Author(s): Girish Ganachari and Rameshbabu Lakshmanasamy
The analysis of this paper focuses on AWS IAM, Amazon Cognito, and External Solutions for Authentication and Authorization of Cloud Services. It
determines its usage, advantages, and disadvantages as well as possible advancements in the future that may enhance cybersecurity; and the necessity for the construction of improved security systems in the face of increasing global threats.
The need to adopt cloud security cannot be overemphasized in the present world that has been dominated by the advent of cloud technology. As organizations gradually transition their operations to cloud services, the need to safeguard information becomes necessary to ensure authorized access. The protection of information systems is important as it helps to protect against threats such as computer vandalism, theft, structural minds, and data diddle, thereby protecting the integrity and confidentiality of the data.
The research adopted a comparative and SWOT analysis to determine the effectiveness of AWS IAM, Amazon Cognito, and top-tier solutions. The comparison between the two frameworks was on the capability, security, and efficiency of the two frameworks [1]. The SWOT analysis was found useful in that it could be used not only to define the internal and external strengths and weaknesses of an organization in terms of security but also in defining the opportunities and threats with the use of these frameworks. Thus, having considered the survey of different methodologies which are to solve the problem, advantages and the disadvantages of each of the solutions were considered. These studies informed their use and the possibility of improvement through such procedures according to other workers [2].
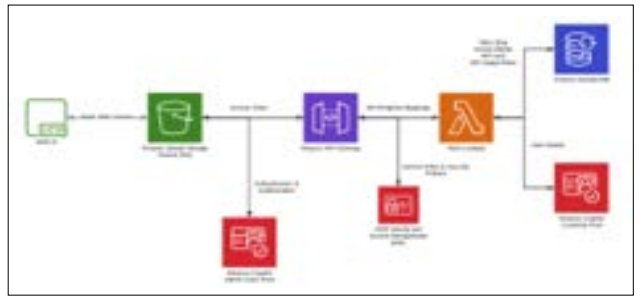
Figure 1: Overall Application Architecture
AWS IAM is massively used in various industries to enhance the security of the cloud by regulating user access and privileges. In the world of finance, Identity and Access Management (IAM) ensures that only the right person opens the door to restricted financial data and transacts on behalf of the firm [3]. IAM is used in healthcare organizations for compliance with certain standards such as HIPAA among others.
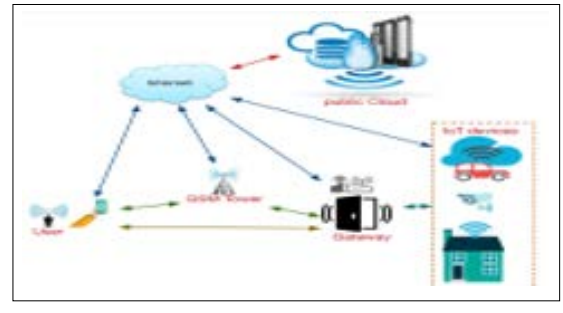
Figure 2: A High-Level System Model
Amazon Cognito is an important tool that should be used to secure applications with strict user authentication requirements for Internet-based web and mobile applications. They can easily implement the functionalities of user registration, login, and access control allowing smooth and secure user administration [4]. Appropriate for applications that require integration with social nets, authentication is provided by Facebook, Google, and other providers. Cognito is used to manage customer accounts for members of e-commerce platforms to provide an efficient purchase process when protecting clients’ information.
IAM is often used in conjunction with AWS IAM and Cognito, both external solutions, for enhanced security measures. Okta and Auth0 are both application software that deals with intricate solutions to Multi-Factor Authentication and Single Sign-On solutions [5]. These features are added to increment on the current gains to AWS services to even further. These interfaces are very beneficial for any organization that needs extra protection measures or that is answerable for entry to a few cloud systems [6].
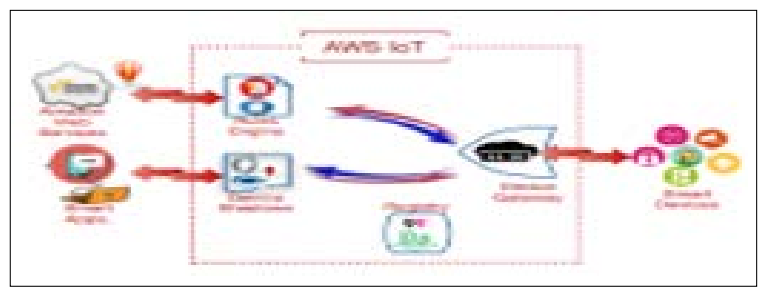
Figure 3: AWS IoT Architecture
Analyzing the work of AWS IAM together with Amazon Cognito with regard to aspects of security and compliance, their advantages are evident. IAM also provides efficient measures for access control that allows only the approved people to access certain materials and discourages intruders as well as data leakage [7]. Campus, this framework assists in achieving compliance with many legal mandates including but not limited to the GDPR and HIPAA because it has detailed access logs as well as audited measures. Amazon Cognito promotes security and has features as MFA and secure user authentication implemented. These are essential for security and as per to the parameters that are expected in protecting of the users data.
Amazon IAM service and Amazon Cognito also help in managing users by providing centralized control of user identity and access [8]. IAM enables the administrators to set fine-grained control measurements thus ensuring that the users have only the necessary level of authorization required for their tasks within the organization [9]. This centralized management reduces the amount of administrative processing needed and enhances security because fewer points can be attacked in the process [10].
The modularity and adaptability of AWS IAM and Amazon Cognito translate into significant advantages for any scale of organization. IAM is built to incorporate an organization’s growth, meaning more users and resources can be integrated while maintaining maximum security [11]. Due to the objective, the possibility of using the system is vast, and the integration of AWS can easily be connected with other services. Like most AWS services, Amazon Cognito has outstanding high availability, the performance increases with the number of users and their requests [12].
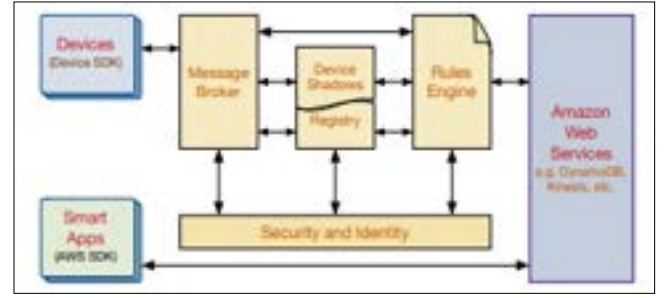
Figure.4: AWS IoT Security Mechanism
The major difficulty in the case of the implementation of AWS IAM and Amazon Cognito is like these services. Therefore, efficient configuration of IAM policies requires a detailed understanding of AWS services and their relationships [23]. Incorrect configurations may lead to various security issues or an overly restrictive environment which is disadvantageous for the functioning of the infrastructure [14].
It is important to note that despite having great features, AWS IAM and Amazon Cognito have certain drawbacks. IAM is a relatively sound industry framework but is complex for handling thousands of users and roles, primarily because of issues in scalability [15]. It is a limited system that lacks certain elements of the more complex identity solutions, some of which include detailed reporting [16]. Amazon Cognito is great for user authentication but lacks some freedom in terms of customizability [17].
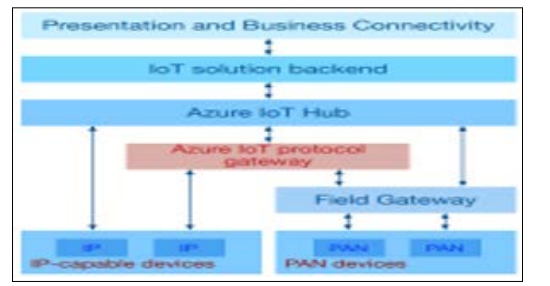
Figure.5: Azure IoT Architecture
The use of supplementary other solutions along with AWS IAM and Cognito introduces additional risks. While these solutions can increase the level of security and usefulness, they also enhance the attack possibilities [18]. Thirdly, the herein management of more security technologies can be cumbersome and result in integration problems in the security infrastructure [22].
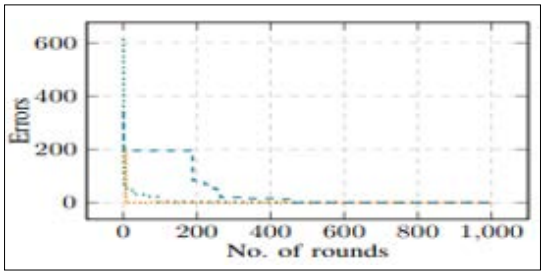
Figure.6: Errors in Constructing Flow Graphs Using Traces from Many Rounds
Several emerging trends are defining the future of secure authentication and authorization settings for AWS cloud solutions [19]. One of the trends is the increase in the adoption of zero- trust security frameworks that assume that threats can come from outside and inside the organization [20]. This method requires constant validation.
This development is expected to take place with AWS IAM and Amazon Cognito since these programs have been found to have some limitations in meeting the needs that come with complex environments [21]. Some potential options for IAM improvement may include the introduction of some methods of policy policies, easy to use, and the inclusion of scalability mechanisms to deal with a large number of users and roles [22]. Anticipated improvements include improvements in customization possibilities that will allow Amazon Cognito to flexibly interface with third-party and older systems easily.
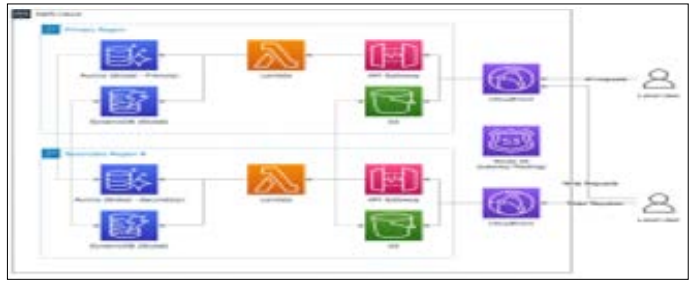
Figure.7: AWS exists within One Region
External solutions will therefore continue to offer new and advanced security solutions that offer more value-added services to those offered by AWS [23]. Future development can include the integration of more complex user authentication techniques that are biometric validation and behavioral genetics in the procedure of identity validation [24]. It can be stated that external service providers would improve their knowledge of how to provide multiple layers of security and integrate the AWS services hence improving the connection’s security and fluency [25,26].
The analysis of AWS IAM, Amazon Cognito, and third-party services shows the opportunities and challenges of the mentioned frameworks in providing secure authentication and authorization accordingly.
