Author(s): Pavan Nutalapati
T he rapid adoption of cloud technologies and the increasing sophistication of cyber threats have necessitated the evolution of security models in fintech applications. Traditional perimeter-based security models are insufficient for protecting sensitive financial data in dynamic and distributed cloud environments. This paper explores the implementation of Zero Trust Architecture (ZTA) in cloud-based fintech applications. Zero Trust is a security model that assumes that threats could exist both inside and outside a network, enforcing strict verification for every entity attempting to access resources. This study reviews the principles of Zero Trust, its benefits, and challenges in the context of fintech, and presents a comprehensive framework for integrating ZTA into cloud-based fintech infrastructures. Additionally, this paper introduces sample code snippets to demonstrate the practical application of ZTA principles in fintech environments. The paper concludes with a discussion on future trends and the need for continuous adaptation of security strategies in the evolving digital landscape.
The fintech industry has experienced explosive growth, driven by innovations in digital payment systems, cryptocurrencies, and financial services platforms. The global fintech market size was valued at over $110 billion in 2019 and is projected to grow at a compound annual growth rate (CAGR) of 23.58% from 2021 to 2028. This growth has coincided with a rise in cyber threats, including data breaches, phishing attacks, and sophisticated malware. Cybersecurity incidents have increased in frequency and severity, with notable breaches affecting companies such as Equifax, Capital One, and PayPal, exposing millions of users' financial data and eroding consumer trust.
Traditional security approaches, which focus on perimeter defenses, are increasingly ineffective in the cloud environment, where data and applications are distributed across multiple locations and accessed from various devices. The traditional "castle-and-moat" approach to security, where the perimeter is heavily fortified while internal networks are trusted, is no longer viable in the context of modern, distributed architectures. The cloud environment inherently lacks a distinct perimeter, making it vulnerable to a range of attacks, from insider threats to external breaches.
Zero Trust Architecture (ZTA) offers a paradigm shift in cybersecurity by advocating for a "never trust, always verify" approach. This model does not automatically trust any entity, whether inside or outside the network perimeter. Instead, it requires rigorous verification for every access request, ensuring that only authenticated and authorized users can access sensitive resources. The concept of Zero Trust has gained significant traction, with 61% of organizations planning to implement or expand Zero Trust capabilities in the next 18 months, according to a 2021 survey by Gartner.
The primary objective of this paper is to provide a detailed examination of Zero Trust Architecture and its application within the fintech sector, specifically focusing on cloud-based environments. The scope includes an exploration of the fundamental principles of ZTA, the identification of unique security challenges in cloud-based fintech applications, and the development of a comprehensive framework for the implementation of ZTA. Furthermore, this paper aims to highlight the benefits and challenges associated with Zero Trust, offering actionable insights and recommendations for fintech organizations seeking to enhance their security posture.
This paper also seeks to bridge the gap between theoretical concepts and practical implementation by providing code examples and detailed technical strategies for deploying ZTA in cloud environments. Additionally, it aims to offer insights into regulatory compliance and how ZTA can be aligned with industry standards, such as GDPR, PCI-DSS, and ISO 27001.
This paper is structured as follows:
The financial technology (fintech) sector has undergone significant transformation over the past two decades, driven by rapid technological advancements and the increasing demand for digital financial services. As fintech applications have evolved, so too have the cybersecurity threats that target them. The nature of cyber threats has shifted from opportunistic attacks to more sophisticated and targeted assaults, often orchestrated by well- funded cybercriminal organizations or nation-state actors.
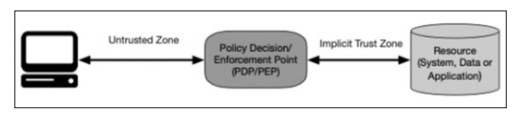
Initially, cybersecurity in fintech focused on perimeter defenses, such as firewalls and intrusion detection systems (IDS). These measures were designed to create a barrier between trusted internal networks and untrusted external networks. The early 2000s saw the widespread adoption of these technologies, with the primary goal of keeping unauthorized users out of the network. However, these early measures were largely reactive, relying on known threat signatures and patterns to detect and block malicious activity.
While effective against known threats, these perimeter-based defenses were vulnerable to zero-day exploits and advanced persistent threats (APTs). Attackers increasingly exploited human weaknesses through phishing and social engineering to gain access to internal networks. By 2008, studies such as the Verizon Data Breach Investigations Report (DBIR) highlighted that more than 70% of data breaches involved external agents, often bypassing traditional security mechanisms.
In response to the increasing complexity of cyber threats, fintech organizations began adopting multi-layered security approaches. This included the implementation of encryption, access controls, and endpoint security solutions. Encryption technologies, such as SSL/TLS for data in transit and AES for data at rest, became standard practices. Identity management systems evolved to include multi-factor authentication (MFA) and role-based access control (RBAC), reducing the risk of unauthorized access.
Endpoint security solutions, such as antivirus software and endpoint detection and response (EDR) systems, were deployed to protect devices connecting to corporate networks. However, the proliferation of mobile devices, the rise of bring-your-own-device (BYOD) policies, and the adoption of cloud services introduced new attack vectors. These developments exposed the limitations of traditional perimeter-based security models, particularly in the context of remote work and global operations.
Despite these advancements, the perimeter-based model still left significant gaps, particularly in the context of cloud environments where data and applications are distributed across multiple platforms and accessed from various locations. The increasing reliance on cloud services for storing and processing financial data necessitated a shift in security paradigms, as attackers could exploit vulnerabilities in cloud interfaces, misconfigured security settings, and inadequate API protections.
The limitations of traditional security models paved the way for the adoption of Zero Trust Architecture. By shifting the focus from perimeter defenses to continuous verification of every access request, ZTA addresses the inherent vulnerabilities of modern IT infrastructures. Zero Trust was first articulated by Forrester Research in 2010, with the core principle that organizations should not trust any entity—whether inside or outside the network— without verifying its identity and security posture.
The adoption of ZTA was initially driven by organizations in highly regulated industries, such as finance and healthcare, where the protection of sensitive data is critical. However, the model has since gained broader acceptance across various sectors, particularly as cloud computing, mobile workforces, and remote access have become ubiquitous. According to a 2020 survey by Cybersecurity Insiders, 72% of organizations had either adopted or planned to adopt Zero Trust principles in their cybersecurity strategies.
The concept of Zero Trust challenges the assumption that everything within an organization's network can be trusted. Instead, ZTA assumes that threats could be internal or external and thus requires continuous verification and validation of each access request. This approach significantly reduces the attack surface by eliminating implicit trust and enforcing strict access controls at every layer of the IT environment.
Zero Trust is built on several core principles:
These principles align with industry frameworks such as the National Institute of Standards and Technology (NIST) Zero Trust Architecture framework, which provides guidelines for implementing ZTA in various environments [1].
The implementation of ZTA involves several critical components:
Cloud computing offers numerous benefits, including scalability, flexibility, and cost efficiency. However, it also introduces unique security challenges, such as data breaches, insecure interfaces, and account hijacking. The shared responsibility model, where cloud service providers and customers share security duties, can sometimes lead to gaps in security coverage if not properly managed.
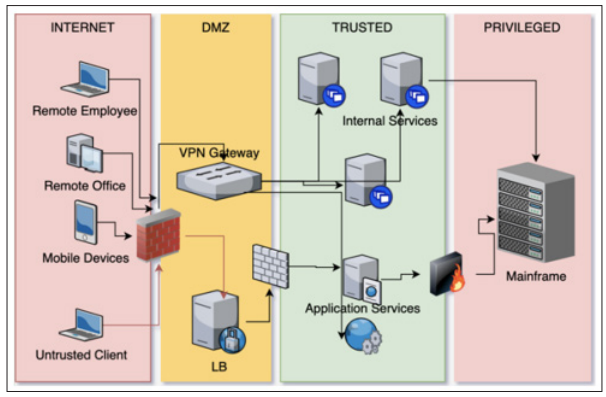
One of the most significant security challenges in cloud environments is the risk of data breaches. The centralized storage of data in cloud environments can make them attractive targets for cybercriminals. According to the 2016 Cloud Security Spotlight Report, 53% of organizations cited data breaches as their top security concern when adopting cloud services. Ensuring data is encrypted both at rest and in transit is crucial for mitigating this risk. Additionally, organizations must implement strong access controls and regularly audit their cloud environments to detect and remediate potential vulnerabilities.
Cloud services often rely on application programming interfaces (APIs) for interaction and integration with other services. Insecure APIs can be exploited by attackers to gain unauthorized access to cloud resources. The OWASP API Security Top 10 highlights common API vulnerabilities, such as broken authentication and excessive data exposure, which can lead to significant security incidents. Implementing robust API security measures, including authentication, access controls, and input validation, is essential to protect against these threats.
Account hijacking occurs when attackers gain unauthorized access to user accounts, often through phishing or brute-force attacks. Multi-factor authentication (MFA) and strong password policies are critical for preventing account hijacking. According to a report by the Ponemon Institute, 54% of organizations that experienced account hijacking attributed the incident to the lack of MFA. In addition to MFA, organizations should implement anomaly detection systems to identify and respond to suspicious login attempts in real-time.
The shared responsibility model in cloud security requires both cloud service providers and customers to share security responsibilities. Cloud providers are typically responsible for the security of the infrastructure, while customers are responsible for securing their data and applications. However, misconfigurations, such as unsecured storage buckets or overly permissive access controls, can expose organizations to significant risks. Clear communication and collaboration between providers and customers are essential for ensuring comprehensive security coverage.
In a Zero Trust model, identity is the new perimeter. Strong IAM practices are essential, including multi-factor authentication (MFA), single sign-on (SSO), and continuous monitoring of user behavior to detect anomalies. Fintech applications must enforce stringent access controls to ensure that only authorized individuals can access sensitive data.
MFA requires users to provide multiple forms of verification before gaining access to resources. This typically includes something the user knows (password), something the user has (security token), and something the user is (biometric verification). Implementing MFA can significantly reduce the risk of unauthorized access. Research by Google has shown that MFA can block up to 99.9% of automated attacks.
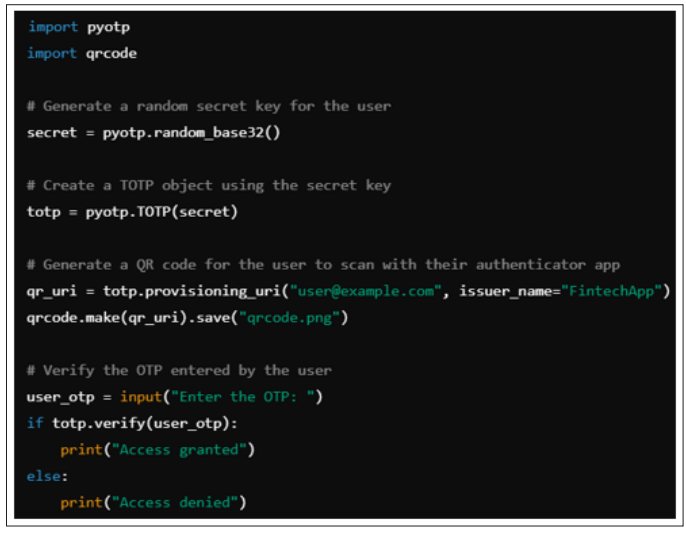
This code snippet demonstrates how to implement MFA using Time-based One-Time Passwords (TOTP) in a Python-based fintech application. The use of TOTP provides an additional layer of security, making it more difficult for attackers to compromise user accounts.
SSO allows users to authenticate once and gain access to multiple applications and services without needing to log in again. This simplifies the user experience and reduces the number of passwords users need to manage, while still ensuring robust security. SSO also enhances security by reducing the attack surface associated with multiple login credentials, which can be a common target for phishing attacks.
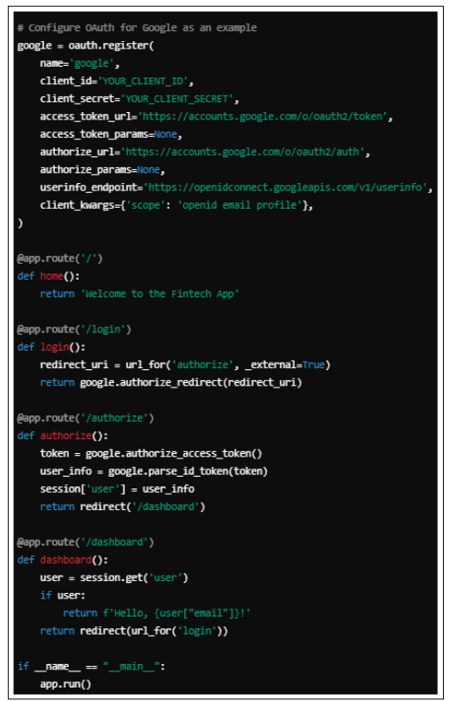
This example demonstrates how to implement SSO using OAuth2 with Google as an identity provider. OAuth2 is widely adopted in the fintech industry due to its robust security features and ease of integration with cloud services.
Continuous monitoring involves tracking user activities and behaviors in real-time to detect and respond to anomalies. Advanced analytics and machine learning can help identify suspicious behavior patterns, such as unusual login times or locations, and trigger alerts or automated responses. According to a 2015 Ponemon Institute study, organizations that deployed continuous monitoring and analytics reduced the cost of data breaches by an average of $1.5 million.
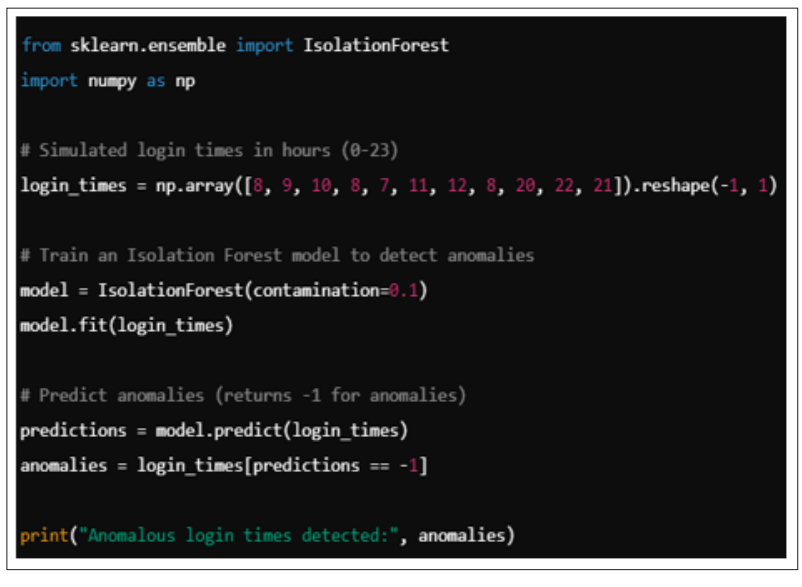
This code snippet uses an Isolation Forest algorithm to detect anomalies in user login times. By identifying deviations from normal behavior, organizations can quickly respond to potential security incidents, such as account takeovers or insider threats.
Devices accessing cloud-based fintech applications must be authenticated and their security posture continuously assessed. This includes checking for malware, ensuring up-to-date security patches, and verifying device configurations. According to Gartner, 70% of breaches originate on endpoint devices, highlighting the importance of robust device security measures.
Device authentication ensures that only trusted devices can access sensitive resources. This can involve using device certificates, hardware-based authentication tokens, or mobile device management (MDM) solutions to verify device identity. By enforcing device authentication, organizations can prevent unauthorized devices from connecting to the network, reducing the risk of compromise.
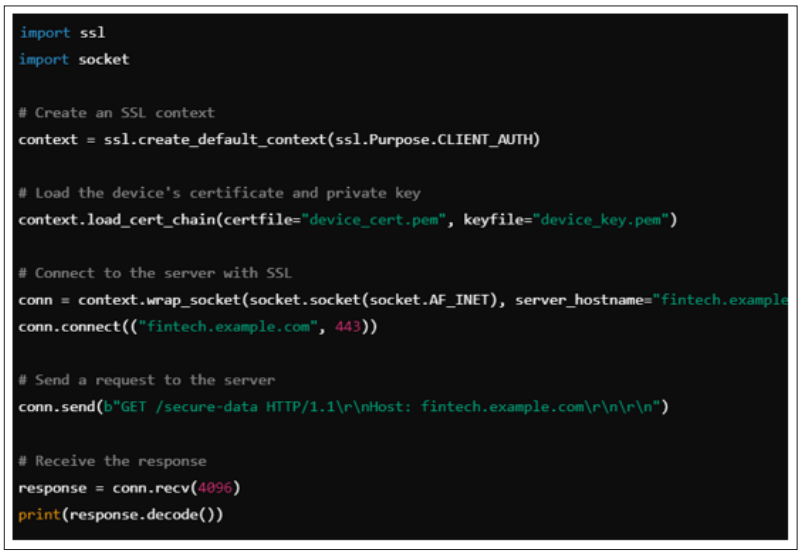
This code demonstrates how to implement device authentication using SSL certificates. Device certificates provide a secure method for verifying the identity of devices connecting to a network, ensuring that only authorized devices can access sensitive resources.
Endpoint protection solutions, such as antivirus software and endpoint detection and response (EDR) systems, are crucial for detecting and mitigating threats at the device level. Ensuring that devices are protected against malware and other threats is essential for maintaining a secure environment. Advanced EDR systems can provide real-time monitoring, threat hunting, and automated response capabilities, enabling organizations to quickly detect and neutralize threats before they cause significant damage.
Regularly assessing the security posture of devices involves checking for compliance with security policies, ensuring that security patches are up-to-date, and verifying that devices are configured securely. This helps to identify and remediate vulnerabilities before they can be exploited by attackers. Organizations can use tools such as Microsoft's Configuration Manager or VMware's Workspace ONE to automate security posture assessments and enforce compliance across all devices.
ZTA emphasizes the importance of network segmentation to limit the lateral movement of attackers. In cloud environments, micro- segmentation can further enhance security by isolating workloads and applying granular access policies. Micro-segmentation is particularly effective in preventing attackers from moving laterally within the network, even if they manage to breach the perimeter.
Traditional network segmentation involves dividing a network into smaller segments, each with its own security controls. This can help to contain the impact of a security breach by preventing attackers from moving freely within the network. For example, separating production environments from development and testing environments can reduce the risk of data leakage and unauthorized access.
Micro-segmentation takes network segmentation to a more granular level, applying security policies at the level of individual workloads or applications. This can involve using software-defined networking (SDN) technologies to create isolated virtual networks within the cloud environment. For instance, VMware NSX and Cisco ACI offer micro-segmentation capabilities that allow organizations to define security policies for specific workloads, ensuring that only authorized traffic can flow between them.
Implementing granular access controls involves defining and enforcing security policies that specify which users and devices can access which resources. This can help to ensure that only authorized entities can access sensitive data and applications, reducing the risk of unauthorized access. Access control models such as Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) provide the flexibility needed to enforce these policies effectively in complex cloud environments.
Data should be encrypted both at rest and in transit. In addition to encryption, ZTA recommends implementing robust data classification and labeling to ensure sensitive information is appropriately protected and handled according to its classification. Data breaches can have severe financial and reputational consequences, making robust data security measures a top priority for fintech organizations.
Encrypting data at rest involves protecting stored data using encryption algorithms. This ensures that even if attackers gain access to the storage medium, they cannot read the data without the encryption keys. Common encryption standards include AES-256, which is widely used for encrypting sensitive financial data. Cloud service providers such as AWS, Azure, and Google Cloud offer built-in encryption services that allow organizations to encrypt data at rest with minimal overhead.
Encrypting data in transit involves protecting data as it moves between different components of the cloud environment, such as between clients and servers or between different cloud services. This helps to prevent attackers from intercepting and reading data as it is transmitted over the network. Transport Layer Security (TLS) is the most commonly used protocol for encrypting data in transit, providing confidentiality and integrity for data exchanged between systems.
Data classification and labeling involve categorizing data based on its sensitivity and applying appropriate security controls to each category. For example, highly sensitive financial data may require stronger encryption and more stringent access controls than less sensitive data. Organizations can use data classification tools such as Microsoft's Azure Information Protection or Symantec's Data Loss Prevention (DLP) to automate the process of classifying and protecting sensitive information.
Continuous monitoring is crucial in a Zero Trust environment. This includes monitoring network traffic, user behavior, and system configurations. Automated responses to detected threats can help mitigate potential breaches swiftly. Continuous monitoring enables organizations to detect and respond to threats in real-time, reducing the dwell time of attackers and minimizing the potential impact of a breach.
Monitoring network traffic involves analyzing data packets as they move through the network to detect anomalies or signs of malicious activity. This can include using intrusion detection systems (IDS) and intrusion prevention systems (IPS) to identify and respond to threats in real-time. Network traffic analysis tools such as SolarWinds, Wireshark, and Zeek (formerly Bro) are commonly used to monitor and analyze network traffic for signs of malicious activity.
User behavior analytics (UBA) involves analyzing user activities and behavior patterns to detect anomalies that may indicate a security threat. For example, if a user typically logs in from a specific location and suddenly logs in from a different country, this could trigger an alert. UBA tools such as Splunk UBA and Exabeam use machine learning algorithms to identify deviations from normal behavior, allowing security teams to investigate and respond to potential threats.
Automated threat response involves using technologies such as security orchestration, automation, and response (SOAR) to automatically respond to detected threats. This can include actions such as blocking access, isolating compromised systems, or initiating incident response procedures. SOAR platforms such as Palo Alto Networks' Cortex XSOAR and IBM's Resilient provide the automation capabilities needed to respond to threats quickly and efficiently, reducing the time to containment and minimizing the impact of security incidents.
The implementation of Zero Trust Architecture in cloud-based fintech applications can be challenging due to factors such as legacy systems, complex IT environments, and resource constraints. Furthermore, the shift to ZTA requires a cultural change within the organization, emphasizing security at every level.
Many fintech organizations rely on legacy systems that were not designed with modern security principles in mind. Integrating these systems into a Zero Trust Architecture can be challenging and may require significant investment in time and resources. Legacy systems often lack the flexibility needed to support modern security controls, such as multi-factor authentication and micro- segmentation. Additionally, these systems may not be compatible with newer technologies, requiring organizations to invest in costly upgrades or replacements.
Fintech organizations often operate complex IT environments that include a mix of on-premises systems, cloud services, and third-party applications. Ensuring consistent security across these diverse environments can be difficult, particularly when different systems have different security requirements and capabilities. The complexity of managing security across multiple environments increases the risk of misconfigurations, which can lead to security gaps and vulnerabilities. Organizations must adopt a comprehensive security strategy that includes consistent policies, centralized management, and regular audits to ensure that all systems are properly secured.
Implementing Zero Trust Architecture can require significant investment in new technologies, processes, and training. Fintech organizations may face resource constraints that limit their ability to implement ZTA fully. Prioritizing high-risk areas and leveraging existing resources can help to overcome these challenges. Organizations should conduct a thorough risk assessment to identify the most critical assets and focus their resources on securing these areas first. Additionally, adopting a phased approach to ZTA implementation can help organizations manage costs and resources more effectively.
To successfully implement ZTA, fintech companies should:
Conducting a comprehensive risk assessment involves identifying and evaluating potential threats to the organization's assets and determining the likelihood and impact of each threat. This can help to prioritize security efforts and allocate resources effectively. Risk assessments should consider a wide range of factors, including the value of the assets being protected, the potential impact of a breach, and the likelihood of various types of attacks. Organizations can use risk assessment frameworks such as NIST's Risk Management Framework (RMF) or ISO/IEC 27005 to guide the assessment process.
Developing a clear Zero Trust strategy involves defining the organization's security objectives, policies, and procedures. This should include detailed guidelines for implementing and maintaining ZTA, as well as metrics for measuring success. A successful Zero Trust strategy should be aligned with the organization's overall business objectives and should include input from key stakeholders across the organization. The strategy should also be flexible enough to adapt to changing threats and technologies, ensuring that the organization remains secure as the threat landscape evolves.
Investing in training and awareness programs is crucial for ensuring that all employees understand their role in maintaining security. This can include regular security training sessions, phishing simulations, and awareness campaigns to promote a culture of security within the organization. Employees are often the first line of defense against cyber threats, and ensuring that they are properly trained can significantly reduce the risk of security incidents. Organizations should also provide specialized training for IT and security staff, ensuring that they have the skills and knowledge needed to implement and manage Zero Trust Architecture effectively.
Collaborating with cloud service providers is essential for ensuring that security practices are aligned and that both parties adhere to the shared responsibility model. This can involve regular security reviews, joint risk assessments, and the implementation of shared security controls. Cloud service providers offer a range of security tools and services that can help organizations implement Zero Trust Architecture more effectively. By working closely with their cloud providers, organizations can ensure that their security controls are properly integrated with the cloud environment and that any potential security gaps are identified and addressed.
The future of Zero Trust Architecture in fintech is promising, with advancements in AI and machine learning offering new ways to enhance security. As cyber threats continue to evolve, the Zero Trust model provides a robust framework for protecting sensitive financial data in the cloud.
Advancements in AI and machine learning are enabling new approaches to threat detection and response. These technologies can analyze vast amounts of data to identify patterns and anomalies that may indicate a security threat. Leveraging AI and machine learning can enhance the effectiveness of Zero Trust Architecture by enabling more accurate and timely threat detection. For example, machine learning algorithms can be used to detect subtle changes in user behavior that may indicate a compromised account or insider threat. AI-driven security tools can also automate routine tasks such as threat hunting and incident response, allowing security teams to focus on more strategic activities.
Zero Trust Architecture is not a one-size-fits-all solution. It requires continuous adaptation and improvement to address emerging threats and technological changes. Fintech companies must remain vigilant and proactive in their security efforts, leveraging the principles of Zero Trust to build a resilient and secure digital infrastructure. This requires a commitment to ongoing investment in security technologies, regular security assessments, and a culture of continuous learning and improvement.
Collaboration within the fintech industry is essential for addressing common security challenges and sharing best practices. Industry groups, regulatory bodies, and standards organizations can play a key role in promoting the adoption of Zero Trust Architecture and developing guidelines for its implementation. By working together, fintech organizations can develop more effective security strategies and share information about emerging threats and best practices. Collaboration can also help to drive the development of industry standards and frameworks, making it easier for organizations to implement Zero Trust Architecture and comply with regulatory requirements.
Regulatory compliance is an important consideration for fintech organizations implementing Zero Trust Architecture. Ensuring that security practices comply with relevant regulations and standards can help to mitigate legal and reputational risks. Regular audits and assessments can help to ensure ongoing compliance. In addition to industry-specific regulations such as PCI-DSS and GDPR, organizations must also consider broader cybersecurity regulations such as the NIST Cybersecurity Framework and the ISO/IEC 27001 standard. Compliance with these regulations not only helps to protect sensitive financial data but also enhances the organization's reputation and trustworthiness in the eyes of customers and partners.
Zero Trust Architecture offers a robust framework for enhancing security in cloud-based fintech applications. By adopting a "never trust, always verify" approach, fintech organizations can mitigate the risks associated with traditional perimeter-based security models and better protect sensitive financial data. However, implementing ZTA requires careful planning, collaboration, and continuous adaptation to address the evolving threat landscape. By following best practices and leveraging advancements in technology, fintech companies can build a resilient and secure digital infrastructure that supports innovation and growth [2-40].
