Author(s): Shriyash Shete
This paper presents an innovative approach to visualizing cybersecurity coverage within the Zscaler Risk360 product, leveraging the MITRE ATT&CK framework. Emphasizing a user-centered design methodology, the study integrates the complex ATT&CK framework into a practical, interactive interface tailored for cybersecurity professionals. This interface combines qualitative and quantitative metrics, enabling users to assess the security posture of their organization effectively. The design process is informed by insights from semi-structured interviews with Chief Information Security Officers (CISOs) and subject matter experts, ensuring relevance and usability. The paper discusses key design decisions, including the integration of complex framework tree structures, color-coded coverage mappings, and a three-pane view for detailed analysis. Additionally, it explores extended use cases beyond the immediate application, suggesting potential for broader applications in various cybersecurity and compliance contexts. This work aims to enhance decision-making in cybersecurity management and inspire future research and development in cybersecurity and data visualization tools.
Defending an enterprise network against cyberattacks remains an increasingly difficult challenge that requires, among other things, advanced technologies and innovative approaches for thwarting an adversary’s goals. Because new and complex attacks are continuously created, there is a need for a common framework to understand how attackers operate to achieve their objectives. This framework should not only help in understanding the attack but also to understand existing defenses and what mitigations can be put in place to thwart attacks.
This paper explains the interface design process to visualize the Cybersecurity coverage in the context of the Zscaler Risk360 product. It delves deeper into the user-centered design approach that was implemented to achieve the innovation interface solution intended for cybersecurity professionals.
To help address the challenges of defending against modern attacks, MITRE Corporation developed a process for modeling an adversary’s post-compromise behavior at a granular level with a common taxonomy. This model is named the ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework, and it serves as a knowledge base of commonly observed adversarial behaviors to support the efforts of threat intelligence functions, with adversary emulation and defensive gap analysis. ATT&CK was created out of the need to systematically document and catalog adversaries’ behaviors based on millions of data points observed from real-life attacks and breaches. The model describes the Tactics, Techniques, and Procedures (TTPs) of adversarial behavior and breaks them into categories based on the sequence of steps involved in an attack. It is not intended to be exhaustive and is very much a living framework that is continuously updated as new TTPs are discovered [1,2].
The ATT&CK model is an ordered list of observed behaviors from known attacks. These behaviors are known as tactics and techniques. ATT&CK is visually organized into a few different matrices: PRE-ATT&CK, Enterprise, and Mobile. Each of these matrices contains various tactics and techniques relevant to its domain. PRE-ATT&CK is a matrix of tactics and techniques related to what attackers do before they try to exploit a particular target network or system. The Enterprise matrix contains tactics and techniques that apply to Windows, Linux, and/or MacOS systems. The mobile matrix contains tactics and techniques that apply to mobile devices. The scope of this paper is limited to the Enterprise Matrix [1,2].
The MITRE ATT&CK framework Enterprise Matrix is composed of 14 tactics, including the first two PRE-ATT&CK tactics, each with associated techniques. The tactics appear in roughly sequential order, following the general stages of a comprehensive (or worst-case) adversarial attack (See Figure 1):
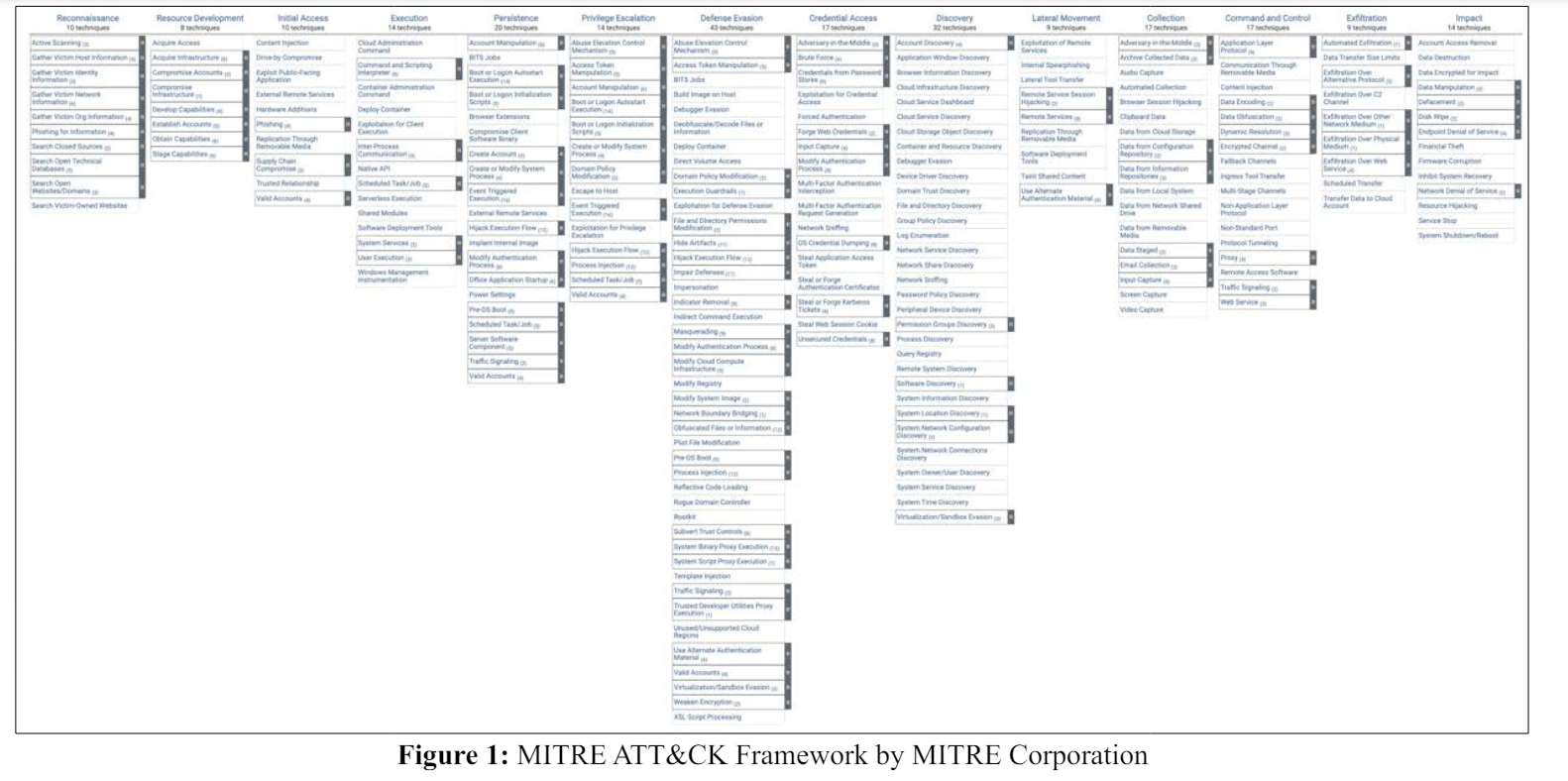
Tactics represent the “why’ of an ATT&CK technique. It is the adversary’s tactical objective for performing an action. Tactics serve as useful contextual categories for individual techniques and cover standard notations for things adversaries do during an operation, such as persist, discover information, move laterally, execute files, and exfiltrate data. A total of 14 tactics have been observed from previous attacks and are defined in the ATT&CK matrix [1,2].
Techniques represent “how’ an adversary achieves a tactical objective by performing an action. Techniques may also represent “what’ an adversary gains by performing an action. For example, an adversary may dump credentials from an operating system to gain access to useful credentials within a network. There may be many ways, or techniques, to achieve tactical objectives, so there are multiple techniques in each tactic category [1,2].
Sub-techniques describe “how’ an adversary achieves a tactical objective in more detail, including the specific tools used. For example, an adversary may use spear phishing as a targeted phishing attack to make the phishing technique look more genuine [1,2].
Sub-techniques describe “how’ an adversary achieves a tactical objective in more detail, including the specific tools used. For example, an adversary may use spear phishing as a targeted phishing attack to make the phishing technique look more genuine [1,2].
Zscaler Risk360 product aims to provide a holistic security measurement and quantification framework to cybersecurity professionals so that they can assess the overall risk posture of the organization and take necessary actions to mitigate risks. The entire framework is based on the individual risk computation for the underlying hundred plus contributing factors. These contributing factors are nothing but the risk findings in an organization’s environment categorized into four stages of a typical cyber breach: 1. External Attack Surface (where the threat actor attempts to discover an organization’s external attack surface exposed to the internet), 2. Compromise (the threat actor attempts to compromise an organization’s corporate asset via threats delivered from the internet) 3. Lateral Propagation (the threat actor attempts to move laterally within the organization’s environment from the compromised asset) and 4. Data Loss (the threat actor steals sensitive data as part of the actions on the objective stage).
These are tailored to CISOs needs to efficiently monitor the security environment of the business and make security enhancement and remediation decisions efficiently. Risk360 assesses thousands of signals from other Zscaler offerings to compute a comprehensive and aggregated risk score. It covers all the underlying contributing factors associated with multiple Zscaler capabilities implemented in the organization’s digital environment [3,4].
We conducted twelve 30-minute semi-structured interviews with CISOs as well as subject matter experts (SMEs) to discuss the significance of MITRE ATT&CK in cybersecurity and identify the ways to showcase it in the context of Risk360.
From the interviews, we found that the goal of ATT&CK is to break down, classify, and document adversarial behaviors from previously observed attacks in a common language that is consistent and clear. This type of cataloging and identification provides a number of benefits to cyber security professionals, such as the following use cases:
Test and verify defenses against common techniques of adversaries.
Create plans and organize operations to avoid certain defensive measures that may be in place within a network.
Assess tools, monitoring, and mitigation capabilities of existing defenses within an organization’s environment.
Identify gaps as a way to prioritize investments for security improvements. Similar security products can also be compared against a common adversarial behavior model to determine coverage.
Identify and rank alerts based on their potential threat level.
Test and verify defenses against com- mon techniques of adversaries.
In this paper, we primarily focus on the ‘Evaluate current defenses’, ‘Finding gaps in coverage’ and ‘Prioritize detections’ aspects that are important for security executives and analysts with titles Chief Information Security Officer(CISO), Chief Security Officer (CSO) and Security Operators in the context of Zscaler Risk360 software.
Overall, we identified the common theme of suggestions: Mapping the risk360 contributing factors with mitigations for various ATT&CK techniques and keeping it as part of the Risk360 interface.
Below are some other key insights we gathered about the MITRE framework:
through interviews, we found out that cyber security professionals are well-versed with analytical findings and want to see quick numeric data to make sense of the information presented. Hence, instead of only showing the coverage in terms of qualitative metrics using visual mappings, we need to combine them with quantitative findings such as showing the percentage of coverage with the help of a donut chart. For example, if total number for of covered techniques is 83 out of the total 196 techniques then we should highlight 43% using a chart.
During interviews, one of the subject matter experts pointed out an official scoring rubric that MITRE corporation recommends to assess the effectiveness of the TTPs. They assess each technique’s effectiveness in terms of three levels-minimal, partial and substantial. Also they categorize each technique into three control types-protect, detect and respond. We decided to leverage these familiar methodologies and include them in the interface design.
Coverage, Configuration: through our study, we found out that the MITRE attack framework can be utilized to understand two critical data points-1. The number of tactics techniques and sub-techniques are covered by the current Zscaler controls in place and 2. Whether those controls are correctly configured or misconfigured.
MITRE Corporation provides a web-based open source tool called ATT&CK Navigator which is highly customizable and can be used for annotating and exploring ATT&CK matrices. It can be used to visualize defensive coverage, red/blue team planning, the frequency of detected techniques, and more. However, the tool requires users to set up the color-coding and mapping manually which is a very difficult task for large enterprises with large security infrastructure. These are often a medley of point solutions, spreadsheets, and manual aggregation of datasets to feed the navigator tool. We used this tool as an inspiration for providing an appropriate level of user control within a single Risk360 software [3,5].
We also took inspiration from the interfaces of Splunk Lantern and Microsoft Sentinel software interfaces which attempt to provide analytical insights through the MITRE ATT&CK framework visualization [6,7].
Based on the insights that we gained from our interviews and data analysis, we designed high-fidelity mockups using Figma. Below are some of the key design decisions made
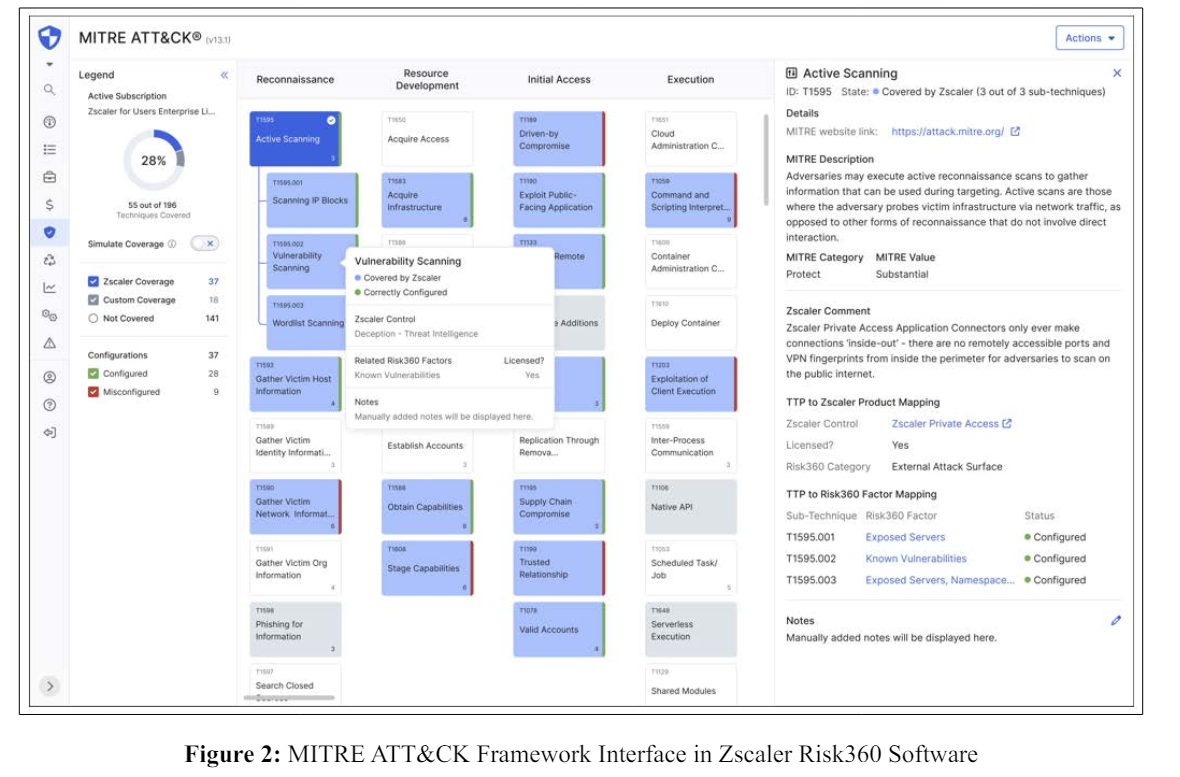
Jakob’s law of UX states that users spend most of their time on other sites. This means that users prefer your site to work the same way as all other sites they already know. Hence, in this case, we know that the security professionals are familiar with the MITRE ATT&CK website and would expect any other relevant interface to work similarly. Therefore, we decided to preserve the familiarity of the MITRE ATT&CK framework by maintaining the structure and hierarchy of the information. We kept the order of the tactics, techniques and sub- techniques consistent with the official document on the MITRE ATT&CK website. Thus, we assumed that these clickable tree structures with expandable and collapsible tiles, similar to the original familiar interface, would be easy to interact with for the CISOs and security administrators.
Another design consideration was to provide a clear visual mapping of the coverage on top of the MITRE ATT&CK framework. With Zscaler coverage tiles represented in its brand color blue, custom covered in gray and not covered in white, we aimed to provide a clear visual indication and separation of different types of coverages quickly to the user. In addition to that, we also represented the configuration status for each technique where a red line meant misconfiguration and a green line depicted a correctly configured technique.
On a broader level, the screen layout was divided into three sections-the leftmost being the legend panel for a quick overview of the security coverage, the middle one dedicated to the interactive framework itself and the rightmost panel to cover the details of each technique.
Because the framework itself has 196 techniques and 411 subtechniques in total, and each of them has a long list of associated metrics to be shown inside the details panel, there was a need to quickly display the summary of those details, without the CISOs having to click several times to delve deeper. We used the tooltip design pattern filled with rich summary information that pops up when a user hovers over a technique.
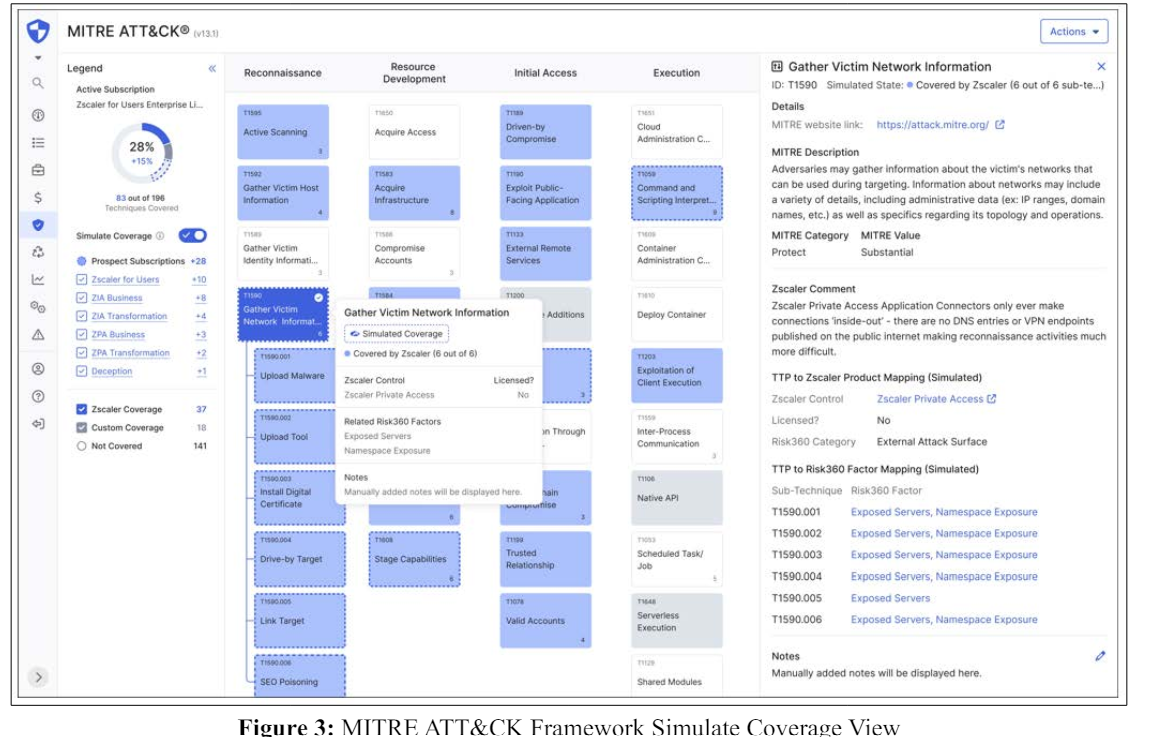
As Zscaler coverage shown in blue depicts the coverage based on customers’ existing subscriptions, it is impera- tive to showcase the simulated coverage that a customer can potentially add with other remaining subscriptions. Hence to make it intuitive and aesthetically appealing, we created a separate simulated coverage view that the CISOs and executives could toggle on and interact with to understand the value of purchasing other Zscaler licences as shown in the figure below. Thus it can accelerate the decisionmaking process for customers and bring upsell opportunities for Zscaler.
As mentioned above, the coverage and visualization fulfil half of the objectives, and the remaining half is to convey whether the covered techniques were correctly configured or not. This was achieved by displaying the clear mapping between each sub-technique and the associated Risk360 contributing factors.
We envision that this innovative, security framework-based coverage visualization, and three panel-based approaches, can be used to fulfil other use cases such as representing the coverage based on the NIST CSF or NIST 800 frameworks [8].
Typically governance risk and compliance teams, use multiple tools to audit, evaluate and understand different regulatory compliance statuses such as ISO, SOC2, GDPR, HIPAA, to name a few. This particular visualization may inspire further innovative workflows, where the additional dimension of compliance can be represented visually to provide a full picture of cyber security risk posture, to the concerned teams. Sales team.
We anticipate that the security coverage view along with the simulated coverage view would be beneficial to secondary personas such as salespersons who intend to use this risk360 product and this MITRE Attack framework to explain the capabilities and upsell more Zscaler services.
Besides the color-coded security coverages, this framework-based visualization can be leveraged to map different cyberattacks by highlighting various tactics, techniques, and procedures involved. It can be used to study different types and stages of cyberattacks to shape future risk predictions.
This paper explains how a user-centered design approach can be valuable in representing the complex information of security coverage based on the popular framework of MITRE ATT&CK. Using the color-coded layers approach on top of the original framework enhances usability and caters to multiple personas. With this innovative design solution, we can help cybersecurity professionals make sense of the complex data related to the security posture of the organization. With a thorough usability evaluation of this interface in the future, we hope that this novel approach will spark future conversations, and research directions in the cyber security and data visualization spaces.
