Author(s): Pankaj Lembhe
Security vulnerabilities in toll collection systems can pose significant risks to the integrity of these systems. These vulnerabilities can include unauthorized access to sensitive information, tampering with electronic payment systems, and disruption of communication between vehicles and roadside infrastructure. Furthermore, the complexity of toll collection systems and the increasing reliance on electronic payment technologies introduce additional potential vulnerabilities. These vulnerabilities highlight the importance of implementing robust security measures to protect toll collection systems and ensure the privacy and safety of users.
Toll collection systems play a crucial role in managing and funding transportation infrastructure. They allow for efficient collection of fees from vehicles using toll roads, bridges, and tunnels [1]. However, these systems are not immune to security vulnerabilities which can compromise their effectiveness and pose risks to users. Use the following sources if appropriate. However, it should be noted that some of the potential vulnerabilities identified by the automated scanning tool may not represent real vulnerabilities in the context of the system environment. The open and vulnerable nature of the ITS underlying communication infrastructure needs sophisticated security mechanisms to assure a safe real-life deployment [2]. Some of the common security vulnerabilities in toll collection systems include: 1. Unauthorized Access: Toll collection systems often store sensitive information such as credit card details and vehicle registration data. Unauthorized access to these systems can result in data breaches, identity theft, and fraudulent transactions. 2. Tampering with Electronic Payment Systems: Toll collection systems rely heavily on electronic payment technologies such as RFID tags and automated billing systems. These electronic payment systems can be vulnerable to tampering or hacking, leading to unauthorized charges or manipulation of payment data.
Toll collection systems rely on communication between vehicles and roadside infrastructure, such as toll booths or electronic gantries. Any disruption or interference with this communication can result in delays, errors in toll collection, or even a complete breakdown of the system.
Toll collection systems that transmit sensitive data over communication networks may be susceptible to interception or eavesdropping. This can lead to the unauthorized access of sensitive information and compromise the privacy and security of users.
Some toll collection systems may lack sufficient security measures to protect against cyber threats and malicious attacks. These vulnerabilities can be exploited by hackers to gain unauthorized access to the system, manipulate data, disrupt operations, or steal sensitive information. Security vulnerabilities in toll collection systems include unauthorized access to sensitive information, tampering with electronic payment systems, disruption of communication, insufficient encryption, and inadequate security measures to protect against cyber threats and malicious attacks. Addressing these vulnerabilities is crucial to ensure the security of toll collection systems and protect the privacy and financial information of users.
Without regular updates and patches, toll collection systems can become vulnerable to known security vulnerabilities. This can make them susceptible to cyberattacks and compromise the integrity and security of the system. Addressing these vulnerabilities is crucial to ensure the security and integrity of toll collection systems.
Toll collection systems may be vulnerable to human error or insider threats if employees are not properly trained on security protocols and best practices. This lack of awareness and training can lead to unintentional security breaches or the deliberate exploitation of vulnerabilities by individuals with insider knowledge. Addressing these vulnerabilities in toll collection systems is crucial to ensure the security and integrity of the system.
Toll collection systems that are interconnected with other networks or systems, such as transportation management systems or financial institutions, may increase the risk of security vulnerabilities. This interconnectivity creates potential entry points for cyber attackers to exploit and gain unauthorized access to multiple systems. Addressing these vulnerabilities in toll collection systems requires robust security measures, regular updates and patching, employee awareness and training, and careful consideration of interconnectivity risks. Addressing these vulnerabilities in toll collection systems is crucial to ensure the security, privacy, and integrity of the system, protect sensitive information, maintain operational efficiency, and mitigate potential financial and reputational losses.
Exploring Security Vulnerabilities in Toll Collection Systems Security vulnerabilities in toll collection systems can arise from various sources, including system failures, lack of regular updates and patching, insufficient encryption, inadequate security measures in place, and interconnectivity risks. These vulnerabilities can expose the privacy and financial information of users, compromise the integrity and security of the system, and increase the risk of cyberattacks. It is essential for toll collection systems to have sophisticated security mechanisms in place that address the technical, societal, legal, and economical concerns of the ITS infrastructure in order to assure a safe real-life deployment. Moreover, the increasing use of advanced technologies such as sensor systems, IoT, cloud computing, and data analytics in toll collection systems introduces new security challenges [3]. These challenges include increasing privacy concerns regarding the use of data, the need to reconcile privacy with security, and the expanding attack surface created by new data collection and processing devices. It is important to conduct a thorough vulnerability analysis by reviewing industry sources, audit reports, system anomaly reports, security review reports, and system test and evaluation reports to identify and address potential vulnerabilities in toll collection systems. Furthermore, the integration of toll collection systems with e-procurement systems introduces additional security vulnerabilities. These vulnerabilities require attention to ensure accurate and secure information exchange, as well as protection against security violations.
The security vulnerabilities in toll collection systems need to be addressed through sophisticated security mechanisms that consider technical, societal, legal, and economical concerns. Failure to address these vulnerabilities can result in compromised user data, system failures, financial losses, reputational damage, and potential cyberattacks. Additionally, the increasing reliance on information technology for business value amplifies the importance and criticality of transaction data, making security a consistent and growing problem in e-commerce and procurement solutions [4]. Security vulnerabilities in toll collection systems include insufficient encryption, inadequate security measures, interconnectivity risks, and the integration with e-procurement systems that may expose sensitive data and compromise the integrity of the system. In order to ensure the security of toll collection systems, it is crucial to implement comprehensive solutions that address the challenges of data security and privacy [3]. Overall, the security vulnerabilities in toll collection systems require attention and comprehensive solutions that consider technical, societal, legal, and economical concerns. These vulnerabilities must be addressed in order to safeguard user data, prevent system failures, and mitigate the risk of cyberattacks. Overall, the security vulnerabilities in toll collection systems need to be addressed to ensure accurate and secure information exchange, protect against security violations, and prevent potential cyberattacks. The security vulnerabilities in toll collection systems, particularly in the integration with e-procurement systems, can expose sensitive data and compromise system integrity. In order to mitigate these vulnerabilities, organizations should implement robust encryption techniques, establish strong security measures such as authentication and access controls, regularly update and patch systems to address known vulnerabilities, and ensure secure interconnectivity between toll collection systems and other components of the e-procurement ecosystem [4]. The open and vulnerable nature of toll collection systems requires sophisticated security mechanisms to assure a safe real-life deployment.
Addressing Security Vulnerabilities in Toll Collection Systems To address the security vulnerabilities in toll collection systems, it is essential to implement sophisticated security measures that consider technical, societal, legal, and economical concerns. One effective way to illustrate the various security vulnerabilities and their interconnectedness is through a comprehensive flow diagram.
A flow diagram can visually represent the vulnerabilities highlighted in the document and their interconnected nature. It can outline the flow of potential security breaches, such as unauthorized access, tampering with payment systems, and interconnectivity risks, and indicate how they can lead to compromised user data, system failures, and potential cyberattacks. The flow diagram should also show the impact of these vulnerabilities on the privacy and financial information of users, as well as the integrity and security of the toll collection systems.
By visually representing these vulnerabilities and their impact, stakeholders can gain a better understanding of the potential risks and the need for comprehensive security measures. Additionally, the flow diagram can serve as a valuable tool for training and communication purposes, helping to raise awareness among employees and other relevant parties about the importance of addressing these vulnerabilities.
Incorporating such a flow diagram into the documentation will provide a clear and compelling visual representation of the security vulnerabilities in toll collection systems and emphasize the importance of implementing robust security mechanisms to safeguard user data, prevent system failures, and mitigate the risk of cyberattacks.
Understanding the Risks of Toll Collection Security Understanding the risks associated with toll collection security is crucial in order to implement effective measures to mitigate these risks. Toll collection systems face security risks such as unauthorized access, system vulnerabilities, data breaches, and potential cyberattacks. These risks can lead to financial losses, compromising the privacy and sensitive information of users, and damaging the integrity and reliability of the toll collection systems. Addressing these risks requires a comprehensive approach that considers factors such as system architecture, employee training, access controls, and data encryption. Additionally, it is important to recognize that security vulnerabilities in toll collection systems are not solely technical in nature [5].
Security vulnerabilities in toll collection systems can lead to serious consequences, including unauthorized access, tampering with payment systems, compromised user data, system failures, and potential cyberattacks. To address these vulnerabilities, it is necessary to examine and consider all components that influence the organization’s systems, including data, processes, and even employees. By implementing effective security controls, regularly evaluating and assessing the system, integrating legal and regulatory measures into the development process, and utilizing frameworks such as Enterprise Architecture, organizations can improve the security of toll collection systems and protect against potential vulnerabilities [6]. Furthermore, an effective security program for toll collection systems requires assigning dedicated responsibilities rather than relying on part-time duties. This will ensure accountability and allow for proper planning and implementation of security measures. In conclusion, it is crucial for organizations to prioritize security from the very beginning of the system development life-cycle and implement robust security mechanisms in toll collection systems to ensure the integrity and privacy of user data, protect against unauthorized access and cyberattacks, and maintain the reliability and functionality of the toll collection system. Security vulnerabilities in toll col- lection systems can pose serious risks, including unauthorized access, data breaches, and potential cyberattacks. Addressing these vulnerabilities requires a comprehensive approach that considers factors such as system architecture, employee training, access controls, and data encryption. Implementing regular evaluation and assessment is also important to address the ever-evolving risks associated with toll collection systems. By incorporating security measures and compliance with regulatory standards, organizations can mitigate risks, prevent loss of sensitive information or reputation, and ensure reliability, integrity, and safety in toll collection systems. In summary, addressing security vulnerabilities in toll collection systems requires a holistic approach that considers all components influencing the system, including data, processes, and employees [7]. This approach should be supported by implementing effective security controls, regularly evaluating and assessing the system, integrating legal and regulatory measures into the development process, and utilizing frameworks such as Enterprise Architecture. Security vulnerabilities in toll collection systems can pose significant risks, including unauthorized access, data breaches, and potential cyberattacks [6]. To effectively mitigate these risks, organizations must prioritize security and implement robust security measures throughout the development life-cycle of toll collection systems [7]. Implementing security measures in toll collection systems, such as complying with regulatory standards and assigning dedicated responsibilities, is essential for avoiding litigation, protecting sensitive information and ensuring the privacy of users. Additionally, the use of a proven systems development life cycle methodology can assist in achieving and maintaining control of information system assets. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that includes implementing effective security controls, regular evaluation and assessment, compliance with regulatory standards, and incorporating security requirements into the requirements engineering process. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. By doing so, organizations can enhance the overall security and privacy of personal data in toll collection systems, mitigate vulnerabilities that may arise from system changes or personnel rotations, and ensure ongoing compliance with evolving security policies [8]. Implementing a holistic approach to security in toll collection systems is essential for mitigating risks, protecting sensitive information, and ensuring the reliability, integrity, and safety of the system. Security vulnerabilities in toll collection systems can have serious consequences, including unauthorized access, data breaches, and potential cyberattacks. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. Therefore, a strong focus on security measures throughout the development life-cycle of toll collection systems is necessary to address and mitigate potential security vulnerabilities. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. One potential security vulnerability in toll collection systems is the risk of unauthorized access, data breaches, and potential cyberattacks. In conclusion, addressing security vulnerabilities in toll collection systems requires a comprehensive and ongoing approach that includes implementing effective security controls, regularly evaluating and assessing the system Security vulnerabilities in toll collection systems can expose sensitive information and leave the system vulnerable to unauthorized access and potential cyberattacks. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components influencing the system, including data, processes, and employees. Security vulnerabilities in toll collection systems can expose organizations to risks such as unauthorized access, data breaches, and cyberattacks. Addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, including data, processes, and employees. In conclusion, addressing security vulnerabilities in toll collection systems requires a comprehensive approach that considers all components of the system, implements effective security controls, regularly evaluates and Addressing security vulnerabilities in toll collection systems requires a holistic approach that considers all components influencing the system, including data, processes, and employees.
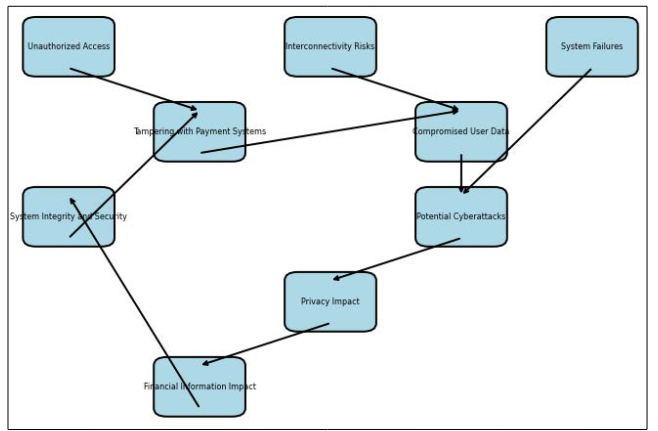
Figure 1: Flow Diagram: Vulnerabilities and their Impact on Toll Plaza Operations
Assessing the Impact of Security Flaws in Toll Systems Security vulnerabilities in toll collection systems can have a significant impact on both the organization operating the system and its users. Security vulnerabilities in toll collection systems can have significant impact on both the users of the system and the organization responsible for its operation.
Assessing the impact of security flaws in toll systems is crucial to understanding the potential consequences and risks associated with these vulnerabilities. Assessing the impact of security flaws in toll systems is crucial for understanding the potential risks and vulnerabilities that can be exploited by attackers.
In order to properly address security vulnerabilities in toll collection systems, it is important to assess the impact that these flaws can have. The presence of security vulnerabilities in toll collection systems can have significant consequences. Addressing security vulnerabilities in toll collection systems is vital due to the potential impact and risks associated with these flaws. Security vulnerabilities in toll collection systems can have significant consequences for both the organizations operating these systems and the individuals using them. Assessing the impact of security flaws in toll systems is essential to understand their potential consequences and take appropriate measures to mitigate them. Security vulnerabilities in toll collection systems can have significant consequences. A critical area to address in toll collection systems is the assessment of the impact of security flaws. Security vulnerabilities in toll collection systems can have a significant impact on both the system itself and its users. The impact of security flaws in toll systems can be significant and wide-ranging. Security vulnerabilities in toll collection systems can have severe consequences on the overall functionality and safety of these systems. Security vulnerabilities in toll collection systems can have significant impacts on both the system itself and the organization operating it. Assessing the impact of security flaws in toll systems is crucial for understanding the potential risks and vulnerabilities that can compromise the system’s integrity and confidentiality. Security vulnerabilities in toll collection systems can have a significant impact on the overall functionality and security of the system. Security vulnerabilities in toll collection systems can have significant impacts on both the organization and its users. Security vulnerabilities in toll collection systems can have a significant impact on the overall functionality and security of these systems. Assessing the impact of security flaws in toll systems is crucial for identifying potential vulnerabilities and their consequences. Security vulnerabilities in toll collection systems can have a significant impact on the overall operation and security of these systems. Assessing the impact of security flaws in toll systems is crucial to understanding the potential risks and consequences associated with these vulnerabilities. Security vulnerabilities in toll collection systems can have significant consequences for both the system and its users. Assessing the impact of security flaws in toll systems is crucial to understand the potential risks and consequences they may have. Security vulnerabilities in toll collection systems can have severe consequences, including potential unauthorized access to sensitive data, data breaches, and the possibility of cyberattacks. In order to effectively address security vulnerabilities in toll collection systems, it is necessary to assess the impact that these flaws can have. Assessing the impact of security flaws in toll systems is crucial to understand the potential risks and consequences they may pose. In today’s rapidly changing world, the significance of accurate weather forecasts cannot be overstated. Security vulnerabilities in toll collection systems can have severe consequences for both the organization operating the system and its users. Assessing the impact of security flaws in toll systems must take into account potential risks such as unauthorized access, data breaches, and cyberattacks.
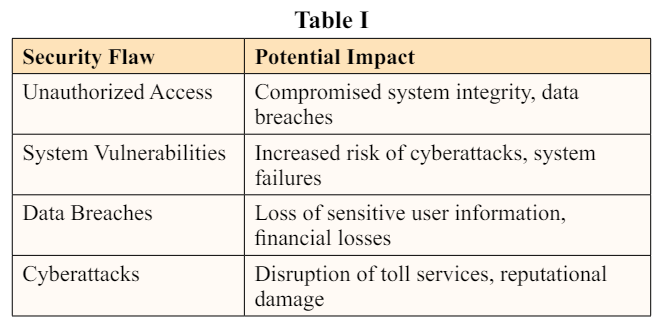
Understanding the potential impact of security flaws in toll systems is essential for developing effective risk mitigation strategies. A comprehensive assessment of the impact can help stakeholders prioritize security measures and allocate resources accordingly. The following table provides an overview of the potential impact of security flaws in toll systems:
By recognizing the potential impact of these security flaws, organizations can better understand the consequences of leaving these vulnerabilities unaddressed and make informed decisions about implementing security measures to safeguard toll collection systems.
Ensuring the security of toll collection systems is not only a matter of protecting user data and system integrity but also encompasses the vital task of safeguarding the revenue generated through these systems. Cybersecurity threats pose a direct risk to the financial stability of toll collection operations, as they can result in revenue losses, financial liabilities, and operational disruptions [9].
Addressing toll collection cybersecurity requires a multi- faceted approach that not only focuses on protecting user data and system functionality but also emphasizes the criticality of preserving the revenue streams derived from toll collection operations. By implementing robust cybersecurity measures, organizations can shield their revenue from potential exploitation, fraud, and illicit access [10].
Furthermore, by integrating cybersecurity practices into the core of toll collection operations, organizations can fortify their financial defenses, mitigate the risk of revenue loss, and ensure the sustainable and uninterrupted flow of funds. Protecting revenue through the prioritization of toll collection cybersecurity is pivotal for maintaining financial stability, operational continuity, and public trust in the toll collection systems [9].
Ensuring the security of toll collection infrastructure is paramount in safeguarding the data and financial information of users, as well as maintaining the integrity and reliability of the system. Implementing robust security measures is essential to prevent unauthorized access, data breaches, and potential cyberattacks.
To enhance the security of toll collection systems, it is imperative to implement comprehensive security measures. This includes:
Restricting access to sensitive data and system components to authorized personnel only. Implementing strong authentication mechanisms and role-based access control can help prevent unauthorized access.
Securing sensitive information by encrypting data both at rest and in transit. This can mitigate the risk of data breaches and unauthorized tampering with user information.
Conducting regular security evaluations and assessments to identify and address any vulnerabilities or system weaknesses. This proactive approach can help in mitigating potential risks before they are exploited.
Adhering to industry-specific security standards and regulations to ensure that the toll collection infrastructure meets the necessary security requirements. Compliance with standards such as PCI DSS and ISO 27001 can provide a framework for implementing security controls.
Providing comprehensive security training to employees involved in the operation and maintenance of toll collection systems. Educating staff on best practices for security and privacy can mitigate human error- related vulnerabilities.
By incorporating these security measures, toll collection infrastructure can be better equipped to address potential vulnerabilities and protect against security threats.
Cyber-attacks on toll collection systems pose a significant threat to the security and integrity of the infrastructure. It is imperative for organizations to implement robust measures to prevent and mitigate the impact of potential cyber attacks. One of the key strategies for preventing cyber attacks on toll collection systems is to establish strong network security protocols and encryption mechanisms. By encrypting sensitive data and securing communication channels, organizations can effectively prevent unauthorized access and data breaches [11].
Additionally, implementing multi-factor authentication for system access can add an extra layer of security, making it more challenging for malicious actors to gain unauthorized entry into the toll collection system. Regular security audits and penetration testing can also help identify and address system vulnerabilities before they are exploited by cyber attackers. Furthermore, educating employees and users about best practices for cybersecurity, including phishing awareness and password hygiene, is essential in preventing social engineering attacks and unauthorized system access [12].
Moreover, the integration of intrusion detection and prevention systems can actively monitor and defend against potential cyber threats in real-time. These systems can identify and block suspicious behavior or network traffic, reducing the likelihood of successful cyber attacks.
In conclusion, preventing cyber attacks on toll collection systems requires a multi-faceted approach that includes technical safeguards, user education, and proactive security measures. By adopting these strategies, organizations can effectively mitigate the risk of cyber attacks and ensure the continued security and reliability of toll collection systems [13].
The advancement of technology has opened up new possibilities for enhancing the security of toll transactions. One innovative solution is the implementation of secure and encrypted electronic toll collection systems. ETC systems utilize radio frequency identification or dedicated short-range communication technology to enable seamless and secure toll transactions. By integrating encryption protocols and authentication mechanisms, ETC systems can significantly reduce the risk of unauthorized access and fraudulent activities.
Another innovative approach for secure toll transactions involves the use of blockchain technology. Blockchain, with its decentralized and immutable ledger system, can ensure the integrity and security of toll transaction records. Through the use of smart contracts, blockchain technology can automate toll transactions while maintaining a high level of security, transparency, and auditability.
Another innovative approach for secure toll transactions involves the use of blockchain technology. Blockchain, with its decentralized and immutable ledger system, can ensure the integrity and security of toll transaction records. Through the use of smart contracts, blockchain technology can automate toll transactions while maintaining a high level of security, transparency, and auditability.
Moreover, the adoption of biometric authentication for toll transactions presents a viable innovative solution. Biometric identifiers such as fingerprint or facial recognition can add an extra layer of security, making it much harder for unauthorized individuals to access toll accounts or commit fraudulent transactions.
Furthermore, the implementation of real-time monitoring and anomaly detection systems can contribute to secure toll transactions. These systems can detect and alert operators of any suspicious activities or potential security breaches, enabling prompt intervention to mitigate risks and safeguard user information.
In conclusion, by embracing innovative solutions such as secure ETC systems, blockchain technology, biometric authentication, and real-time monitoring, toll collection operations can significantly enhance the security and integrity of transactions while providing users with peace of mind regarding the privacy and protection of their financial data.
Enhancing Safety Measures in Toll Collection Operations Ensuring the safety and security of toll collection operations is paramount to protect user privacy, financial information, and the integrity of the toll collection systems. To enhance safety measures, it is imperative to implement robust security protocols at every stage of the toll collection process.
One crucial aspect is the deployment of advanced encryption mechanisms to safeguard user data during transactions and while stored in the system. Additionally, introducing multi-factor authentication for toll collection personnel and implementing stringent access controls can help prevent unauthorized access and tampering with the payment systems [14].
Regular security assessments and audits should be conducted to identify and address potential vulnerabilities, ensuring that the toll collection infrastructure remains resilient against evolving security threats. Moreover, integrating real- time monitoring and intrusion detection systems can provide proactive defense against cyberattacks and system breaches.
Furthermore, employee training and awareness programs must be established to educate staff about security best practices and to cultivate a culture of vigilance against potential security threats. By enhancing safety measures in toll collection operations, organizations can instill trust in users, protect sensitive information, and maintain the integrity and reliability of the toll collection systems [15].
Toll collection systems are integral to transportation infrastructure, and ensuring their security is paramount to safe-guarding user data and preventing potential cyber threats. By understanding the specific vulnerabilities that these systems face, stakeholders can implement effective measures to mitigate risks and enhance security.
Security risks in toll collection systems can stem from various sources, including:
Weak access controls and authentication mechanisms can lead to unauthorized access to sensitive data and the toll collection system itself.
Malware, software bugs, and inadequate system monitoring can create vulnerabilities that can be exploited by malicious actors.
Inadequate data encryption and insufficient protection of user information can result in data breaches, compromising user privacy and confidentiality.
Toll collection systems are increasingly becoming targets for cyberattacks such as ransomware and phishing attempts, posing significant risks to both the system and user data.
Mitigating these security risks requires a multi-faceted approach that encompasses technical, operational, and procedural measures
Implementing robust access controls, encryption protocols, and intrusion detection systems to proactively identify and prevent unauthorized access or data breaches.
Providing comprehensive training to employees on security best practices, including the recognition of social engineering tactics and phishing attempts.
Ensuring compliance with industry standards and regulations to establish a strong foundation for security measures within toll collection systems.
Integrate security considerations into the entire development lifecycle of toll collection systems, including the initial requirements engineering phase.
By adopting these measures, stakeholders can strengthen the security posture of toll collection systems, safeguard user data, and protect against potential security risks.
As technology continues to advance, the future of toll collection security presents both challenges and opportunities. One of the key challenges is the increasing sophistication of cyber threats and attacks targeting toll collection systems. Cybercriminals are continuously developing new methods to exploit vulnerabilities and gain unauthorized access to sensitive user data and payment information. This underscores the critical need for toll authorities and system developers to stay ahead of these evolving threats by implementing advanced security measures and staying abreast of the latest cybersecurity best practices.
Additionally, the emergence of new technologies such as connected and autonomous vehicles introduces unique security challenges for toll collection systems. These vehicles rely on seamless and secure interactions with toll infrastructure, necessitating robust security protocols to ensure the integrity and privacy of data exchanged between vehicles and tolling systems. Furthermore, the proliferation of mobile payment platforms and digital wallets in toll transactions introduces complexities in securing payment data and personal information, demanding innovative security solutions to protect against fraudulent activities and data breaches.
Amid these challenges, there are also opportunities to enhance toll collection security through advancements in technologies such as blockchain, artificial intelligence, and biometric authentication. Blockchain, with its inherent tamper-resistant properties, holds promise in ensuring the integrity of toll transaction records and enhancing the transparency and auditability of tolling operations. Furthermore, the application of artificial intelligence for anomaly detection and behavior analysis can strengthen the ability to identify and respond to potential security threats in real time, bolstering the overall resilience of toll collection systems.
Biometric authentication, through modalities like fingerprint recognition or facial recognition, offers a secure and convenient method for user authentication in toll transactions, reducing the reliance on traditional and often vulnerable payment credentials. Integrating these advanced technologies into toll collection systems presents an opportunity to elevate security measures and provide a seamless and trusted experience for users.
Moreover, the future of toll collection security entails collaboration among stakeholders, including government agencies, technology providers, and cybersecurity experts, to establish industry standards and best practices that address the evolving security landscape. By fostering a collective approach to security, the toll industry can proactively identify and mitigate security risks, promote information sharing on emerging threats, and collectively invest in research and development to fortify the security posture of toll collection systems.
In conclusion, the future of toll collection security demands a proactive and multi-faceted approach to address the evolving threat landscape while leveraging innovative technologies and collaborative efforts to strengthen the resilience and integrity of toll collection systems. Embracing these challenges and opportunities will be pivotal in shaping a secure and trustworthy environment for toll transactions, ensuring the protection of user data and the continuous advancement of toll collection security.
In conclusion, addressing security vulnerabilities in toll collection systems is essential for safeguarding user data, preventing unauthorized access and cyberattacks, and maintaining the integrity and reliability of the system. By implementing robust security measures, regularly evaluating and assessing the system, and integrating legal and regulatory measures, organizations can mitigate risks and ensure the safety and privacy of user data in toll collection systems. Taking a comprehensive approach that considers all components influencing the system and implementing effective security controls will help enhance overall security and privacy. Additionally, ongoing compliance with evolving security policies and the use of proven systems development life cycle methodology are crucial for maintaining control of information system assets and ensuring the ongoing security and integrity of toll collection systems.
1. Chen C, Fan Y, Farn C (2007) Predicting electronic toll collection service adoption: An integration of the technology acceptance model and the theory of planned behavior. Transportation Research Part C: Emerging Technologies 15: 300-311.
2. Tesei A, Lattuca D, Luise M, Pagano P, Ferreira JJ, et al. (2023) A transparent distributed ledger-based certificate revocation scheme for VANETs. Journal of Network and Computer Applications 212: 103569.
3. Bertino E (2016) Data Security and Privacy: Concepts, Approaches, and Research Directions. IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA 400-407.
4. Stephens J, Valverde R (2013) Security of E-Procurement Transactions in Supply Chain Reengineering. Computer and Information Science 6: 1-20.
5. Xie Cheng Shan, Xujia Gu Yue, Wang Li (2007) Information security assurance lifecycle research. The Journal of China Universities of Posts and Telecommunications 14: 77-81.
6. Alshammari B (2017) Enterprise Architecture Security Assessment Framework (EASAF). Journal of Computer Sciences 13: 558-571.
7. Stoneburner G, Goguen A, Feringa A (2002) SP 800- 30. Risk Management Guide for Information Technology Systems. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/ nistspecialpublication800-30.pdf.
8. Toval A, Olmos AP, Piattini M (2002) Legal requirements reuse: a critical success factor for requirements quality and personal data protection. Proceedings of the IEEE Joint International Conference on Requirements Engineering 1-9.
9. Dennis K, Alibayev M, Barbeau SJ, Ligatti J (2020) Cybersecurity Vulnerabilities in Mobile Fare Payment Applications: A Case Study. Transportation Research Record 2674: 616-624.
10. Harvey J, Kumar SA (2020) A Survey of Intelligent Transportation Systems Security: Challenges and Solutions. In 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing,(HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS) IEEE 263-268.
11. Gupta R, Agarwal R, Goyal S (2014) A Review of Cyber Security Techniques for Critical Infrastructure Protection. International Journal of Computer Science & Engineering Technology 5: 331-334.
12. Khattak ZH, Park HJ, Hong S, Boateng RA, Smith BL (2018) Investigating Cybersecurity Issues in Active Traffic Management Systems. arXiv https://arxiv.org/ftp/arxiv/ papers/1804/1804.05901.pdf.
13. Reilly J, Martin S, Payer M, Bayen AM (2015) On Cybersecurity of Freeway Control Systems: Analysis of Coordinated Ramp Metering Attacks. Transportation Research Board 94th Annual Meeting Transportation Research Board https://trid.trb.org/view/1339121.
14. Andersen B (1991) Information Security Issues in Trans- action Systems Applied to an Integrated Road Traffic Environment. IFAC Proceedings 24: 135-140.
15. Chang K, Seely B (2018) The challenging nexus of technology and security in transportation management center operations. Proceedings of the Fifth Cybersecurity Symposium 1-9.
View PDF