Author(s): Dinesh Reddy Chittibala
This paper presents a comprehensive examination of the integration of Web Application Firewalls (WAF) within DevOps practices, underscoring the pivotal role of WAFs in fortifying security, enabling automation, and ensuring continuous protection. As DevOps methodologies advocate for rapid development and deployment cycles, robust security mechanisms that can keep pace with these accelerated processes are paramount. This study explores how integrating WAFs into the DevOps pipeline enhances the security posture of applications without impeding the agility and efficiency that DevOps promotes. It delves into the complexities of this integration, discusses strategies for seamless implementation, and addresses the challenges encountered in aligning WAF capabilities with the continuous and automated nature of DevOps workflows.
In the world of software development, DevOps stands out as a powerful approach that brings together the creation of software (development) and the management of it (operations). This combination goes beyond just merging tasks; it represents a significant shift in workplace culture, speeding up how quickly software can be released and encouraging creative solutions. DevOps is known for its focus on smooth teamwork across different departments, like development, quality checks, and operations, which allows for a quick and continuous flow of software production and release. However, with this fast pace comes the need for strong security measures. It's crucial to integrate security deeply within the DevOps process. This means making sure that from start to finish, as software is being developed and managed, keeping it safe from cyber threats is a key part of the workflow.
Enter the realm of Web Application Firewalls (WAF), the sentinels standing guard at the precipice of web applications. WAFs serve as a formidable barrier, shielding applications from various threats like SQL injection, cross-site scripting, and forgery, among others. In the dynamic ecosystem of DevOps, where changes are as frequent as they are critical, the integration of WAFs pivots from being an option to a necessity. WAFs offer a robust defense mechanism along with bringing the versatility needed to adapt to the ever-changing threat landscape, all while aligning with the rapid deployment cycles characteristic of DevOps.
The crux of this paper is to embark on a scholarly exploration into the integration of WAF within DevOps practices, unraveling its multifaceted implications. The discourse aims to illuminate how WAF integration transcends conventional security measures, harmonizing with the automated pipelines of DevOps to fortify applications against threats continuously. It's an inquiry into the synthesis of security and agility, probing how WAFs can be seamlessly woven into the DevOps fabric, thereby enhancing the security posture without compromising the fluidity and pace of development and deployment processes.
DevOps is a modern approach in software development that combines the creation (development) and management (operations) of software into a cohesive process. The key principles of DevOps revolve around collaboration, automation, continuous integration, continuous delivery, and quick feedback loops. This integration aims to shorten the development lifecycle, fostering a culture of high efficiency and flexibility. It allows teams to release software faster and more frequently, responding swiftly to market demands and customer feedback.
While DevOps accelerates software development and deployment, it also presents unique cybersecurity challenges. The rapid pace and constant changes make it harder to enforce traditional security measures. Security needs to be as dynamic and adaptable as the DevOps process itself. This means embedding security practices directly into the development pipeline. However, ensuring that these practices do not slow down operations is a delicate balance. The need for security solutions that can keep up with continuous development, integration, and deployment is paramount. They must be capable of identifying and mitigating threats in real time, ensuring that every release is fast and secure.
A Web Application Firewall (WAF) is the frontline defense mechanism specifically designed to protect web applications from a wide range of security threats and vulnerabilities. Unlike traditional firewalls, WAF operates at the application layer and scrutinizes every HTTP request coming to your web application. It effectively shields applications from prevalent dangers such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), among others. Furthermore, WAFs are not only reactive but can also proactively identify and mitigate potential threats based on predefined or dynamically learned security rules, offering robust protection and ensuring the integrity, confidentiality, and availability of web applications.
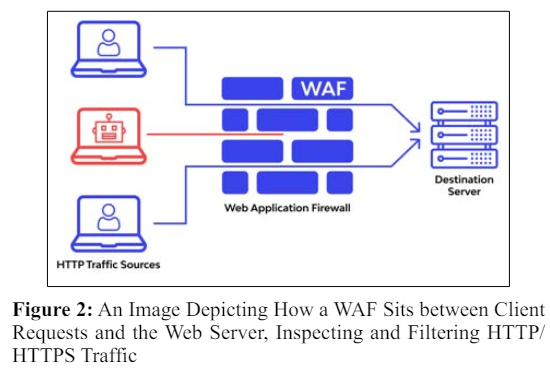
WAFs operate by intercepting and analyzing every HTTP/HTTPS request before they reach the web application. Here’s how WAFs typically function:
WAFs analyze incoming traffic to identify malicious requests. This involves inspecting GET/POST requests, URL parameters, cookie data, and HTTP headers.
WAFs use a set of predefined or custom rules to identify and filter out malicious traffic. These rules are based on patterns known to be indicative of attacks (such as those seen in SQL injection or XSS).
Some advanced WAFs use anomaly detection to identify threats. They establish a baseline of normal behavior and then flag or block requests that deviate significantly from this norm.
Once a threat is identified, the WAF can block the malicious request, ensuring it doesn't reach the web application. Simultaneously, it can alert administrators about the detected threat for further investigation.
In the CI/CD pipeline, WAF plays a critical role in automated security testing. It acts as a gatekeeper, inspecting and filtering HTTP/HTTPS traffic to and from web applications. By integrating WAF into CI/CD, organizations can automatically test their web applications against common threats like SQL injection, cross-site scripting, and others, in real-time.
The integration of WAF within CI/CD enables real-time threat analysis, which is crucial for identifying and mitigating vulnerabilities early in the development process. This continuous monitoring ensures that any changes in the code or new deployments do not introduce security vulnerabilities
WAF settings and rules need to be treated as part of the application code. This involves storing WAF configurations in version control systems alongside the application code. This practice ensures consistency across environments and facilitates rollback in case of erroneous rule updates that might block legitimate traffic or allow vulnerabilities.
Changes to WAF rules should go through the same review process as application code changes. This includes peer reviews, automated testing, and logging of changes for audit trails.
Integrating WAF configuration within IaC tools like Terraform, Ansible, or AWS CloudFormation enables automated provisioning and management of security controls. This approach aligns with the DevOps philosophy of infrastructure automation and ensures that security controls are consistently applied across all environments.
IaC allows for dynamic configuration of WAF settings based on the deployment environment. For instance, stricter rules can be applied in production than in development, and this can be automatically managed through IaC scripts.
A multinational financial services provider adopted WAF in their DevOps to secure online transactions and comply with financial regulations.
The main challenge the company was facing was web attacks, SQL injection, and cross-site scripting, which threatened customer data, service availability, and transaction speed.
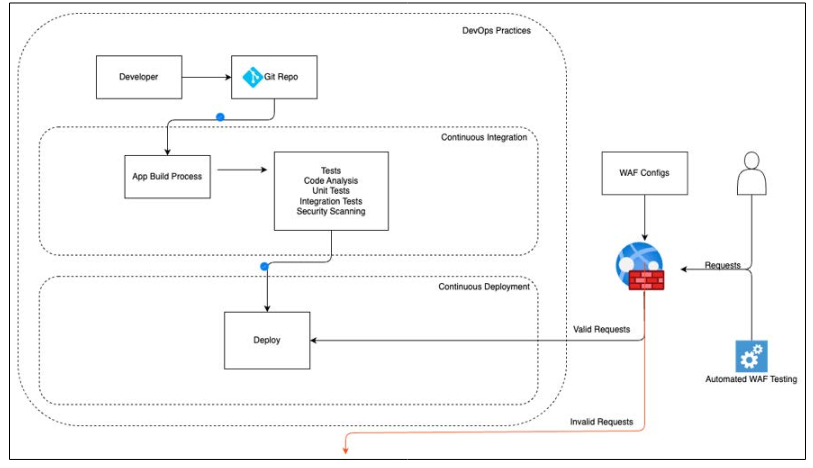
Figure 3: An Illustration of DevOps Integrated with WAF. Automated WAF Testing is Done Against WAF and Application and Rules are Updated as Needed
A Cloud WAF is introduced for all the web applications in CI/CD pipeline. WAF rules and policies were managed via code, enabling rapid updates and compliance checks. The company also pushed Automated WAF testing, which helped them to detect new rules to be added to WAF. Figure 3 provides an architectural solution on how DevOps and WAF were integrated.
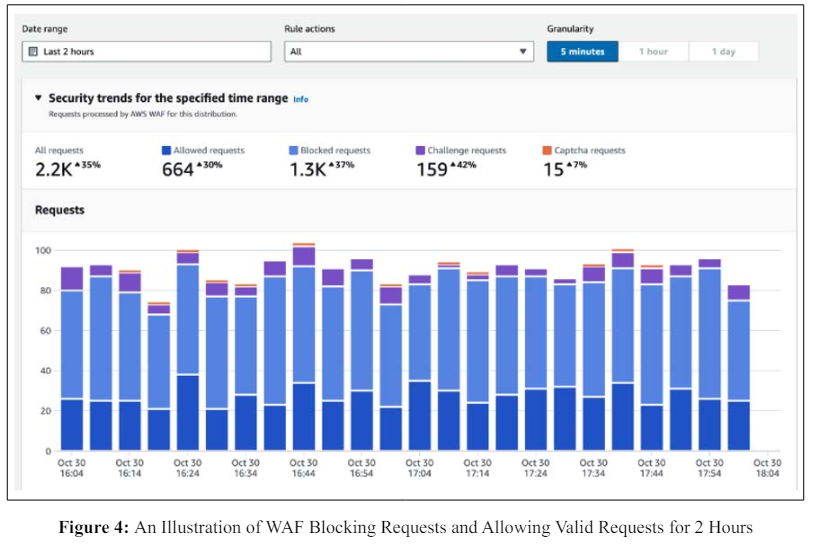
In the integration of Web Application Firewalls (WAF) into DevOps practices, several challenges arise, primarily balancing security with the need for speed in development. The rapid and dynamic nature of DevOps, characterized by frequent code updates and environment changes, complicates effective WAF configuration. Additionally, the complexity of WAF management, ensuring comprehensive coverage without triggering false positives, and adhering to compliance and reporting requirements add layers of difficulty. Moreover, a skills and knowledge gap often exists within DevOps teams regarding the nuances of WAF technology
To address these challenges, it is crucial to implement automated security testing and to integrate continuous security practices within the DevOps pipeline. Solutions like Policy as Code (PaC) can enable dynamic adjustments to WAF configurations, adapting to the ever-changing DevOps environment. Utilizing DevOps tools such as Ansible, Chef, or Puppet for automating WAF configurations can alleviate the complexity of management. Regular updates of WAF rules based on the latest threat intelligence, coupled with continuous monitoring and security assessments, are essential to maintain effective coverage. Automating compliance checks and leveraging WAF features for detailed logging and reporting can help in meeting regulatory standards. Bridging the skills gap requires regular training and fostering collaboration between security experts and DevOps teams.
In conclusion, while integrating WAF into DevOps presents distinct challenges, leveraging solutions like automation, continuous monitoring, and policy as code, along with fostering an environment of continuous learning and collaboration, organizations can overcome these hurdles. This ensures a robust, secure, and efficient DevOps pipeline, aligning with the overarching goals of both security and development agility
It is essential to look ahead at emerging trends and future directions that will shape DevOps and WAF integration. The landscape of cybersecurity and DevOps is continually evolving, and staying ahead of these trends is critical for maintaining robust security and operational efficiency.
The integration of Web Application Firewalls (WAF) into DevOps is poised to be revolutionized by Artificial Intelligence (AI) and Machine Learning (ML). These technologies promise to bring about WAFs that are not only reactive but also predictive. We can anticipate WAFs that automatically adjust to emerging threats, learn from past attack patterns, and predict vulnerabilities before they are exploited. This evolution will facilitate a more proactive approach to security and more efficient anomaly detection, significantly enhancing the capability of WAFs to protect in a dynamic DevOps environment.
As the shift towards cloud-native architectures and serverless computing continues, the need for adaptable WAF solutions becomes more pronounced. Future WAFs are likely to be more modular and scalable, seamlessly integrating with cloud services. These solutions will need to address the transient nature of serverless functions, offering dynamic protection that matches the scalability and flexibility inherent in cloud-native technologies. This adaptation will ensure that WAFs remain effective in protecting applications that leverage the latest cloud computing paradigms.
The emerging trend of DevSecOps, where security is an integral part of the entire software development lifecycle, is gaining significant momentum. In this context, security considerations, including WAF configurations and policies, are expected to be an inherent part of the development process. The implication of this shift is profound: security will be embedded in the product from its inception, rather than being appended as an afterthought. This holistic approach will ensure a more secure development workflow, with WAFs playing a key role in this integrated security strategy.
In an era where data protection and cybersecurity regulations are becoming increasingly stringent, automated compliance will be a key feature of future WAF solutions. These solutions are likely to include capabilities for ensuring adherence to various regulatory requirements, possibly through automated reporting, real-time compliance checks, and integration with governance frameworks. Such features will not only ensure compliance but also streamline the governance process, making it more efficient and less prone to human error.
The ongoing advancement in technologies such as IoT, 5G, and edge computing will necessitate the evolution of WAF solutions to protect a broader range of devices and networks. As these technologies become more prevalent, WAFs will need to adapt to safeguard not just traditional web applications but also the diverse array of devices and networks associated with these emerging technologies. This evolution will be crucial in maintaining the security integrity of systems operating at the network's edge and beyond.
In the quest to harmonize rapid development with robust security, the integration of Web Application Firewalls (WAF) within DevOps practices emerges as a crucial strategy. This paper has embarked on a comprehensive exploration of how WAFs can be seamlessly woven into the DevOps fabric, enhancing the security posture without compromising the agility and efficiency inherent in DevOps methodologies. From the initial understanding of the necessity for enhanced security in fast-paced development environments to the intricate details of WAF integration strategies, this study has highlighted the multifaceted role of WAFs in ensuring continuous protection in an ever-evolving digital landscape.
The case studies presented provide real-world insights into the transformative impact of WAF integration, demonstrating significant improvements in both security and operational efficiency. Furthermore, the discussion on the challenges and corresponding solutions offers a pragmatic guide for organizations striving to balance the dual objectives of rapid deployment and stringent security. As we look toward future trends, the anticipated advancements in AI and ML, cloud-native solutions, and the growing emphasis on DevSecOps paint an optimistic picture of more intelligent, adaptable, and integrated WAF solutions.
In conclusion, as the field of DevOps continues to evolve, the role of WAFs will become increasingly pivotal. The continuous refinement and integration of WAFs within DevOps are not just a response to the escalating sophistication of cyber threats but also a proactive approach to building more secure, resilient, andefficient digital ecosystems. This paper underscores the importance of a forward-thinking mindset, where the integration of advanced security measures like WAFs is viewed as an integral and ongoing aspect of the DevOps process, paving the way for a more secure and agile future in software development and deployment [1-6].
1.Liang J, Zhao W, Ye W (2017) Anomaly-based web attack detection: A deep learning approach. Proceedings of the 2017 VI International Conference on Network, Communication and Computing; Kunming, China 80-85.
2.Moradi VA, Mehralian S, Teshnehlab M, Sedighian KS (2019) Auto-Encoder LSTM Methods for Anomaly-Based Web Application Firewall. Int J Inf Commun Technol Res 11: 49-56.
3.Pantoulas E (2022) Description, Analysis and Implementation of a Web Application Firewall (WAF). Master’s Thesis: School of Information Technology and Communications; Piraeus, Greece.
4.Rajesh S, Clement M, Sooraj SB, Shifan SH, Johnson J (2021) Real-Time DDoS Attack Detection Based on Machine Learning Algorithms. Proceedings of the Yukthi 2021-The International Conference on Emerging Trends in EngineeringGEC Kozhikode; Kerala, India https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3974241.
5.Osanaiye O, Choo KKR, Dlodlo M (2016) Distributed denial of service (DDoS) resilience in cloud: Review and conceptual cloud DDoS mitigation framework. J Netw Comput Appl 67: 147-165.
6.Dariusz P, Zachara M (2011) Learning Web Application Firewall - Benefits and Caveats. Availability, Reliability and Security for Business, Enterprise and Health Information Systems 295-308.
View PDF