering to these best practices and integrating the tool into a thorough security testing
Conclusion
Because they provide smooth data interchange and communication across various services and apps, application programming interfaces (APIs) have grown in importance in today’s software systems. On the other hand, unreliable APIs can provide serious security issues, including the possibility of data breaches, illegal access, and other security events. To reduce these vulnerabilities, thorough testing is necessary to ensure API security.
AI-powered capabilities in Postman AI, a potent tool for API development and testing, can automate and improve a number of API security testing tasks. Developers and security experts can quickly test for common API security flaws like improper authentication, improper access control, injection vulnerabilities, insecure cryptography, security misconfigurations, and inadequate logging and monitoring by utilizing Postman AI’s capabilities.
Postman AI has several benefits, including as intelligent test creation, automation, and interaction with current tools; nevertheless, it has some limits that must be recognized and addressed. Potential errors, dependence on API standards, difficulties integrating, worries about data security and privacy, maintenance needs, and constrained customizability are a few examples of these restrictions.
Developing strong API specifications, integrating with vulnerability scanners and security tools, implementing continuous integration and deployment (CI/CD), establishing secure coding practices, routinely updating and maintaining Postman AI, putting in place appropriate data privacy and security measures, encouraging collaboration and knowledge sharing, and continuously monitoring and auditing API security are all best practices that organizations should adhere to in order to use Postman AI for API security testing in an efficient manner.
Organizations can improve their API security posture, lower the risk of security incidents, and guarantee the confidentiality, integrity, and availability of their applications and data by implementing a thorough security testing strategy that includes Postman AI in addition to other testing techniques, manual reviews, and secure development practices.
In addition to investigating new methods for automating complex security testing scenarios and integrating with cutting-edge security frameworks and technologies, future research and development in the field of AI-powered API security testing may concentrate on enhancing the precision and adaptability of solutions such as Postman AI [2-10].
References
- (2024) Postman: The Collaborative Platform for API Postman https://www.postman.com/.
- (2024) OWASP API Security Project. OWASP https://owasp.org/www-project-api-security/.
- Vieira M, Antunes N, Madeira H (2009) Using Web Security Scanners to Detect Vulnerabilities in Web Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) 566-571.
- Shar J, Tan B (2012) Defending Against Injection Attacks Through Context-Sensitive String Evaluation. Proceedings of the International Conference on Recent Advances in Intrusion Detection (RAID) 124-145.
- Stuttard D, Pinto M (2011) The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws 2nd ed. Wiley Publishing https://edu.anarcho-copy.org/Against%20Security%20-%20Self%20Security/Dafydd%20Stuttard,%20 Marcus%20Pinto%20-%20The%20web%20application%20 hacker ’s%20handbook_%20finding%20and%20 exploiting%20security%20flaws-Wiley%20(2011).pdf.
- Nataliia Neshenko, Elias Bou-Harb, Jorge Crichigno, Georges Kaddoum, Nasir Ghani, et al. (2019) Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Communications Surveys & Tutorials 21: 2703-2740.
- Doupé A, Cova M, Vigna G (2010) Why Johnny Can’t Pentest: An Analysis of Black-Box Web Vulnerability Scanners. Proceedings of the International Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA) 111-131.
- Challoo R, Chana R, Singh J (2019) Continuous Integration and Continuous Delivery in Web Applications. Proceedings of the International Conference on Inventive Computation Technologies (ICICT) 441-446.
- Anjana M, Basu S (2019) Secure Software Development Life Cycle: An Overview. Proceedings of the International Conference on Advanced Computing and Communication Systems (ICACCS) 1052-1057.
- Scholte T (2018) An Empirical Study of API Governance and Proceedings of the IEEE International Conference on Software Analysis, Evolution and Reengineering (SANER) 211-221.
View PDF






