Author(s): Pavan Navandar
In today’s interconnected digital landscape, securing applications and data against cyber threats is paramount. SAP Business Technology Platform (BTP) offers a robust solution for managing cloud applications, and at its core lies the SAP BTP Cockpit, a centralized hub for application management and monitoring. This white paper delves into the significance of role-based access control (RBAC) in SAP BTP Cockpit, elucidating its role in safeguarding applications and data, and providing insights into best practices for implementing RBAC effectively.
In the current rapidly evolving business landscape, organizations face unprecedented challenges and opportunities driven by digital disruption. SAP, a global leader in enterprise software solutions, recognizes the imperative for businesses to embrace digital transformation to thrive in this environment. SAP BTP emerges as a strategic enabler for organizations seeking to harness the power of advanced technologies such as cloud computing, analytics, machine learning, and IoT to fuel innovation and drive growth. At the core of SAP BTP lies the SAP BTP Cockpit, a unified management interface that empowers users to orchestrate and optimize their digital assets effectively.
As organizations increasingly rely on cloud-based applications to drive innovation and agility, the need for robust security measures becomes imperative. SAP BTP Cockpit serves as a central point for managing and monitoring applications deployed on SAP BTP, offering a range of tools and services to streamline operations. Role-based access control (RBAC) emerges as a fundamental component of SAP BTP Cockpit’s security framework, enabling organizations to enforce granular access controls and mitigate security risks effectively.
RBAC is a security model that restricts system access to authorized users based on their roles within an organization. It defines roles, permissions, and privileges associated with different user types, enabling fine-grained access control and least privilege principle.
Use the SAP BTP cockpit to create a role for a subscribed application using an existing role template. You can refine the role by assigning attributes and add the role-to-role collections.
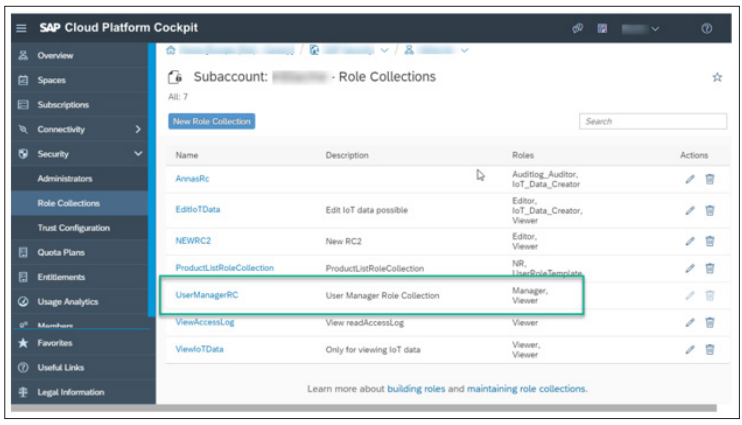
Roles: Roles define sets of permissions or access rights that are assigned to users based on their responsibilities within an organization.
Permissions: Permissions specify the actions or operations that users are allowed or denied performing within the system.
Privileges: Privileges refer to specific capabilities or resources that
users can access based on their assigned roles and permissions.
Granular Access Control: RBAC enables organizations to define and enforce granular access controls, restricting access to sensitive data and functionalities.
Simplified Administration: By organizing users into roles, RBAC simplifies user management and administration, reducing administrative overhead.
Enhanced Security: RBAC helps organizations mitigate security risks by ensuring that users only have access to the resources and functionalities necessary to perform their roles effectively.
Role Assignment: SAP BTP Cockpit allows administrators to define custom roles and assign specific permissions to users based on their responsibilities and job functions.
Permission Management: Administrators can manage permissions at a granular level, specifying access rights to various resources, services, and functionalities within SAP BTP Cockpit. Role Hierarchy: SAP BTP Cockpit supports role hierarchies, allowing for the inheritance of permissions from parent roles to child roles, simplifying role management and administration.
Audit Trails: SAP BTP Cockpit logs all user activities and changes to roles and permissions, providing administrators with comprehensive audit trails for compliance and security monitoring.
Best Practices for Implementing RBAC in SAP BTP Cockpit Define Clear Roles and Responsibilities: Identify and define roles based on organizational hierarchies and job functions, ensuring clarity and consistency in role assignments.
Limit Access to Least Privilege: Follow the principle of least privilege by granting users only the permissions necessary to perform their roles, minimizing the risk of unauthorized access. Regular Review and Updates: Conduct regular reviews of roles and permissions to ensure alignment with organizational changes and evolving security requirements.
User Training and Awareness: Provide training and awareness programs to educate users about their roles and responsibilities regarding security practices and RBAC policies.
Role-based access control (RBAC) plays a pivotal role in ensuring the security and integrity of applications deployed on SAP BTP Cockpit. By defining clear roles, managing permissions granularly, and adhering to best practices, organizations can effectively mitigate security risks and safeguard their applications and data against unauthorized access and cyber threats. As organizations continue to embrace cloud technologies for digital transformation, RBAC remains a cornerstone of robust security frameworks, enabling organizations to stay resilient and secure in the face of evolving cyber threats [1-7].
